![]() [English]Security researchers have now probably seen for the first time a meta sploit on the net that wants to exploit the BlueKeep vulnerability and tries to install Crypto-Miner. At the moment, however, this exploit still ends with BlueScreens.
[English]Security researchers have now probably seen for the first time a meta sploit on the net that wants to exploit the BlueKeep vulnerability and tries to install Crypto-Miner. At the moment, however, this exploit still ends with BlueScreens.
The BlueKeep vulnerability in the Windows RDP service threatens unpatched systems from Windows XP to Windows 7 and their server counterparts. I had been warning about the BlueKeep vulnerability for months (see BlueKeep warning: Exploit might come soon?). It seems, however, that the BlueKeep vulnerability is difficult to exploit in practice. This is the only way to explain that this issue has been quite quiet so far, although there is a publicly available metasploit (see Windows: Bluekeep Metasploit released in the wild). But that could change now.
RDP HoneyPots suddenly crashes with BlueScreens
I had already seen it at the weekend, but only now am I able to prepare something for it. Security researcher Kevin Beaumont had set up a worldwide network of honeypots for the RDP vulnerability after the BlueKeep vulnerability became known and the first exploits became available. On Saturday Beaumont reported that its EternalBlue RDP honeypot suddenly showed BlueScreens.
huh, the EternalPot RDP honeypots have all started BSOD'ing recently. They only expose port 3389. pic.twitter.com/VdiKoqAwkr
— Kevin Beaumont (@GossiTheDog) November 2, 2019
Specifically, the first BluesScreen with a restart start of the underlying Windows system already appeared on 23 October 2019. In the last weeks there were these BlueScreens at further Honeypots. The suspicion was that someone was trying to exploit the BlueKeep vulnerability. In another tweet, however, it quickly became clear that it was probably not a worm that had attacked the honeypot. According to Beaumont, there were probably only BlueScreens at various honeypots. Here is a post from him:
imma retrieving the crash logs to see if anything interesting pic.twitter.com/sEoMV37RG7
— Kevin Beaumont (@GossiTheDog) November 2, 2019
On November 2, 2019 he received his bill for the booked Microsoft Azure services and looked at the details of the Azure Sentinel for log analysis.
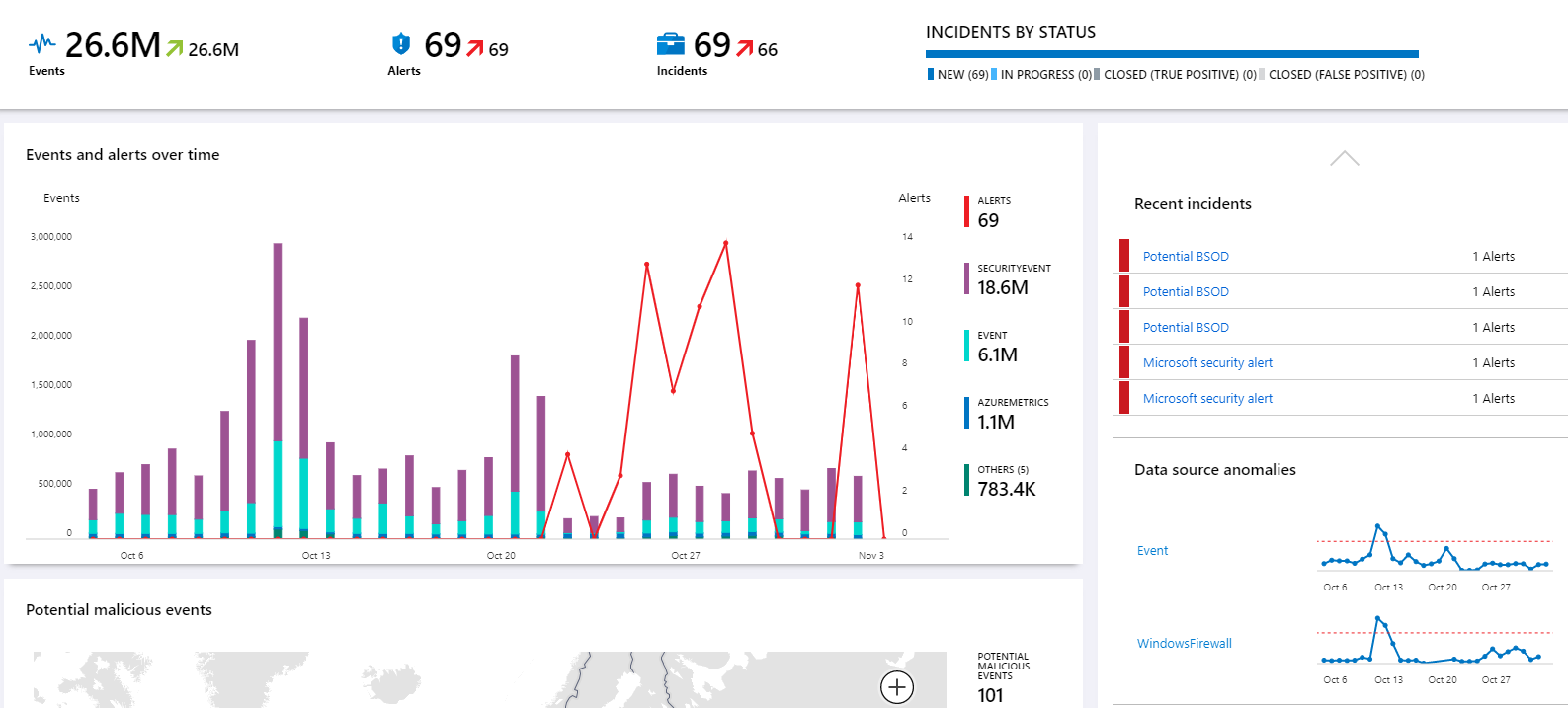
