![]() Security experts from Bleeping Computer has found a new Malware, named RAA, that is using JScript. The Malware behaves as Ransomware and encrypt user files – but there is also a 2nd payload, a Trojan, that will be installed on victims computers. Here are a few information about this malware – explaining also, why several internet articles are wrong or inaccurate. And there is a cure against such infections.
Security experts from Bleeping Computer has found a new Malware, named RAA, that is using JScript. The Malware behaves as Ransomware and encrypt user files – but there is also a 2nd payload, a Trojan, that will be installed on victims computers. Here are a few information about this malware – explaining also, why several internet articles are wrong or inaccurate. And there is a cure against such infections.
The message about RAA malware has been spread widely within the internet. What took my attention, was the fact, that many articles are writing about a malware entirely written in JavaScript – which isn't accurate. You can find such an article New ransomware variant coded entirely on Javascript, exploits macros at neowin.net for instance. Therefore I read the original article The new RAA Ransomware is created entirely using Javascript at Bleeping Computer. Well, although the head line was wrong, the article itself named the facts widely accurate.
What does the malware?
In brief: A user receives an e-mail with an attachment mgJaXnwanxlS_doc_.js – that looks like "a DOC file", if the user has disabled showing file type extensions (disabled by default in Windows), and if the user isn't too much experienced and don't know the difference between mgJaXnwanxlS_doc and mgJaXnwanxlS.doc. Double clicking the attachment executes the script, which provides the following thing:
- Files (documents) will be encrypted
- A trojan named Pony will be unpacked and installed – Pony tried to obtain passwords
- The ransomware adds an entry at the registry key HKCU\Software\Microsoft\Windows\CurrentVersion\Run
to establish an autorun each time a user logs in. - A fake "Word" file containing Russian text will be displayed
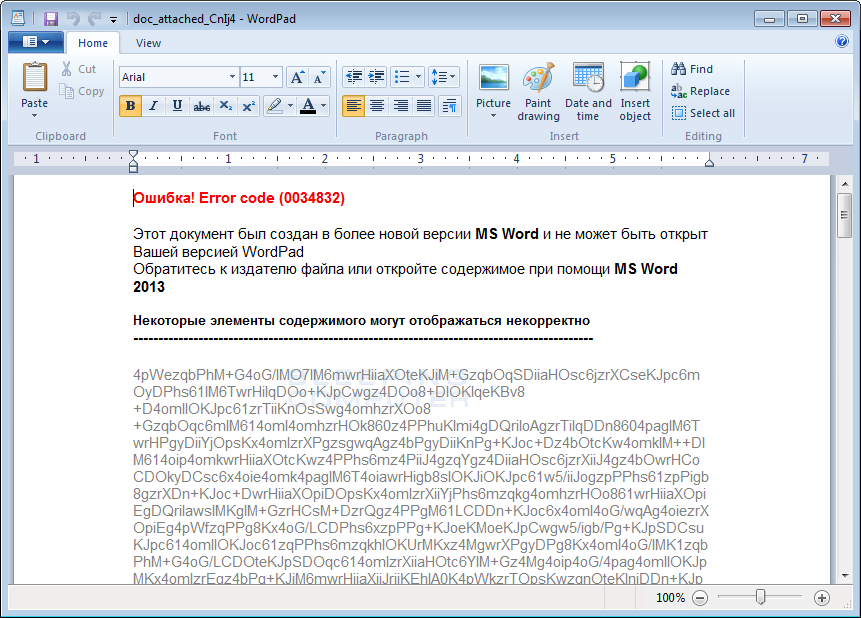
(Source: Bleepingcomputer.com)
The fake document will be displayed in WordPad – goal is, to focus the user's attention onto this document – let him thinking the document is broken. In Background the malware starts its encryption. Bleeping Computer writes the disc will be searched for files and documents will be AES (Advanced Encryption Standard) encrypted using the crypto-js library. All encrypted document files are renamed to a .locked file. After finishing that process, the malware generates an .RTF file on the users desktop, demands for ~250 US Dollar to get the files back.
The problem: Non accurate wording in many internet articles
Although the Bleeping Computer article The new RAA Ransomware is created entirely using Javascript describes the details correctly, the title is extremely misleading. So the neowin.net head line New ransomware variant coded entirely on Javascript, exploits macros is even more misleading, because the message between the lines within the article:
- The malware is entirely written in JavaScript (associates it should be executed within a browser, and may be platform independent)
- Comes as e-mail attachment (.JS file) and encrypts document files using a crypto library (which is correct)
- Deletes volume shadow copies (VSS), to old file versions can't be recovered
- Comes with a Trojan payload to harvest passwords – and the ransom ware demands for payment fro unencrypting the documents
While the above topics are not completely wrong, naming JavaScript (that is executed within a browser) points people to the wrong direction. I read many comments, that using NoScript as a browser option will block this malware.
A few corrections
Reading the orignal article at Bleeping Computer gives you a clue, what happens. Here is the text:
RAA is distributed via email with an attached Javascript (.JS) file. When a victim double-clicks on this JS file, Windows will execute the default program associated with javascript files. By default, this is the Windows Script Host or wscript.exe.
The text snipped indicates that the .JS file will be executed within Windows Script Host (WSH). But using the term JavaScript is completely wrong. A .JS attachment isn't a JavaScript on Windows machine and won't be executed within a browser! Instead it's a JScript file, that will be executed in Windows Script Host (WSH). This is a fundamental different thing.
A JScript script executed within the context of a user account just has default user credentials. So RAA can search only files accessible from the user account (and not the whole disk). On a good administrated system, only local user profile files and some files commonly used are accessible.
Also deleting volume shadow copies (VSS) isn't possible with default user credentials. A WSH script needs administrative credentials to delete VSS entries. This means, the user account control has to be used to obtain admin privileges.
How to block JS attachments from execution?
Admins should set up a system in a way, that the malware can't be executed. By default, users shall work with default user accounts, coming with restricted privileges. An admin account should be used only, if executing an administrative task won't run, using the UAC prompt (there are a few rare cases, where login to an Admin account is mandatory). If default users don't know the admin password, the damages from malware is restricted to the user files.
A second task should be blocking WSH files from execution. Microsoft has published this article mentioning the registry entry to block WSH script execution. Navigate to the registry key:
HKEY_CURRENT_USER\Software\Microsoft\Windows Script Host\Settings\
and add a DWORD value Enabled=0 blocks the execution of .VBS and .JS files on user accounts, so a .JS e-mail attachment will be useless. This has been mentioned within the Bleeping Computer article.
Only a environment within a domain could be a problem, if login and logoff scripts has to be executed on client machines. Disabling WSH for the whole machine (see) is also an option, but could cause trouble, because some system scripts won't run anymore. Microsoft has published this Technet article, describing, how to restrict exception to signed WSH scripts, which could be a possible solution.
As a conclusion: There are ways to block such malicious .js attachments. And don't believe any internet article claiming something is written in JavaScript and does something on your client machine. Maybe some admins has further thoughts how to block such malicious payloads.



