 [German]Windows 10 had a bug, that allowed malware to trick Windows 10's Anti-Malware Scan Interface (AMSI) by including a null character. The character simply caused the code not to be scanned. The bug was fixed on February 2018 patchday.
[German]Windows 10 had a bug, that allowed malware to trick Windows 10's Anti-Malware Scan Interface (AMSI) by including a null character. The character simply caused the code not to be scanned. The bug was fixed on February 2018 patchday.
What is Anti Malware Scan Interface (AMSI)?
The Antimalware Scan Interface (AMSI) is a generic interface standard that allows applications and services to integrate with any anti-malware product on a machine. It provides enhanced protection against malware for users and their data, applications and workloads.
It has been introduced in Windows 10 (I've mentioned within my German blog post Welche Antivirus-Lösung soll ich einsetzen?). Microsoft has published an article in summer 2015 within this Microsoft blog post. More details may be found at MSDN within this article.
Anti Malware Scan Interface bypassing bug
Security researcher Satoshi Tanda from Vancouver (Canada) has found a bug in the Anti-Malware Scan Interface. If a null character (00H) is inserted in a file, the part behind this character within the file is simply no longer scanned. The null character acts as an end-of-file (EOF) tag. A malware developer could then place malware behind the null character that would not be detected during the scan.
Within this blog post Tanda has posted more technical details. In brief: The library System.Management.Automation.dll didn't consider that such null characters may occur in PowerShell files. Tanda created PowerShell scripts with such null characters and passed them to the AMSI providers for scanning. As expected, the 'harmful' script components behind the null character were not detected, as they were not scanned.

(Source: standa-note.blogspot.de)
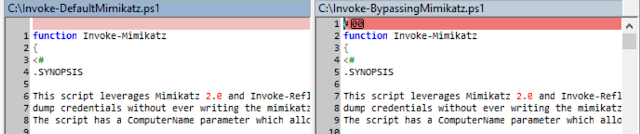
Within the blog post, he has published an example in which a PowerShell statement downloads a Mimikatz exploit from the Internet. As expected, the thread protection (in the picture above this is the Windows Defender) shows an alert, the when running the PowerShell script.
 (Source: standa-note.blogspot.de)
(Source: standa-note.blogspot.de)
Then he inserted a null character in the PowerShell script (screenshot above, right window) and let it run again under Windows 10.

(Source: standa-note.blogspot.de)
The above command prompt window shows that the PowerShell script has been executed. In the blog post Tanda describes his approach. A null character is sufficient to mask the malicious code, although it can be executed afterwards.
Microsoft has fixed this bug with the February 2018 patchday, as Tanda writes. But he recommends that third parties check their anti-malware products to see if null characters are tolerated and the product scans the entire file. (via)



