 [German]US provider Cisco warns in a message about a critical vulnerability in one of its phone adapters. This vulnerability allows an attacker to take control of the device. Unfortunately, affected users can only dispose of this phone adapter, since the manufacturer will no longer offer a security update. The reason is that the device has reached the end of its support period.
[German]US provider Cisco warns in a message about a critical vulnerability in one of its phone adapters. This vulnerability allows an attacker to take control of the device. Unfortunately, affected users can only dispose of this phone adapter, since the manufacturer will no longer offer a security update. The reason is that the device has reached the end of its support period.
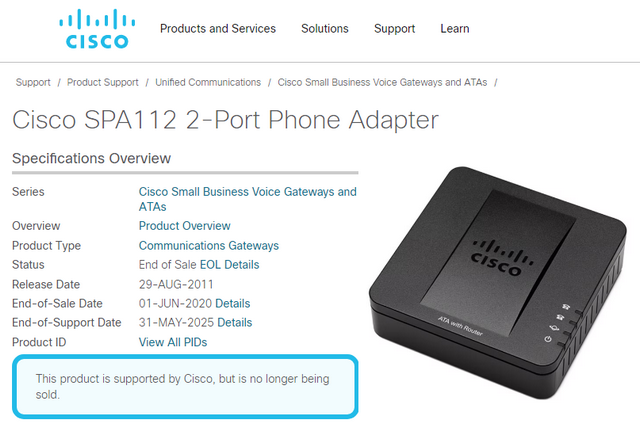
Cisco SPA112 2-Port Phone Adapter
The Cisco SPA112 2-Port Phone Adapter has been on the market since around August 2011 and is currently even still being sold on the Internet. Officially, the sale was discontinued on June 1, 2020, but support is still supposed to be available until May 31, 2025 for owners of a maintenance contract (see the following screenshot).
The adapter allows analog phones and fax machines to be connected to a network for IP telephony.
Cisco security alert
As of May 3, 2023, Cisco has issued the security alert Cisco SPA112 2-Port Phone Adapters Remote Command Execution Vulnerability regarding a critical vulnerability. Among other things, the following tweet points out this warning.
In its alert, the vendor points out a critical vulnerability in the web-based management interface of the Cisco SPA112 2-port phone adapter. The vulnerability, CVE-2023-20126 , is due to a missing authentication process within the firmware upgrade function, and has a CVS 3 Base score of 9.0, according to The Register.
Rated as extremely critical, the vulnerability in the Cisco SPA112 2-port phone adapter's web-based management interface could allow an unauthenticated, remote attacker to execute arbitrary code on an affected device.
The problem with the whole story is that Cisco has not released any firmware updates to address this vulnerability, nor does it plan to develop a fix (the device has reached end-of-life). There are also no workarounds to fix this vulnerability. Owners of such adapters have no choice but to retire the devices in question.




