 [German]Brief warning to administrators of Microsoft Exchange servers. While investigating an attack on a major U.S. hospitality company, security firm Sophos has discovered a new ransomware called Epsilon Red. Red Epsilon exploits unpatched vulnerabilities in Microsoft Exchange servers to infect machines on the network and then encrypt files there.
[German]Brief warning to administrators of Microsoft Exchange servers. While investigating an attack on a major U.S. hospitality company, security firm Sophos has discovered a new ransomware called Epsilon Red. Red Epsilon exploits unpatched vulnerabilities in Microsoft Exchange servers to infect machines on the network and then encrypt files there.
In this blog post, Sophos security researchers report on the new ransomware discovered a few days ago, written in the Go programming language and called Epsilon Red. The name Epsilon Red is a reference to pop culture. The character Epsilon Red was a relatively obscure adversary of some X-Men in the Marvel extended universe, a "super soldier" who was supposedly of Russian origin and had four mechanical tentacles and a bad character.
Analysis of the Epsilon Red Ransomware
Analyzing the infection at a U.S. company, analysts found that the malware was delivered as the final executable payload in a hand-delivered attack. During the attack, the threat actors launched a series of PowerShell scripts named 1.ps1 through 12.ps1 (as well as some named with only a single letter from the alphabet). The task of these PowerShell scripts was to prepare the attacked computers for the final ransomware payload and eventually download and install it.
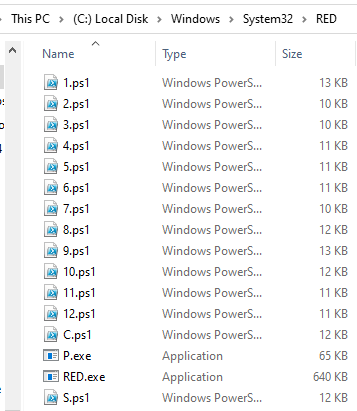
Epsilon Red files, Source: Sophos
The PowerShell script sequence was created by the RED.ps1 PowerShell script and then executed on the target computers using WMI. The script retrieves a .7z archive file from the control server that contains the rest of the PowerShell scripts, the ransomware executable file, and another executable file. These files are then extracted to the Windows system32 folder. The PowerShell script also sets up scheduled tasks that run the scripts numbered 1 through 12, but skips numbers 7 and 8. It also creates tasks for scripts named "S" and "C."
Exchange probably the gateway for the attack
The security analysts write that it looks like a Microsoft Exchange server of the company was the attackers' original entry point into the corporate network. It's not clear whether this was enabled by the ProxyLogon exploit or some other vulnerability, but it seems likely that the cause was an unpatched server. From this machine, the attackers used WMI to install other software on machines within the network that they could reach through the Exchange server.
Ransomware quite small
The ransomware itself is quite small, as it is only supposed to perform the encryption of files on the target system. No network connections are established. Functions such as killing processes or deleting volume shadow copies have been outsourced to PowerShell scripts. .
The program encrypts all files located in the folders to be encrypted. This includes executable files and DLLs, which can cause programs or the entire system to stop working. After a file is encrypted, the file suffix ".epsilonred" is added to the filenames. The ransomware drops a ransom note in each folder. The ransom note is very similar to that of REvil. However, it lacks the spelling and grammar errors typically included in REvil texts. Apparently, the ransom note sent by Epsilon Red has been edited a few times to make the text more readable for an audience of native English speakers. More details can be read in the Sophos article. (via)



