 [German]Security provider Check Point Research has published its ransomware report for the first quarter of 2025. In its latest State of Ransomware report, the security researchers at Check Point Research (CPR) report that the first quarter of 2025 saw a new high in the number of ransomware attacks reported by hackers.
[German]Security provider Check Point Research has published its ransomware report for the first quarter of 2025. In its latest State of Ransomware report, the security researchers at Check Point Research (CPR) report that the first quarter of 2025 saw a new high in the number of ransomware attacks reported by hackers.
In a nutshell
There has been a record-breaking increase in ransomware incidents: In the first quarter of 2025, the number of companies disclosed by hackers worldwide rose by 126 percent to 2289 victims. This is the highest figure ever recorded. Even without the mass casualties of the Cl0p ransomware gang, the number of incidents remains at a historically high level.
Cl0p ransomware group dominates with supply chain attacks. The Cl0p group became the most active ransomware group, exploiting zero-day vulnerabilities in Cleo file transfer products, with 83 percent of their victims based in North America, but also affecting companies in Germany.
Another thing I have also noticed is that there is an increasing number of false victim reports from the various cyber groups, which makes the situation more difficult to understand. Groups such as Babuk-Bjorka and FunkSec are increasingly spreading fake or recycled victim reports, which obscures the actual threat situation and creates new challenges for cyber defense in Germany and worldwide.
Translated with DeepL.com (free version)
1. Q 2025: record-breaking increase
Ransomware remains one of the most persistent and damaging cyber threats to businesses worldwide. The first quarter of 2025 saw an unprecedented increase in activity, with 74 different ransomware groups publicly reporting victims on data leak sites (DLS). These groups report a total of 2289 victims – more than twice as many as in the same period last year, when 1011 cases were published. This corresponds to an increase of 126 percent compared to the previous year.
If you deduct the 300 victims attributable to the mass disclosure of Cl0p in February 2025, which was linked to the exploitation of the Cleo file transfer platform, the figures remain historically high. The adjusted monthly average is over 650 victims, compared to around 450 per month for the whole of 2024.
Including Cl0p, the average for Q1 rises to 760 per month, setting a new high for ransomware activity (Q1 average visualized in Figure 1).the Cl0p ransomware group dominates with supply chain attacks. The Cl0p group became the most active ransomware group, exploiting zero-day vulnerabilities in Cleo file transfer products, with 83 percent of their victims based in North America.
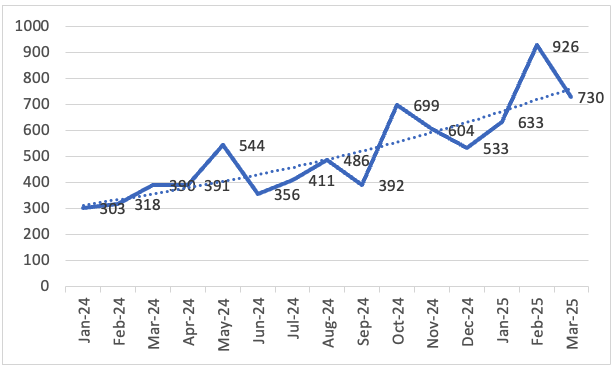
Figure 1 – Total number of reported ransomware victims on data leak sites per month (Check Point Software Technologies Ltd.).
This sharp increase may reflect a growing trend among threat actors to exaggerate the scale of their attacks. This includes the falsification of victim data to feign greater reach and intimidate potential future targets.
At the same time, it should be noted that companies that pay ransoms quickly are usually excluded from publication on leak sites, suggesting that figures published in the past may have significantly underrepresented the true scale of ransomware incidents.
The most active ransomware groups in Q1 in order of publicly disclosed victims were Cl0p, Ransomhub and Babuk-Bjorka. However, a large proportion of the attacks are spread across smaller groups, which are subsumed under the "Other" category (Figure 2).
