![]() [German]The provider SAVE.TV is back online with his service since a few days – and after a hack. The same applies to the UseNeXT.de service. I had the topic with me on resubmission in order to add or disclose information. Now I know more inside details and had also recognized, that the ransomware gangs behind the attack also released extinct data.
[German]The provider SAVE.TV is back online with his service since a few days – and after a hack. The same applies to the UseNeXT.de service. I had the topic with me on resubmission in order to add or disclose information. Now I know more inside details and had also recognized, that the ransomware gangs behind the attack also released extinct data.
Save.tv/UseNeXT.de hack and the shutdown
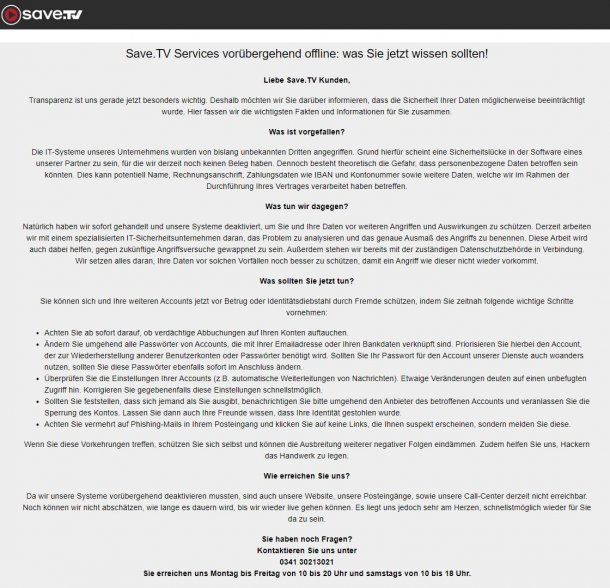
The SAVE.TV service was switched off at the end of April 2020. SAVE.TV is a service that acts as an online recorder for TV shows and stores them in the cloud. At the same time, the UseNeXT.de service, which provides access to usenet, was shut down. Based on reader e-mails, it quickly became clear that it was a hacker attack that forced the operators to shut down these services.
(Source: heise, Click to zoom)
This was then also communicated some time later on the websites of the services. If you are interested in the details, you will find it in my blog post Online video recorder service SAVE.TV [and UseNeXT] hacked.
Save.tv/UseNeXT.de services are back
A few days ago I got the information (I forgot the source) that the service of the provider save.tv is available again. When I checked save.tv and usenext.de, I found out, that both services are back in business.

After the hack, both providers recommended that users reset their passwords for the accounts. Save.tv offers the following form for this purpose, in which the user name or customer number must be entered.

The reason: it could not be excluded that user, registration and payment data had been leaked. On the re-accessible pages of both providers, you will therefore find, in addition to the entry 'Important information about your xxxx account', a button for resetting the password, which then displays the above form.
Note: Both services addresses primary German readers. But the case is a blue print, what can happens after a cyber attack – as you can read below. And I received comments for my yesterday German blog post, reporting, that the service of save.tv is limited and still hasn't all previous feature.
Background information about the Hack
Due to the reports I knew that the cyber attack happened to the service provider Omniga. I had also reported in the blog article Online video recorder service SAVE.TV [and UseNeXT] hacked, that the intruders used a compromised/hacked VPN access gateway.
I was also told by Omniga that it was unclear whether any data had been leaked at all. According to the provider, the data protection supervisory authority was informed promptly and a forensic team had started investigations. Omniga has clearly denied any suspicions from readers that passwords were stored by save.tv in plain text.
Ragnar Locker in action
Some days ago I received some information from security researchers. I now know that files were encrypted by Ragnar Locker. This is a ransomware that comes via a Virtualbox VM to escape detection. I learned also, that the ransomware group extinted data and tried to blackmail the company with the disclosure. Since no payment was made, data was published.
Only Omniga customers affected
In response to a specific request concerning this matter, a spokesperson for Omniga, referring to a forensic report now available, stated that 'it can be assumed that the types of data concerned are limited to e-mails, contractual documents and documents in administrative [Omniga] directories, but do not include database exports'. The company states that 'To the best of its knowledge, no sensitive customer data has been stolen, either from the customer-specific directories or from the technologies used by the individual shops.
So in my understanding, what Omniga told me, no personal data from Save.TV or UseNeXT customers are affected.
Still a huge disaster
Due to a lack of sufficient resources, I cannot fully verify the above statements. A directory dump I've seen, seems to be consistent with the forensics statements above. Information that I was able to check through security researchers seems to prove that data from Omniga customers (including bank details) has been dumped. In addition, the contents of a KeePass store, including its very simple master password, was published as a screenshot. So the attackers had access to all accounts (some important) stored there, including passwords. And the attackers seem to have accessed the Active Directory of the network, as I could see in screenshots. However, I assume that not all extinct data has been published. The damage seems to me to be substantial – but Omniga was smart enough not to pay, even at the risk of data being published. There is a risk that data may be passed on despite payment or that 'additional claims' may suddenly arise, as cases in the near past have shown.
Similar articles
Online video recorder service SAVE.TV [and UseNeXT] hacked
City of Weiz (Austria): Computers infected with ransomware?
Security incident at the Santander Bank website in Belgium
Revil Ransomware hackers release first Trump files
Warning: Infected Cookie Consent logo delivers Ransomware
Security incident: Source Code for Mercedes OLU leaked
News on the ransomware attack on Ludwigshafen supplier
Diebold Nixdorf victim of a Ransomware Attack
Clop Ransomware attack at Technische Werke Ludwigshafen
Fresenius probably victim of a Snake Ransomware attack
Ransomware strikes at night and on weekends



