[German]Microsoft has been struggling with cloud outages in Exchange Online and Microsoft 365, including the iOS Outlook app, since March 1st, 2025. At the same time, I have just come across information about the CVE-2024-49035 vulnerability on the Microsoft Partner Portal. There are now indications that the Exchange Online issues could be related to a vulnerability. And there are suspicions that customers may have been compromised. I'll summarize some of the information that I see as pieces of the puzzle in a certain (unfortunately still incomplete) picture.
[German]Microsoft has been struggling with cloud outages in Exchange Online and Microsoft 365, including the iOS Outlook app, since March 1st, 2025. At the same time, I have just come across information about the CVE-2024-49035 vulnerability on the Microsoft Partner Portal. There are now indications that the Exchange Online issues could be related to a vulnerability. And there are suspicions that customers may have been compromised. I'll summarize some of the information that I see as pieces of the puzzle in a certain (unfortunately still incomplete) picture.
Cloud problems: What are they about?
Microsoft's cloud services have showing outages and issues since March 1, 2025. Outlook.com, the Outlook client (iOS), Microsoft 365 services and Exchange Online have been disrupted again and again. I first reported on these problems in the German article Microsoft 365 Störung (1. März 2025).
The first reader reports of problems arrived on my German blog as early as February 28, 2025 – see, for example, the German comments on the blog post Probleme beim Zugriff von Outlook auf Exchange Online-Postfächer. At that time, I didn't pay much attention to these reports.
But even on March 6, 2025, there are still disruptions (see Outlook also disrupted on March 6, 2025). Both the iOS mail app (confirmed by Microsoft several times) and the Samsung Android mail app (reported by German readers here and here, for example) are still unable to access Exchange Online mailboxes. This German comment also confirms massive problems accessing Exchange Online mailboxes with mail clients on different platforms.
In an early announcement, Microsoft had explained the disruption on March 1, 2025 with an "accidental update". Maybe, but I had doubts – given the ongoing disruption – whether that was all.
In the article Outlook also disrupted on March 6, 2025, I asked what the cause of this disruption was. One week of disruption seems unusual to me. That's why I explicitly asked the Microsoft Germany press department this week for a post-incident report for the disruption. But so far there is silence in the forest.
Strange observations from administrators
On Facebook, I received a reader comment from a German IT service provider on March 4, 2025 regarding one of my posts about the disruption (see screenshot below), which states that Exchange Online is no longer sending mails to its customers. The reason reported for these customers is "The mailbox doesn't exist".

Exactly this information has also been reported to me by other sources – where tenant administrators observed that the mailboxes of Exchange Online tenants were suddenly gone or the message "Mailbox being set up" appeared. This is also described in following German comment by Norbert P..
the shock at the beginning of the problems that all the tenant's mailboxes were gone was bad… then the message appeared: "We are setting up a mailbox…" (in the exo admin center)
This suggests (in my view) that something has happened across tenants at Microsoft and that mailboxes may be "restored" there. It also does not affect all tenants or all mailboxes of an Exchange Online tenant.
There was also a vague rumor that before the disruption reported on March 1, 2025, tenant administrators had received warnings that Exchange Online tenants were running out of storage space and quotas were being reached. It appears that the junk folder of the mailboxes of affected tenants has been flooded with SPAM. If the quota threshold is reached or exceeded as a result, the MS 365 package in question may no longer work.
Would be an explanation for me why those affected were no longer able to receive or send mails days before March 1, 2025. In the article Probleme beim Zugriff von Outlook auf Exchange Online-Postfächer from February 26, 2025, "strange error patterns" (also "mailbox moves" to other MS servers) are discussed, which make sense with the above information (something was deleted by Microsoft so that the mailbox works again). What all observations have in common is that it only affects individual tenants and/or mailboxes and that the faults can also "disappear".
The Dark Side of the Moon
In the spirit of the old Pink Floyd song "The Dark Side of the Moon", I'm going to take the story a little further and look at the dark side of the moon. I've just come across another observation that gives me some explanations, although I can't reveal everything (some of what I've heard in the last few days is still too vague, but something seems to be "up"). The canary I'm keeping here says: "No, Microsoft has not threatened me with legal action" till now. But Microsoft has so far remained silent in response to my request for an incident report and I think, Redmond could come out with details.
