![]() [German]Users of micro-routers should urgently update their firmware. Because a vulnerability that became known two days ago is already being exploited for attacks.
[German]Users of micro-routers should urgently update their firmware. Because a vulnerability that became known two days ago is already being exploited for attacks.
Vulnerability known, update available
Two days ago Mikrotik released a Security Advisory Vulnerability exploiting the Winbox port (see also my German blog post Mikrotik-Router: Sicherheitslücke im Winbox-Port about this vulnerability).
The vulnerability was discovered by Mikrotik and affects all RouterOS versions from v6.29 to.43rc3. The vulnerability allowed a special tool to connect to the Winbox port and request the system user's database file.
The manufacturer has already released the router OS versions v6.42.1 and v6.43rc4 on April 23, 2018, which close this vulnerability.
First attacks observed
Bleeping Computer reported here that exactly this vulnerability is already being exploited. According to a Czech forum, a zero-day exploit was discovered with which the user database can be read.
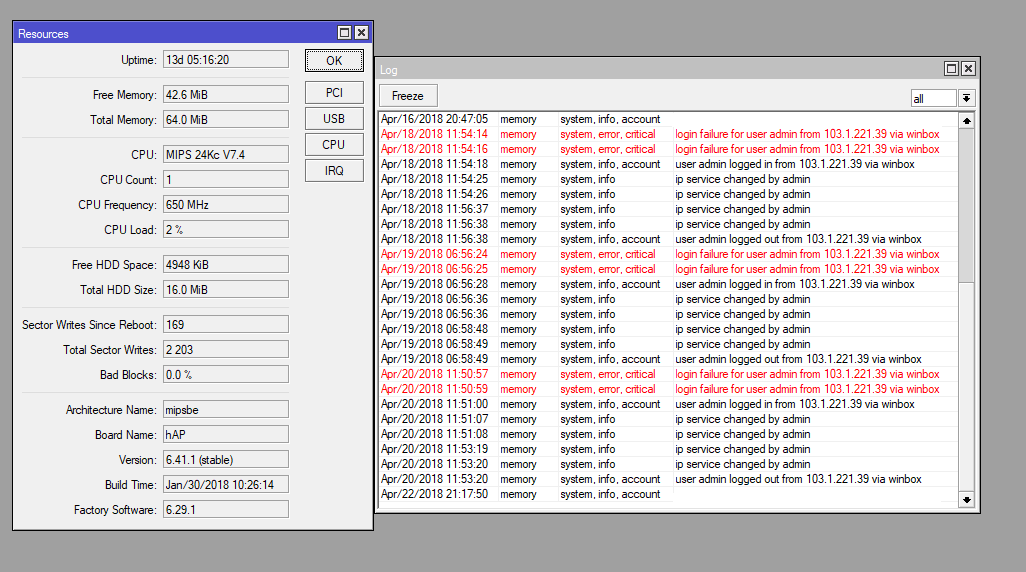
If the attacker succeeds in accessing the user data and decrypting the data, he can then log into the system via the web interface of the router. The hacks followed a similar pattern. The attacker produces two failed Winbox logon attempts and one successful login (screenshot above). Then he changes some services in the router and logs off to come back a few hours later.
All attacks were conducted using Winbox, a remote management service MikroTik offers with its routers to allow users to configure devices over a network or the Internet. The Winbox service (port 8291) is delivered with all MikroTik devices by default.
Zero-Day was not used on a massive scale
The good news is that so far all attacks have only been performed from one IP address, indicating that this was the work of a single hacker. The IP address 103.1.221.39 of the attacker, which all attacked users reported, was assigned in Taiwan.
However, you should update immediately and change the login passwords for the router access as a precaution.