 [German]Law enforcement officials seize Lumma Stealer infrastructure (May 2025)In a coordinated operation, US law enforcement officials have seized the infrastructure (C & C servers) of the Lumma infostealer and paralyzed its function. The malware is responsible for numerous cyberattacks on users involving the interception of information and almost 400,000 PCs were infected.
[German]Law enforcement officials seize Lumma Stealer infrastructure (May 2025)In a coordinated operation, US law enforcement officials have seized the infrastructure (C & C servers) of the Lumma infostealer and paralyzed its function. The malware is responsible for numerous cyberattacks on users involving the interception of information and almost 400,000 PCs were infected.
What is Lumma Stealer?
Lumma Stealer (also known as LummaC2 Stealer) is a malware written in C that harvests data from victims' systems (Infostealer). According to this source, the malware has been offered via a malware-as-a-service (MaaS) model in Russian-language forums since at least August 2022.
It is believed to have been developed by the threat actor "Shamel", who also operates under the pseudonym "Lumma". Microsoft refers to the actor offering Lumma as malware-as-a-service (MaaS) as Storm-2477.
Partners who pay Storm-2477 for the service and run their own Lumma campaigns are given access to a panel to create the malware binary and manage C2 communications and stolen information. Microsoft states that ransomware threat actors such as Octo Tempest, Storm-1607, Storm-1113 and Storm-1674 are using the Lumma Stealer in campaigns.
The Lumma Stealer primarily targets cryptocurrency wallets (digital wallets) and browser extensions with two-factor authentication (2FA). If the infection succeeds, the malware steals sensitive information from the victim's computer.
In contrast to earlier Infostealers, which relied on mass spam or exploits for distribution, the Lumma Stealer uses different distribution strategies. Operators are resourceful and the Lumma Stealer distribution infrastructure is flexible and adaptable. Operators are constantly refining their techniques by rotating malicious domains, exploiting ad networks, and using legitimate cloud services to evade detection and maintain operational continuity. This dynamic structure allows operators to maximize the success of their campaigns while making it difficult to trace or dismantle their activities.
If an infection succeeds, the malware attempts to obtain sensitive data (from crypto wallets etc.). Once the targeted data has been read by Lumma, it is exfiltrated to a C2 server via HTTP POST requests using the user agent "TeslaBrowser/5.5". The stealer also has a non-resident loader that can provide additional payload data via EXE, DLL and PowerShell.
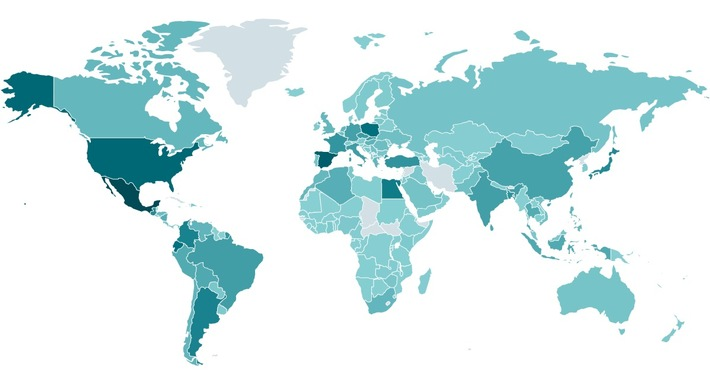
Lumma infections worldwide (source: ESET)
The malware has been one of the most widespread infostealers worldwide over the past two years. The chart above, published by ESET, shows the infection levels in individual countries. The USA, Mexico, Spain and Poland in particular stand out with high infection rates. However, the coloring is deceptive – I have seen maps that show a high infection rate for Europe. In total, over 394,000 PCs worldwide were probably infected with the malware.
Lumma infrastructure dismantled
With the help of Microsoft and ESET, US law enforcement authorities were able to analyze the structures of the Lumma Stealer and then seize the Command & Control (C&C) servers in a worldwide operation.
