![]() [German]In the last few days there have been a number of reports of cyber incidents in German institutions that are attributed to the emotet Trojan/Ransomware. The BSI warns of the danger, especially since spam mail is sent 'on behalf of the federal authorities' with this malware in its luggage.
[German]In the last few days there have been a number of reports of cyber incidents in German institutions that are attributed to the emotet Trojan/Ransomware. The BSI warns of the danger, especially since spam mail is sent 'on behalf of the federal authorities' with this malware in its luggage.
Advertising
I've discussed the last cases in the German article Trojanerbefall in Stadt Bad Homburg und Hochschule Freiburg. But also Frankfurt and the University of Gießen were infected – although the infection in Frankfurt was probably mild – the IT systems are back in operation after a day. In the following tweet, CERT-Bund points out the danger of an infection with the Trojan Emotet.
⚠️Beware of #Emotet – currently one of the most dangerous botnets in operation. #certbund once again became aware of several high profile victims.
‼️ Don't be the next ‼️
— CERT-Bund (@certbund) December 16, 2019
After an infection of the Windows system, the Trojan can reload any malware and constantly converts its signatures and attack variants. It seems also that the cyber criminals behind Emotet has changed their tactics: The Trojan horse are no longer delivered in mail attachments. Instead, a link to compromised websites is sent by email. A drive-by downloader then waits on the pages or the user is tricked into to download an Emotet Trojan via a file.

(Source: Pexels Markus Spiske CC0 Lizenz)
Nasty: German authorities infected
There is a fresh warning from the German Federal Office for Information Security (BSI). Bleeping Computer have also addressed it. According to the report, the BSI has been notified of several confirmed emotet-infections in authorities of the federal administration.
Advertising
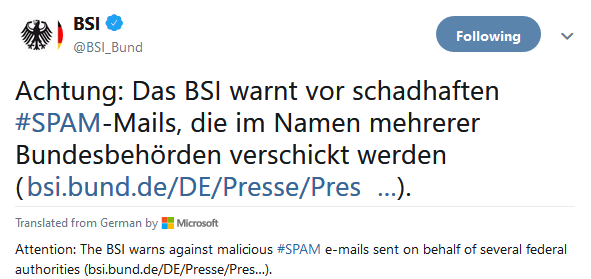
(Source: Bleeping Computer)
The unknown attackers are currently using the data copied in the process to send fraudulent e-mails with dangerous file attachments or links on behalf of several federal authorities. Greta Thunberg is also being misused as bait in spam mail, as this article reveal – and the cyber criminals are constantly adjusting their strategy – Bleeping Computer has made it a subject of discussion here.
Prevent infection in advance
Administrators in corporate environments should take steps to block infection vectors. Here is a recommendation from CERT-Bund:
Biggest impact recommendations for SOCs, CERTs, and CSIRTs on how to block Emotet malspam¹:
Block macro office docs & emails w/ known bad URLs ASAP + Use URLhaus ClamAV signatures + Block known Emotet C&C communication.¹ Provided by @abuse_ch via https://t.co/rrsakWK7Dt
— CERT-Bund (@certbund) December 16, 2019
But also the following tweet from the USA indicates that infections can also occur via USB devices.
I think the City of New Orleans learned the lesson #WeaponizedUSBdevices #MaliciousUSBimplants#WHIDelite #WHIDinjector #USBsamurai pic.twitter.com/B97da2B6uU
— WHID Injector (@WHID_Injector) December 16, 2019
To minimize the damage in case of an infection, administrators and computer users should have emergency instructions on how to act in case of suspected infection. Within the following tweet Catalin Cimpanu recommended not to restart the system after an infection.
Experts: Don't reboot your computer after you've been infected with ransomwarehttps://t.co/Yzs6CfWAPH pic.twitter.com/Ne0AwjVrdz
— Catalin Cimpanu (@campuscodi) November 5, 2019
Instead switch to the Hibernate mode, cut the network connection and let a specialist check the isolated system for a possible infection. It will be also a good idea, to read the FAQ: Responding to an Emotet infection and prepare for the emergency case.







