![]() [German]The Chinese online shopping platform Gearbest has more than 199 million visitors per month and is probably well known to many users. Security researchers have found that the databases of Gearbest and a number of other online shops of the Chinese parent company are unprotected and may be reached from the internet. The Chinese gigant don't seem to be interested in evidence to improve security. Addendum: A statement from Gearbest is available. Explanation: firewalls were switched off and data is stored unencrypted for max. 3 days for test purposes. Details at end of article.
[German]The Chinese online shopping platform Gearbest has more than 199 million visitors per month and is probably well known to many users. Security researchers have found that the databases of Gearbest and a number of other online shops of the Chinese parent company are unprotected and may be reached from the internet. The Chinese gigant don't seem to be interested in evidence to improve security. Addendum: A statement from Gearbest is available. Explanation: firewalls were switched off and data is stored unencrypted for max. 3 days for test purposes. Details at end of article.
Security reaearcher from vpnMentor contacted me and shared their findings. Their security researcher and white hat hackers came across the unbelievable data privacy scandal. My contact at vpnMentor describes it this way:
I wanted to let you know about a HUGE data breach our ethical hackers found last week. It impacts millions of people every day, all around the world. You or one of your loved ones could be affected.
We just published a report which describes how we found that Gearbest (which has over 199 million monthly visitors), as well as many other famous clothing e-commerce stores, has a completely open and accessible database. People's private information, including email addresses, phone numbers, addresses, passwords, payment details, and orders are open to the public.
I believe BornCity's readers will be interested in this story if you decide to share it with them.
Who is Gearbest
With hundreds of thousands of sales per day, Gearbest is a very successful Chinese e-commerce company. The platform sells electronics and appliances, clothing, accessories and household goods in more than 250 countries worldwide. While it sells some internationally known brands such as OnePlus (SmartPhones), most products come from smaller Chinese brands. GearBest ranks among the top 100 websites in a good 30% of target countries, partly because the Chinese have set up subdomains for 18 languages (including German).
Gearbest belongs to the Chinese conglomerate Globalegrow. The parent company operates several internationally successful locations, including Zaful, Rosegal and DressLily. In 2015 its turnover reached 550 million dollars; in 2017 the company celebrated a turnover of 1.48 billion dollars. So it was a resounding success for the company and its subsidiaries. I regularly receive e-mails here, but I would like to present this or that product in my blog, but I have refrained from doing so because the topic was too shaky for me for various reasons.
Gearbest's privacy statements
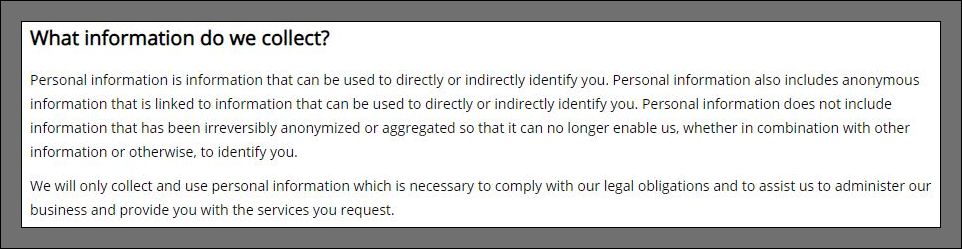
The current case raises some fundamental questions as to whether and how data protection and privacy can plays a role in Chinese companies at all. You simply have to see the context in which those responsible operate. Gearbest's privacy statements state that they collect and store user information for the purpose of communicating and processing orders with customers.
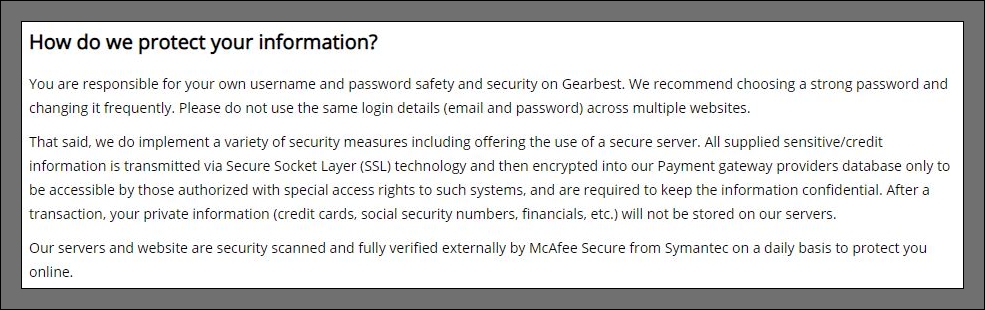
However, the privacy statement also states that users are responsible for their own passwords. But Gearbest states that sensitive information is transmitted via SSL and stored encrypted in the payment provider gateway. Payment information (credit cards, etc.) should not be stored on their Gearbest servers. Access to the data was restricted to authorized users and McAfee external AV software was used to protect customers. Here is the explanation.