Microsoft and ESET analyze infrastructure
Over the past few years, security vendor ESET has automatically analyzed tens of thousands of Lumma Stealer samples to extract key elements such as C&C servers and affiliate identifiers. This has allowed them to continuously monitor Lumma Stealer activity, track development updates, cluster affiliates and much more. ESET has published an article ESET takes part in global operation to disrupt Lumma Stealer with more details and a technical analysis.
Further analysis of Lumma Stealer activities and infrastructure was conducted by the Microsoft Digital Crimes Unit (DCU), which published its findings on May 21, 2025 in the blog posts Lumma Stealer: Breaking down the delivery techniques and capabilities of a prolific infostealer and Disrupting Lumma Stealer: Microsoft leads global action against favored cybercrime tool.
On Tuesday, May 13, Microsoft's DCU filed a lawsuit against Lumma Stealer ("Lumma") in a U.S. court. The lawsuit argued that action should be taken against the malware because Infostealer, which is favored by hundreds of cyber threat actors, steals passwords, credit card data, bank account data and cryptocurrency wallets. This allowed cybercriminals to blackmail schools, drain bank accounts and disrupt critical services.
Between March 16, 2025 and May 16, 2025, Microsoft identified over 394,000 Windows computers worldwide that were infected with the Luma malware. Through a court order from the United States District Court of the Northern District of Georgia, Microsoft's DCU seized and enabled the blocking of approximately 2,300 malicious domains that formed the backbone of the Luma infrastructure.
The Department of Justice (DOJ) simultaneously seized Lumma's central command structure and disrupted the marketplaces where the tool was sold to other cybercriminals. Europol's European Cybercrime Center (EC3) and the Japanese Cybercrime Control Center (JC3) assisted in shutting down the local Lumma infrastructure.
This was done in collaboration with law enforcement agencies (FBI, Europol, JC3) and industry partners (ESET, Bitsight, Lumen, Cloudflare, CleanDNS, and GMO Registry). Microsoft claims to have interrupted the communication between the Lumma Stealer on the victims' systems and the operators' C&C servers.
More than 1,300 domains seized by Microsoft or transferred to Microsoft, including 300 domains seized by law enforcement agencies with the assistance of Europol, were then redirected to Microsoft sinkholes. In this way, Microsoft's DCU can provide actionable intelligence to further improve security measures.
Details on the campaign and the findings from the analyses carried out can be found in the articles from Microsoft, ESET and other partners linked in the text above. A German-language press release from Microsoft can be accessed here. The press release from the US judiciary is available here.
Parts of the infrastructure have survived
Addendum: Subsequently, I received additional information from Check Point that although the law enforcement agencies have shut something down, parts of the infrastructure have survived. Under the title "Infostealer Lumma not yet taken down", Check Point Research (CPR) informed me of new developments following the high-profile takedown of the Infostealer Lumma by Europol, the FBI and Microsoft. While the operation seized thousands of domains and cut off access for Lumma users, the security researchers warn that Lumma is down, but not out.
Law enforcement agencies have penetrated the backend of Lumma, deleting backups via a vulnerability in Dell's iDRAC and planting phishing pages to grab user data and even attempt to access the webcam.
In a detailed blog with Darkweb quotes and evidence, CP shows: parts of Lumma's infrastructure hosted in Russia survived the takeover – and the operators are already in the process of rebuilding operations.
New stolen credentials from Lumma continue to be offered for sale, with the number of logs increasing rapidly just days after the operation. According to Check Point, this indicates that those behind the operation are trying to revive Lumma's business model.
The real battleground may now be psychological, as the authorities seek to destroy trust between Lumma's operators and their criminal customers. "This is not just a technical attack, but a war for image," says Sergey Shykevich, Threat Intelligence Group Manager at Check Point. "Lumma's developers are trying to pretend that business is normal, but confidence in the malware-as-a-service underworld is fragile. The next few weeks will be crucial." Check Point has published the new findings in this blog post.




