 [German]In Windows 10 V1903, Windows Defender receives tamper protection. Here are a few details, what this is and how it affects administrators in enterprise environments.
[German]In Windows 10 V1903, Windows Defender receives tamper protection. Here are a few details, what this is and how it affects administrators in enterprise environments.
Microsoft has just introduced Windows Defender Tamper Protection again and released some more details (I became aware about the new article via).
What is Defender Tamper Protection?
Microsoft intends to protect the Windows Defender included in Windows 10 against malware tampering. It should not be possible for a malicious program to switch off Windows Defender. The Insider Previews (Build 18305 and later) of Windows 10 V1903 introduced the so-called Windows Defender Tamper Protection (see this article on Preview Build 18305 in the Windows Blog). Martin Brinkmann from ghacks.net reported briefly about this new feature in this article in December 2018.
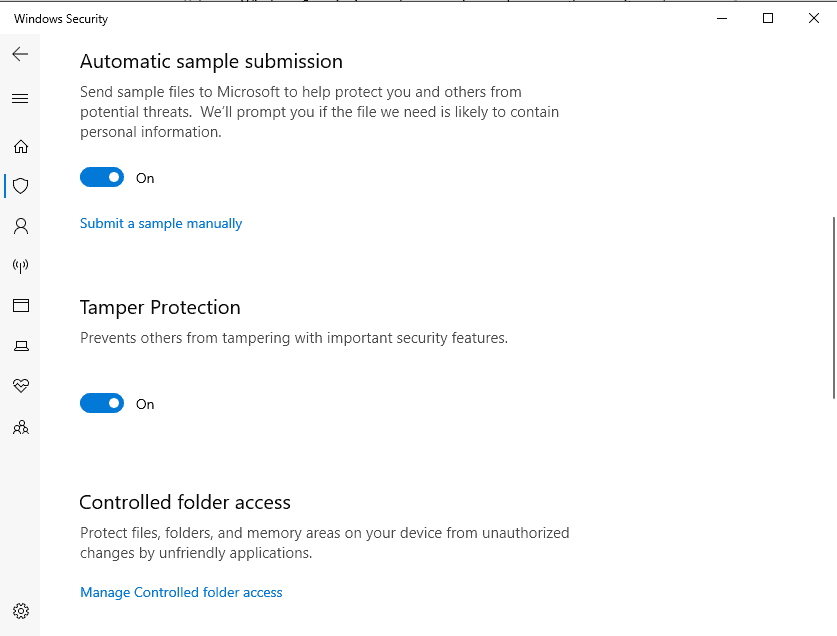
(Windows Defender Tamper Protection, Source: Ghacks.net)
Also this tensforum post discusses the question of how to switch this function on or off. Microsoft has published in Feb. 2019 the article Prevent changes to security settings with Tamper Protection. They wrote about Windows 10:
Tamper Protection in Windows Security helps prevent malicious apps from changing important Windows Defender Antivirus settings, including real-time protection and cloud-delivered protection. If Tamper Protection is turned on and you're an administrator on your computer, you can still change these settings in the Windows Security app. However, other apps can't change these settings.
Tamper Protection is turned on by default. If you turn off Tamper Protection, you will see a yellow warning in the Windows Security app under Virus & threat protection. Tamper Protection doesn't affect how third-party antivirus apps work or how they register with Windows Security.
More details about Windows Defender Tamper Protection
Microsoft's Eric Avena provided now more details within the blog post Tamper protection in Microsoft Defender ATP.
Tamper protection is a new setting available in the Windows Security app which provides additional protections against changes to key security features, including limiting changes that are not made directly through the app.
