[German]Since October 4, 2025, security experts at Huntress have observed a sharp increase in compromised SonicWall SSLVPN instances. The nature of the attacks and the speed with which the attackers penetrate the systems suggest that they have valid login credentials.
[German]Since October 4, 2025, security experts at Huntress have observed a sharp increase in compromised SonicWall SSLVPN instances. The nature of the attacks and the speed with which the attackers penetrate the systems suggest that they have valid login credentials.
The cloud backup incident
SonicWall recently experienced a security incident in which backup files of the firewall configuration were exposed. Unauthorized persons were able to view this information via the Internet. SonicWall disclosed the incident on September 17, 2025, in the support article MySonicWall Cloud Backup File Incident. I reported on this in the blog post MySonicWall Cloud Backup File Incident: Configuration backup disclosed.
It is now known that all customers who have used MySonicWall Cloud Backup are affected by this incident (see MySonicWall Cloud Backup File Incident: All customers affected). It is also known that the ransomware group Akira can hack SonicWall VPN accounts and bypass MFA security (see Akira hacks SonicWall VPN accounts (even those with MFA protection)). This serves as a preliminary remark to the following sections.
Attacks on SonicWall SSLVPN instances
Security provider Huntress has been observing a campaign of successful attacks on SonicWall SSLVPN instances since October 4, 2025, which continued until October 10, 2025. This is evident from the following tweet dated October 11, 2025.
The attackers quickly authenticate themselves across different devices, leading Huntress to conclude that valid login credentials are being used and that the compromise is not the result of brute force attacks.
- As of October 10, 2025, over 100 SSLVPN accounts have been compromised.
- Sixteen organizations have been affected by these successful attacks.
- The activities began on October 4, 2025, from the IP address: 202.155.8[.]73
Some passive accesses were observed. Other activities included scans and access to Windows accounts.
What administrators can do
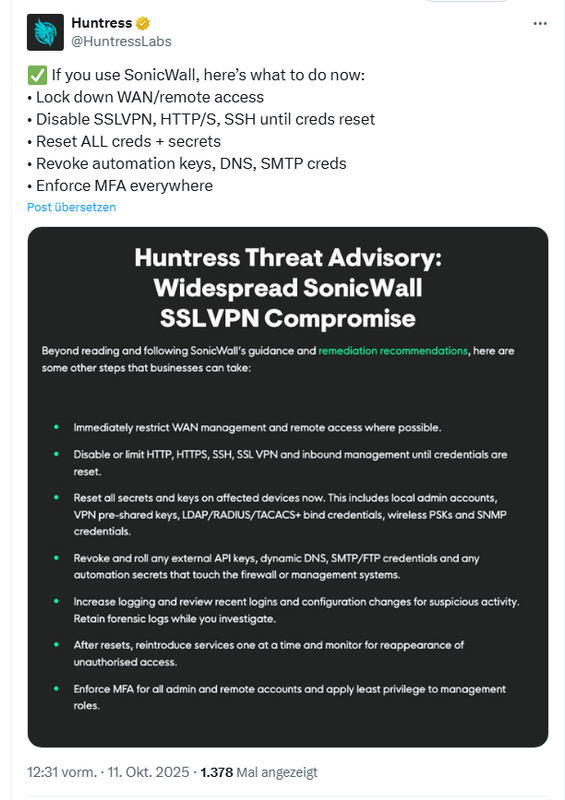
In the following tweet, Huntress provides some advice on what administrators of SonicWall SSLVPN instances should do urgently. This includes the following measures:
- Block WAN/remote access
- Disable SSLVPN, HTTP/S, and SSH until login credentials are reset
- Reset ALL login credentials + secrets
- Revoke automation keys, DNS, and SMTP login credentials
- Enforce MFA everywhere
And log files should be checked for suspicious activity. Huntress has published this article on the subject. The article here also picks up on the idea that the attackers were able to deduce the access data from the backups and are now exploiting it.
A reader feedback about a bad observation
Addendum: Shortly after the article was published, a German blog reader contacted me by email and wrote: "I would like to add one more fact to the article that causes me great unease." One of his customers is directly affected (to the extent of total encryption, he says). What bothers the blog reader about the gateway, i.e., the "SonicWall backup disaster," is the following.
SonicWall provides instructions on how to use cloud backup: How can I create cloud backup of SonicWall settings? The reader writes that for most of the customers the company supports, the switch was set to active. However, no active backup was ever set up (i.e., the Create Backup -> Cloud Backup option was never used). The local web interface also did not show any backups for these customers.
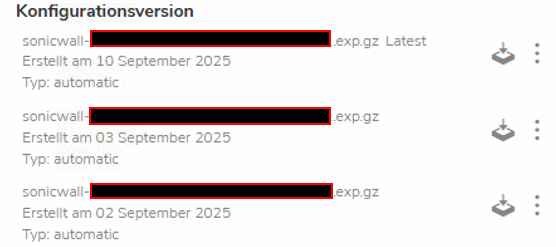
A look at the MySonicwall portal and the device under the Cloud Backups tab shows a different picture (see screenshot above). There you will find backups created for the various devices. The reader wrote that these entries appear with the same date for all firewalls. After that, nothing else was displayed in the list.
For the reader and their employer, the question now arises: if no task has been set up, how were all SonicWall instances apparently instructed centrally to create a backup and upload it to the cloud? The reader concludes: There is currently a feeling that not everything has been disclosed (knowingly or unknowingly).
Similar articles:
MySonicWall Cloud Backup File Incident: Configuration backup disclosed
Akira hacks SonicWall VPN accounts (even those with MFA protection)
Early termination of support for SonicWall SMA100
Warning of attacks on SonicWall firewalls (SSL VPNs)
MySonicWall Cloud Backup File Incident: All customers affected