[German]Unpleasant discovery that a security researcher has made public the days. The Google Chrome browser, and also the Chromium-based Microsoft Edge browser, may transmit in some cases personal data from forms to Google and Microsoft (in the case of Edge). This also includes passwords, by the way. The Extended Spell Checker in the browser or in the MS Editor is probably responsible for this.
[German]Unpleasant discovery that a security researcher has made public the days. The Google Chrome browser, and also the Chromium-based Microsoft Edge browser, may transmit in some cases personal data from forms to Google and Microsoft (in the case of Edge). This also includes passwords, by the way. The Extended Spell Checker in the browser or in the MS Editor is probably responsible for this.
The browser leaks data
The research team at Otto, a security company specializing in JavaScript (otto-js.com), looked into the two browsers Google Chrome and Microsoft Edge and made the unpleasant discovery that both browsers can pass on the user's private data to Google and Microsoft.
The data in question is form data that the user must enter or enters when visiting websites in the browser. This can be usernames, email addresses, social security numbers, etc., but also passwords. Normally, this data should only be transmitted to the website that the respective user is currently visiting. However, with the Advanced Spell Check feature, which can be activated in Google Chrome, such entries are transmitted to Google for verification. It is similar with Microsoft Edge, where the transmission is made to Microsoft. In a blog post published on September 16, 2022, the security researchers write about this:
Chrome's enhanced spellcheck & Edge's MS Editor are sending data you enter into form fields like username, email, DOB, SSN, basically anything in the fields, to sites you're logging into from either of those browsers when the features are enabled. Furthermore, if you click on "show password," the enhanced spellcheck even sends your password, essentially Spell-Jacking your data.
So, the one responsible is the Advanced Spell Checker in Google Chrome or the MS Editor in Microsoft Edge. But the Advanced Spell Checker must be explicitly enabled by the user. And the user must be logged in to his user account with his browser at Google or Microsoft. To do this, they say:
Some of the largest websites in the world have exposure to sending Google and Microsoft sensitive user PII, including username, email, and passwords, when users are logging in or filling out forms. An even more significant concern for companies is the exposure this presents to the company's enterprise credentials to internal assets like databases and cloud infrastructure.
The team documented an example with a login to the Alibaba website in their blog post. The screenshot below shows the user input in the login form.
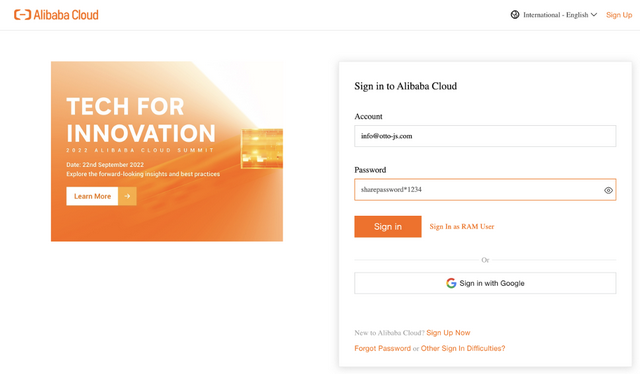
Alibaba login page, Source: otto-js.com
Then the security researchers looked at the transmitted data as well as the JavaScript source code and came across their discovery. The screenshot below shows an excerpt from the data and source code:
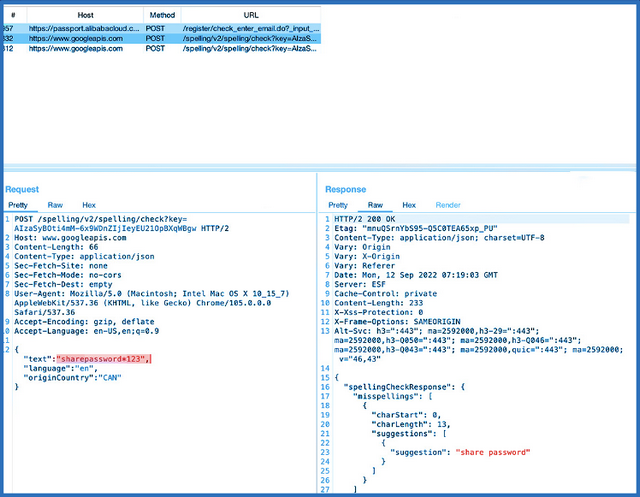
Transmitted / received data, source: otto-js.com
In the above example, the Google API of the spell checker is addressed and the associated browser script transfers the content of the form field (sharedpassword in this case) to the spell checker in plain text, in order to receive a suggestion. In the following YouTube video, the security researchers demonstrate the observation.
In their article, the security researchers have listed several websites where such confidential information was submitted by the Advanced Spell Checker when visiting them. The colleagues from Bleeping Computer have checked other websites and found the same behavior there.
Of course, this is all a machine evaluation and there is no employee at Google or Microsoft sitting at the server waiting for incoming passwords or confidential data. But the fact alone that form fields with sensitive data are transferred to Google or Microsoft is a no-go.
Companies are unlikely to be too happy about this data going to third parties, because no one has any control anymore over where this data ends up and what happens to it. In the dumbest case, cloud and network security is compromised – in Europe, there's also the fact that there may be violations of the DSGVO if personal data is transferred to third parties in forms. I don't think this has been considered in the GDPR approach to data processing (but I may be wrong).
Mitigations possible
Enterprises can mitigate the risk of sharing their customers' personal data by adding the option "spellcheck=false" to all input fields on the websites in question. However, this may cause problems for users. In such cases, companies could also set up this option only for the form fields containing sensitive data.
Both Amazon (AWS) and LastPass have responded to the security researchers' notice and made the relevant adjustments. Companies can also remove the "Show password" feature. This won't prevent spell-jacking, but it will prevent user passwords from being sent. Enterprises can also use client-side security software (e.g., from otto-js) to monitor and control third-party scripts.
Enterprise administrators should reduce internal exposure of proprietary accounts by implementing endpoint security solutions that disable advanced spell checking and prevent employees from installing unauthorized browser extensions.
Users of the Chrome browser the option to turn off the Advanced Spell Check feature in Chrome Settings under Sync and Google Services (if necessary, simply search for Spell Check in Settings – or use chrome://settings/?search=Enhanced+Spell+Check, see here and here).
For Edge, the Microsoft Editor spell and grammar checker is a browser addon that must be explicitly installed to enable this behavior. If present, this browser addon should be uninstalled.
Similar articles:
Chrome stores passwords in memory in plain text
Google Chrome allows websites to write (without asking) to the Windows clipboard
Google Chrome: Block list for extensions (ADMX) has changed in build 86