The reality check prove that's wrong
That privacy statement sounds very good in theory. But vpnMentor's Whithe Hat hackers discovered that Globalegrow's entire database is unprotected and mostly unencrypted. The company uses an Elasticsearch database, which is usually not designed for URL use. However, hackers were able to access it through a browser and manipulate URL search criteria to display up to 10,000 schemas from a single index at any time. The data available to vpnMentor's Whithe Hat hackers shows that the above explanations are just paperwork. The hackers has been able to access a lot of sensitive information – including email addresses and passwords – that was completely unencrypted.
Within this vpnMentor report the security researchers are now revealing their findings. Noam Rotem has discovered that through an open database, the personal information of individuals, including email addresses, phone numbers, addresses, passwords, payment information and orders, is publicly available. Hackers could access various parts of the Gearbest database, including:
- Orders database: Data includes products purchased; shipping address and postcode; customer name; email address; phone number
- Payments and invoices database: Data includes order number; payment type; payment information; email address; name; IP address
- Members database: Data includes name; address; date of birth; phone number; email address; IP address; national ID and passport information; account passwords
The security researchers accessed these databases in March 2019 and found over 1.5 million records. Gearbest's database is not only insecure, it also provides potential attackers with a constantly updated source of new user data. In addition, the Gearbest database contains large amounts of personal information that is not required to perform the functions of an e-commerce shop. For example, a delivery address is crucial for fulfilling orders, but an IP address is not.
Aside from the ability for third party actors to access complete sets of personally identifiable information for millions of users, Gearbest's data breach raises several other very serious issues.Within their report, the security researchers from vpnMentor show what kind of data is public and what risks this entails. This reaches from identity theft up to be confronted with sensitive data (like sex toys ordered from this vendor, which may be a criminal act in some countries). Also payment information can be mis-used by cyber criminals.
The security researchers have uncovered something else. Gearbest does not only store millions of user data openly in a database. The hackers also got access to the URL of the Kafka system from Gearbest and Globalegrow. Kafka is a data management program that helps large companies control the amount of location data sent through each of their servers. This serves two purposes: it prevents server overload (enables load balancing) and allows companies to collect large amounts of data.
This type of access allows malicious hackers to manipulate information, reassign database properties, and even disable entire areas of the company's server. Depending on the function of each server, this can disrupt data collection, order placement, inventory and warehouse management.
The security researchers have repeatedly contacted both Gearbest and Globalegrow to inform them of this privacy violation. It was also announced that vpnMentor would publish an article. Despite a set deadline and repeated attempts to ask these companies to improve security, all approaches were unsuccessful. At the time of publication, vpnMentor had no answers vom Globalegrow or Gearbest.
Addendum: Gearbest's statement and explanation
In the meantime Gearbest has issued a statement, AndroidPolice has published it here.
mmediately upon being aware of this incident, our security experts have initiated an investigation to verify the allegations made by Mr. Noam Rotem. While we found that all our own established databases or servers used for storing or processing Data are protected with all necessary encryption measures and are absolutely safe, some of the external tools we use to temporarily store Data may have been accessed by others and therefore Data security may have been compromised.
The external tools we use are intended to improve efficiency and prevent data overload and the Data will only be stored in such tools for less than 3 calendar days before it is automatically destroyed. Considering possible data security breaches, we protected those tools with powerful firewalls to avoid any such data being compromised by malicious scanning from others. However, our investigation reveals that on March 1st, 2019, such firewalls were mistakenly taken down by one of our security team members for reasons still being under investigation. Such unprotected status has directly exposed those tools for scanning and accessing without further authentication.
Currently, we believe this may have affected our newly registered customers as well as our old customers who placed orders with Gearbest during the time from March 1st 2019 to March 15th, 2019, in a total number of about 280,000. Fortunately, the irregularity has been fixed by us within two hours immediately after detecting it and we will further strengthen our internal security management to avoid such incident from happening again.
We truthfully apologize for what happened. In addition to what we have done mentioned above, we will be urgently carrying out measures to inactivate the passwords of those newly registered customers for avoidance any illegal login to their accounts and will also send email to all affected customers for updating the situation.
Well, the message behind the statement may be read in a different was. Obviously it's possible, that staff may remove certain security measures can be taken without authorization and without documentation. Moreover, this statement contradicts vpnMentor's statements that it found the open database in March 2019 and contacted Gearbest multiple times. There was no reaction, until the reports the data break has been published on 14/15 March 2019. The question I'm asking: As a first step, the company declares in its privacy policy that everything is encrypted and protected from unauthorized access. And then the data is temporarily stored unencrypted to access it with test tools (even if only for 3 days). In other words: Internal staff can access this unencrypted data and, if necessary, pass it on or 'lose' it. Not trustable in my opinion.