(Azure Sentinel, Source: Kevin Beaumont)
Since 22/23 October, problems (BSOD) have probably occurred with the affected azure instances. Then safety researchers looked at the crash dump of the BlueScreens – an analysis can be found here. MalwareTech security researchers confirmed that the kernel dump contained traces of a metasploit exploiting the BlueKeep vulnerability (or at least something based on it). It is probably an attempt to install a crypto-miner on Windows machines via the vulnerability. Beaumont has published now a writeup.
Here's a writeup of the BlueKeep exploitation activity investigated this weekend https://t.co/q1ne8uuyai
— Kevin Beaumont (@GossiTheDog) November 3, 2019
At present, the impact is still limited: It's not a worm that spreads itself, and the approach of putting a crypto-miner on the machines is unattractive, but not a major threat. But the conclusion from these attacks is that there are people who now understand how to attack random targets using BlueKeep vulnerabilities. There's a good chance the attacks will become more sophisticated soon. More articles can be found at Wired, The Hacker News or ZDNet.
Background: BlueKeep vulnerability
I had reported about the BlueKeep vulnerability CVE-2019-0708 in several blog posts. An explanation of the vulnerabilities can be found in the blog post Security Critical update for Windows XP up to Windows 7 (May 2019).
There is a patch, but it has not been installed on all systems. It is currently estimated that approximately 800,000 systems are still unpatched and accessible via the Internet (see Windows: What about the BlueKeep vulnerability in July 2019? ). In my blog post How To: BlueKeep-Check for Windows, I explained how a system can be scanned both locally for installed patches and in a network for vulnerabilities.
Addendum: An analysis, how the hacker are using the vulnerability may be found here (deleted).
Similar articles
A threat actor scans Windows systems for BlueKeep vulnerability
BlueKeep: Windows Remote Desktop Services vulnerability exploits status
Critical update for Windows XP up to Windows 7 (May 2019)
Nearly 1 million Windows machines with BlueKeep vulnerability
BlueKeep vulnerability: Microsoft warns about a wormable malware epedemia
BlueKeep: Patch for pirated copies; SSL tunnel as a risk factor
Windows: Bluekeep Metasploit released in the wild
BlueKeep warning: Exploit might come soon?
How To: BlueKeep-Check for Windows