Then Eric Avena describes, who can switch the Tamper Protection status and what's the default settings:
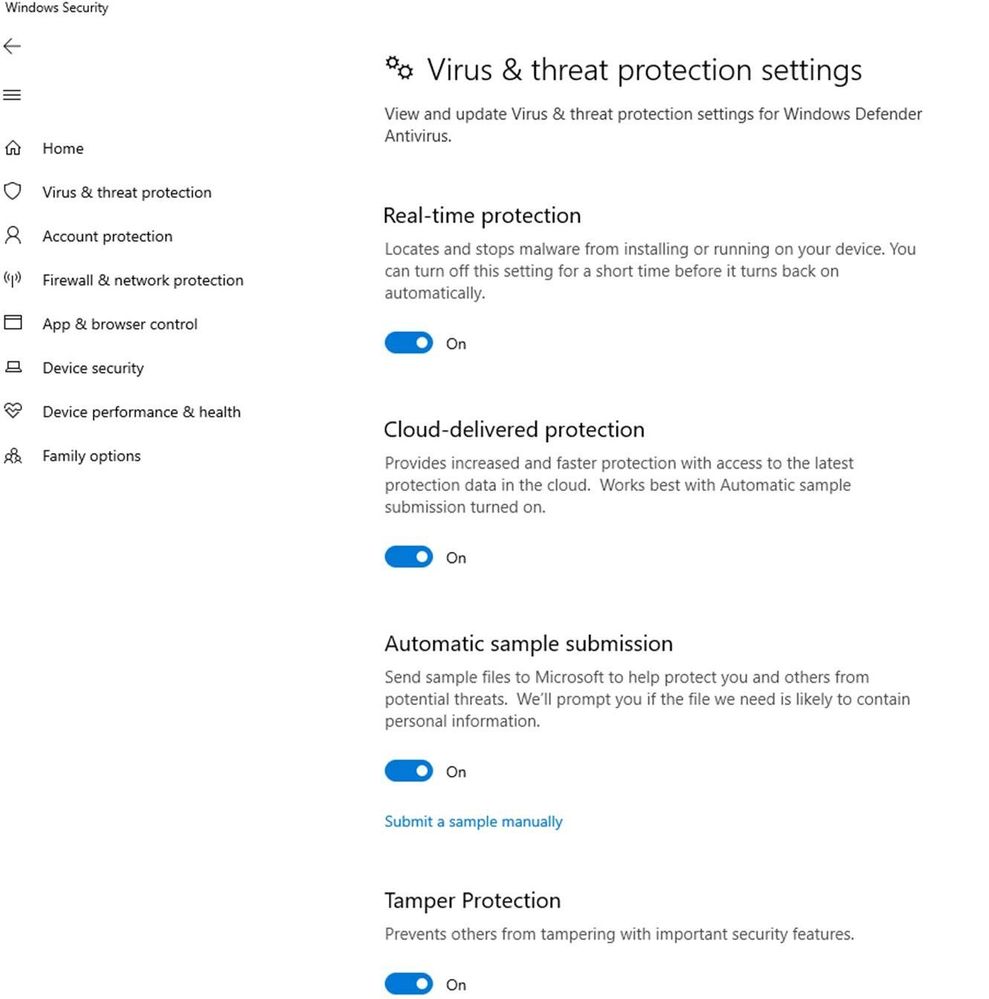
(Defender options for Tamper protection, Source Microsoft)
- Home users can toggle the setting from the Virus & threat protection settings area in the settings app.
- For enterprise environments, the setting can be managed centrally through the Intune management portal. There is also an opt-in required for these environments.
Enabling this feature prevents other (including malicious applications) important protection features such as:
- disable the real-time protection, which is the core feature of Microsoft Defender ATP Next-Gen protection,
- disable the Cloud-delivered protection, which uses Microsoft's cloud-based detection and prevention services to block never-before seen malware within seconds
- disable the IOAV protection (stand probably for Internet On-demand Antivirus, see here), die die Erkennung verdächtiger Dateien aus dem Internet übernimmt,
- disable the behavior monitoring, which uses real-time protection to analyze and determine whether active processes are behaving suspiciously or maliciously and blocking them.
The feature also prevents Security Intelligence updates from being deleted and the entire anti-malware solution from being deactivated. The feature is currently undergoing a limited preview test. Microsoft writes that the feature is supported by the current Windows Insider Build from March 2019 or later published builds. If you want to test the function, you can contact Microsoft via the Feedback Hub.
Collision with Group Policy?
German blog reader David Xanatos informed me a few days ago about an observation with Tamper Protection. David wrote:
In the new Windows Build 1903, Windows Defender has a new Defender Tamper Protection feature.
The problem is that as long as [Tamper Protection] is active, it seems that it is not possible to turn off Windows Defender via GPO.
David used the GPO "Turn Off Windows Defender Antivirus". Maybe Microsoft provides another GPO to turn off Tamper Protection, so Windows Defender GPOs are working again. The Microsoft blog post doesn't answers these questions – so let's wait what the final of Windows 10 V1903 brings within this area. Administrators should keep an eye on this feature.




I confirm the issue with Defender's GPOs here, I was wondering why all of a sudden it started to run in real-time again until I stumbled upon this tampering protection.
In theory sounds like a good idea, but if it's going to be troublesome for sysadmins who disable Defender (or parts of) via GPOs things will get nasty when it reaches general availability.
Strangely enough, there seems to be a registry key governing the anti tamper protection at HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender\Features. It's a DWORD named TamperProtection, so we may end up seeing another GPO for it.