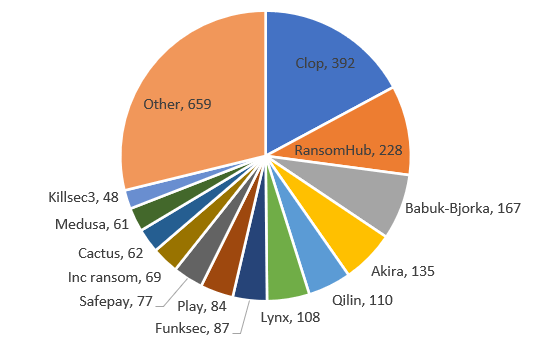
Figure 2 – Ransomware groups by alleged victims – Q1 2025 (Check Point Software Technologies Ltd.) The most active ransomware groups in Q1 by publicly disclosed victims were Cl0p, Ransomhub and Babuk-Bjorka. However, a large proportion of the attacks are spread across smaller groups, which are subsumed under the "Other" category (Figure 2).
Cl0p: Encryptionless attacks; focus on supply chains
With 392 publicly named victims, Cl0p was the most active ransomware actor worldwide in the first quarter of 2025. The group continues to focus on encryption less attacks and instead concentrates on data exfiltration and extortion. It uses waves of zero-day vulnerabilities in widely used third-party platforms to compromise service providers and then access customer data.
Following previous high-impact campaigns, such as GoAnywhere in early 2023 and MOVEit in mid-2023, Cl0p's activity in 2025 was primarily driven by the exploitation of Cleo-managed file transfer products Harmony, VLTrader and LexiCom – an attack responsible for more than 300 Cl0p disclosures in the first quarter.Figure 3 – Ransomware victims by country, Q1 2025 (Check Point Software Technologies Ltd.).
A closer look at the victim data by country shows that some ransomware groups have clear geographical preferences. In the UK, for example, the Medusa ransomware group is disproportionately active – accounting for more than nine percent of reported victims, compared to just two percent of victims globally. This indicates a targeted strategy or a stronger operational foothold in the region.
The sector distribution of ransomware victims in the first quarter of 2025 also reflects a typical cross-industry nature, with no one industry particularly affected.
RansomHub as a rising force after LockBit
RansomHub emerged in February 2024 and has positioned itself as one of the dominant ransomware groups, publicly naming 228 victims in the first quarter of 2025 alone. The rapid rise of RansomHub follows the disruption of LockBit's operations by law enforcement in early 2024, filling the vacuum left by one of the most established ransomware-as-a-service (RaaS). RansomHub has distinguished itself through an aggressive partner recruitment strategy that relies on a favorable profit-sharing model.
The distribution of victims mirrors general trends in the ecosystem: US-based companies account for approximately 59 percent of reported cases, which is consistent with the general pattern in the ransomware landscape.
Babuk-Bjorka: reputation building through recycled victims
Babuk-Bjorka ranked third in Q1 2025, claiming 167 victims since its emergence earlier this year. The group positions itself as a revival of the original Babuk ransomware operation, which ceased its activities in 2021 after its source code was leaked. However, there is no evidence of a link between Babuk-Bjorka and the original group. It is more likely that the new player is using the Babuk name to attract media attention and partners under a RaaS model.
In January alone, Babuk-Bjorka reported an eye-catching 68 victims, but further analysis revealed that many of these were duplicates of incidents previously attributed to other ransomware groups.
FunkSec: AI-driven malware and unclear motivation
FunkSec, a ransomware group that emerged in December 2024, is an example of several evolving trends in the ransomware ecosystem. Since its emergence, the group has claimed responsibility for more than 170 attacks, although the credibility of these claims remains uncertain.
Research by Check Point Research suggests that FunkSec's malware was likely developed using AI tools – an approach that allows for customization and refinement even without advanced technical knowledge. This use of AI significantly lowered the barrier to entry for cyber criminals, enabling the deployment of sophisticated ransomware by relatively inexperienced individuals.
In addition to questions regarding the legitimacy of its claims on previous victims, FunkSec complicates attribution because it operates at the intersection of hacktivism and financially motivated crime, making it difficult to reliably assess its underlying motives.
The report is available at The State of Ransomware in the First Quarter of 2025: Record-Breaking 126% Spike in Public Extortion Cases.



