![]() Currently a new variant of Petya ransomware (aka PetyaWrap, aka NotPetya) are infecting companies and organisations (see Petya ransomware is back – using WannaCry vulnerabilties). First analyses indicating, that this ransomware not only broke infected systems. There are indications, that the malware also steals user credentials. There are also hints, that spreading the malware via networks isn't restricted to unpatched SMBv1 vulnerabilities. And there is hope, that a kind of Killswitch/vaccine has been found to protect a machine from encryption.
Currently a new variant of Petya ransomware (aka PetyaWrap, aka NotPetya) are infecting companies and organisations (see Petya ransomware is back – using WannaCry vulnerabilties). First analyses indicating, that this ransomware not only broke infected systems. There are indications, that the malware also steals user credentials. There are also hints, that spreading the malware via networks isn't restricted to unpatched SMBv1 vulnerabilities. And there is hope, that a kind of Killswitch/vaccine has been found to protect a machine from encryption.
Talos analysis of 'Nyetya' malware
Security experts from Talos (Cisco) are calling the new Petya ransomware as Nyetya (for Not Petya) and has published a first analysis.
- The assumption, that the primary infection vector of this malware was an e-mail attachment hasn't been confirmed.
- Talos found indications, that the infection started via a compromised update system of Ukrainian tax system M.e.Doc.
Kaspersky has published a graphic, shown that the majority of infections (60%) are affecting systems within the Ukraine.
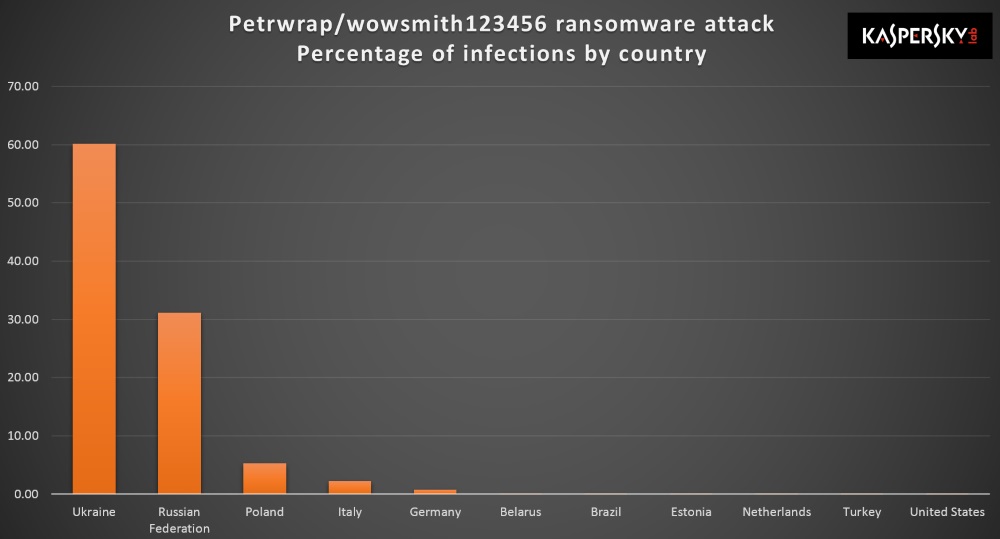
(Source: Kaspersky/BleepingComputer)
Within a tweet GossiTheDog says a forged digital signature is responsible for a compromised update system.
The payload appears to specifically reference the update process and uses a forged digital signature. It may be unconnected of course still. https://t.co/o7pFzuNQXx
— Kevin Beaumont (@GossiTheDog) 27. Juni 2017
At Bleeping-Computer this article also addresses this topic, the owner of M.E.Doc confirmed a virus infection, but denies later, that it's the source of the Petya attack.
Distribution via PsExec and WMIC in networks
If a Windows system is infected, a copy of admin tool PsExec (from Sysinternals tools) will be stored as dllhost.dat within the Windows folder. Then the malware uses WMIC commands and other strategies, to reach other machines within the network.
Just patching with EternalBlue (MS17-010) doesn't appear to save you – other techniques for lateral movement in play here it looks like.
— Dave Kennedy (ReL1K) (@HackingDave) 27. Juni 2017
The tweet above from Dave Kennedy says, that patching the ETHERNALBLUE vulnerability (MS17-010) doesn't prevent the malware spread over a network. Talos has published an article, containing commands to invoke PsExec and WMIC.
C:\WINDOWS\dllhost.dat \\w.x.y.z -accepteula -s -d C:\Windows\System32\rundll32.exe C:\Windows\perfc.dat,#1
The command above contains a file perfc, mentioned below within the Killswitch section. Then a WMIC command tries to reach shares using a user name and a user password:
Wbem\wmic.exe /node:"w.x.y.z" /user:"username" /password:"password" "process call create "C:\Windows\System32\rundll32.exe \"C:\Windows\perfc.dat\" #1"
Currently Talos tries to analyze, how the malware is able to obtain user credentials.
Credential Stealer integrated
Within this tweet I got the information, the same information, that login data are used within a network. Also this tweet contains a similar information:
Not sure on technique yet here, but crews being used for authentication to systems not just loggedin_user https://t.co/fEumwgs4Ho
— Dave Kennedy (ReL1K) (@HackingDave) 27. Juni 2017
This Arstechnica article cites security researcher saying, that a 2nd function within this ransomware tries to harvest user names and passwords and send it to servers controlled by the attackers. So the infected system is forced to be inaccessible, but the attackers gain access to login data and may use it to infect more machines.
Killswitch found?
On Twitter Amid Serper posted this tweet, indicating a 'Kill switch' has been found to stop an infection:
98% sure that the name is is perfc.dll Create a file in c:\windows called perfc with no extension and #petya #Nopetya won't run! SHARE!! https://t.co/0l14uwb0p9
— Amit Serper (@0xAmit) 27. Juni 2017
So a write-only file perfc (without extension) located within the Windows folder may stop the ransomware. Here are a 2nd source confirming that. So it's possible to copy a file and rename it. It seems that this file prevent the encryption routine on a infected machine – but that's far away from a kill switch stopping other infections. At MalwareBytes a blog post also says, it prevents only the malware on the current machine. Bleeping Computer has this article detailing how to create the file mentioned above.
Addendum: Microsoft has details and recommdations
Microsoft has published this blog post with many details about Petya. Microsoft confirms some infection theories, says, that Defender and other MS AV products has been updated to recognise this ransomware and gives also hints to avoid infections.
Similar articles:
Petya ransomware is back – using WannaCry vulnerabilties
WannaCry & Co.: EternalBlue Vulnerability Checker and Crysis Ransomware Decryptor
Ransomware WannaCry infected worldwide thousands of Windows systems




https://www.bleepingcomputer.com/news/security/surprise-notpetya-is-a-cyber-weapon-its-not-ransomware/