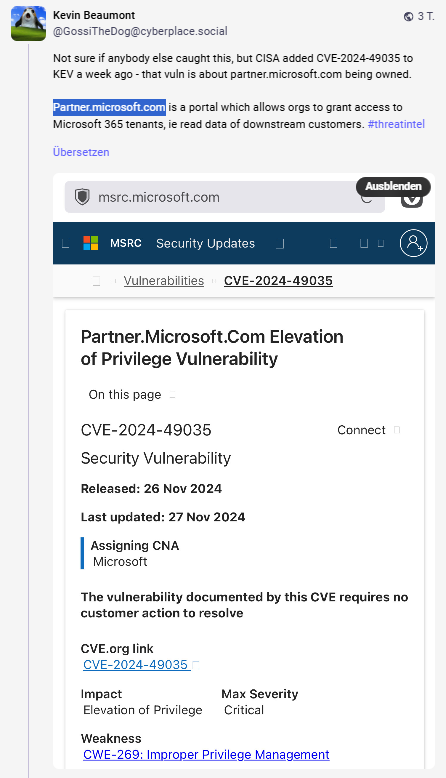
CVE-2024-49035 in the partner portal
A reader pointed me to a post by security researcher Kevin Beaumont on Mastodon – based on my blog posts on the above incident. In the following post, Beaumont writes that the US security authority CISA has added the vulnerability CVE-2024-49035 to the Known Exploit Vulnerabilities Catalog (KEV) (see here).
The vulnerability CVE-2024-49035 has been known at Microsoft for some time, and there was a publication on November 26, 2024. It is a privilege escalation vulnerability in the Microsoft partner portal partner.microsoft[.]com because input was not sufficiently validated. The vulnerability is classified as Critical (Score 8.7).
Microsoft writes that an access control vulnerability at partner.microsoft.com allows an unauthenticated attacker to escalate privileges over a network. And the vulnerability is also being exploited (although this was only "added" after the initial publication).
At the same time, the all-clear was given because this CVE only relates to a vulnerability in the online version of Microsoft Power Apps. According to Microsoft, customers do not need to take any action as the versions are automatically distributed over several days.
Just thinking out loud: There is a vulnerability that allows privilege escalation in the Partner Portal. Then the online version of the Microsoft Power Apps is patched, which allows exploitation. Question: Is the vulnerability now gone? Microsoft should provide clarification.
Did something get through after all?
Now we come to the dark part of the story. According to the Microsoft statement above, the vulnerability CVE-2024-49035 in the online version of Microsoft Power Apps has long since been mitigated. However, I have heard a rumor that something might not be kosher in this environment and that tenant administrators could possibly (unintentionally) influence other tenants.
According to Kevin Beaumont, the partner portal partner.microsoft.com deliberately allows Cloud Solution Providers (CSPs) to gain access to their customers' environments. In this post, he writes that insufficient input validation through the CVE-2024-49035 vulnerability opened up the possibility of accessing things that should not be accessed.
In the thread on Mastodon, participants write that the exploitation in the wild by Microsoft was only added later, i.e. after the initial publication of the article. The exploitation in the wild does not make the story any better.
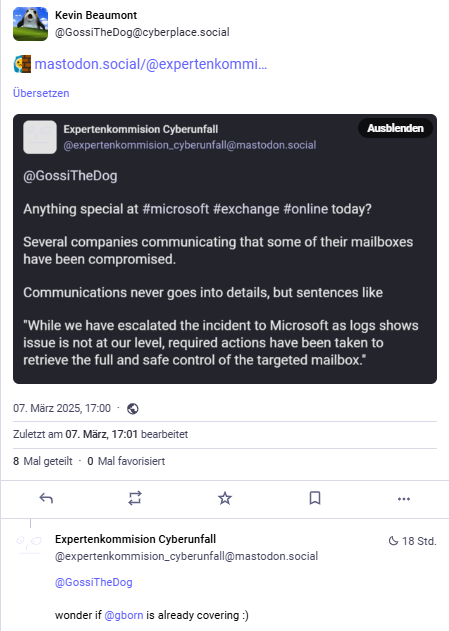
And then there's the following post on Mastodon where someone reports on the rumor that some companies believe their mailboxes have been compromised.
Above post states that these communications never went into detail, but sentences like "We have forwarded the incident to Microsoft as the logs show that the issue is not at our level. The necessary measures have been taken to regain full and secure control of the affected mailbox." would be dropped.
The ball is in Microsoft's court – it may be GDPR-relevant
The various pieces of the puzzle that I have found or received in various places fit the picture here. It seems to me that something has happened across Tenant. Microsoft can only create transparency here by fully disclosing the facts.
Incidentally, the matter has a special significance for administrators in the EU. If there is a vulnerability in Microsoft's cloud services (which I strongly assume based on the information I have so far) that enables Tenant-wide actions on Exchange online mailboxes, data protection officers would have to submit a report to the data protection authority within 72 hours.
Let's see if Microsoft reveals the cards regarding a particular incident in the coming days. I I wrote down a follow up article on an Exchange Online incident (affected tenants globally), that shall be published tomorrow. I've asked Microsoft for a statement, about what sources told me, a few days ago, but haven't got any feedback.