 [German]Administrators use an unattend.xml file to install and set up Windows. The unattend.xml file can be created using a generator. A blog reader already pointed out to me in July 2025 that using an unattend.xml file in Windows 11 24H2 causes a security issue. Here is an overview about that topics.
[German]Administrators use an unattend.xml file to install and set up Windows. The unattend.xml file can be created using a generator. A blog reader already pointed out to me in July 2025 that using an unattend.xml file in Windows 11 24H2 causes a security issue. Here is an overview about that topics.
What are answer files (unattend.xml)?
Windows can be installed unattended and configured in the default settings using answer files (unattend.xml). These are .xml files that contain instructions for unattended installation. Windows Setup automatically searches for answer files in specific locations, or administrators can specify a file to use for unattended installation by using the /unattend: option when running Windows Setup (setup.exe).
For a complete list of response file settings (also known as unattended installation settings), see the Windows Unattended Installation Reference.
An unattend.xml generator
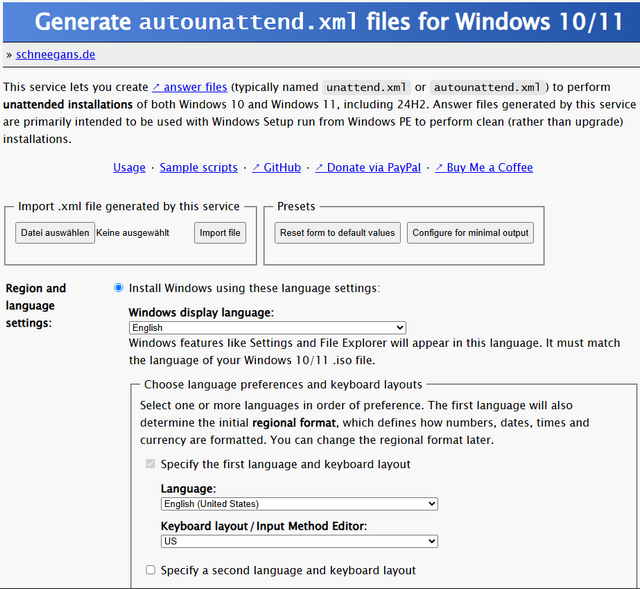
Christoph Schneegans has provided a generator for creating unattend.xml files on the Internet at site Generate autounattend.xml files for Windows 10/11.
There, you can interactively select the desired parameters for the Windows installation in forms and generate the unattend.xml file.
Windows 11 24H2: Security issue caused by unattend.xml
A blog reader contacted me by email in mid-July 2025 and pointed out a security issue with unattend.xml in Windows 11 24H2 that he had encountered. He wrote to me: "I am contacting you to draw your attention (if you are not already aware) to what I believe to be a critical issue that primarily affects businesses."
It concerns the behavior of a Windows 11 24H2 installation when it is performed via unattend.xml, i.e., automatically using the XYZ deployment tool. Since Windows 11 24H2, after installation the folder
C:\Windows\Panther\
two copies of this unattend.xml file are stored. The problem is that the "unattend.xml" file contains the administrator username created during installation in plain text (which, according to the reader, is bad enough, as administrator rights are not required to read this file).
The reader wrote that during installation, the "built-in" administrator is often disabled by an unattend.xml file in accordance with MS best practice. At the same time, an account for a local administrator is created.
The name of this administrator account then appears in the unattend.xml file. Furthermore, the second saved "unattend-original.xml" file contains not only the local administrator name but also their password in plain text.
This means that companies that automatically set up clients with Windows 11 24H2 and do NOT change or customize the local administrator password, e.g., via LAPS, have a blueprint for the spread of a worm or worse located at C:\Windows\Panther\.
The obvious solution at this point is to delete these two files using a software distribution tool/GPO. The reader wrote: If you search the internet for "unattend-original.xml," you will currently find very little material, so I am not sure how critical this topic is. I have therefore posted the information here in the blog—thanks to the reader for the tip.




When using Windows System Image Manager (from the WAIK Kit), passwords in the xml file can be encrypted or unencrypted, depending on the administrator's choice.
I will not comment on third-party sites that generate xml files because I have never used them, but complaining about unencrypted passwords in this file is like complaining that everyone knows your password after you stuck card with it on your monitor.
In my case unattend.xml in C:\Windows\Panther after MDT deployment says:
Username mdt_join /Username
Password *SENSITIVE*DATA*DELETED* /Password
Of course in XML format but that will be stripped here…
So admin passwords seems to be removed.
Unfortunately not in all cases, as my German blog readers told me. So the message of the article is: "keep it on your watchlist".