[German]Short note for users who have Cisco components with IOS XE in use and these components are accessible via the Internet. As of October 16, 2023, Cisco issued a security warning about the 0-day vulnerability CVE-2023-20198, which is unpatched so far but is being exploited in the wild to take over Cisco components. In the meantime, the vulnerability seems to be exploited in fierce waves of attacks and 10,000s of compromised systems can be assumed.
[German]Short note for users who have Cisco components with IOS XE in use and these components are accessible via the Internet. As of October 16, 2023, Cisco issued a security warning about the 0-day vulnerability CVE-2023-20198, which is unpatched so far but is being exploited in the wild to take over Cisco components. In the meantime, the vulnerability seems to be exploited in fierce waves of attacks and 10,000s of compromised systems can be assumed.
Advertising
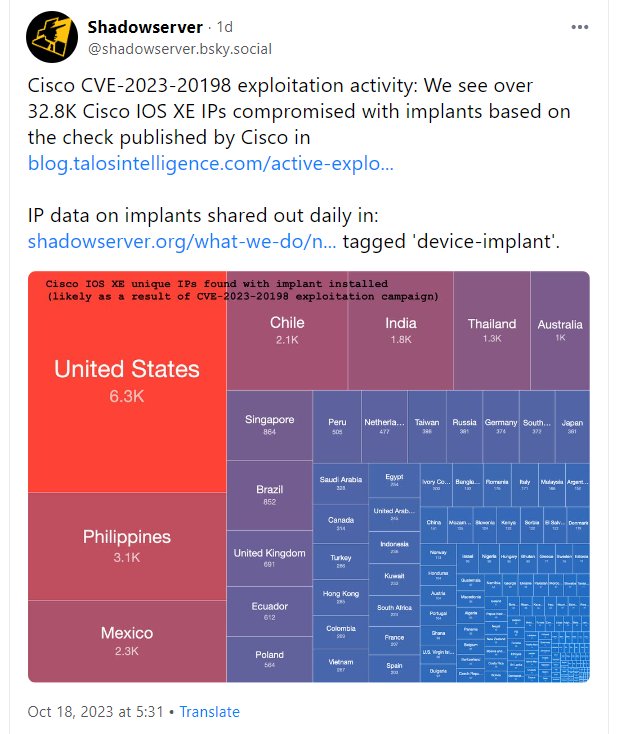
While Cisco only reports isolated cases, there are indications that the vulnerability has been exploited since August 2023 and that over 32,800 Cisco instances with IOS XE have now been compromised. All instances that are accessible via the Internet are likely to be affected. Fortunately, the German-speaking region (as far as I have seen so far) does not seem to be in the "hit list" of compromised systems. I have published the details as well as the supplements in the German blog post Cisco warnt vor bereits ausgenutzter 0-day-Schwachstelle (CVE-2023-20198) in IOS XE (16. Oktober 2023). Here are the details.
Vulnerability CVE-2023-20198
Cisco has released a security alert Cisco IOS XE Software Web UI Privilege Escalation Vulnerability, where Cisco confirms active exploitation of a previously unknown vulnerability (CVE-2023-20198) in the Cisco IOS XE Software Web UI feature.
The Web UI is an embedded GUI-based system management tool, for provisioning and managing the relevant Cisco components. The Web UI is shipped with the default image, and does not need to be activated. The Web UI is used to create configurations and to monitor and troubleshoot the system without CLI knowledge, but should not be accessible via the Internet or from untrusted networks.
If this web UI function is accessible from the Internet or an untrusted network, there is the highest risk. This is because this vulnerability allows a remote attacker to create an account with level 15 access rights on an affected system without authentication. The attacker can then use this account to gain control of the affected system.
This vulnerability affects Cisco IOS XE software when the Web UI feature is enabled. The Web UI feature is enabled using the ip http server or ip http secure-server commands. In the security alert, Cisco provides guidance on how to check if Web UI is enabled and what Indicators of Compromise (IoCs) exist.
Currently, there is no patch or workaround. On systems that are accessible via the Internet, Cisco recommends disabling the HTTP server feature. To do this, use the no ip http server or no ip http secure-server commands in global configuration mode. If both the HTTP server and the HTTPS server are used, both commands are required to disable the HTTP server feature.
Advertising
Talos warns of exploitation of CVE-2023-20198
Security researchers from Cisco Talos have published the article Active exploitation of Cisco IOS XE Software Web Management User Interface vulnerability as of October 16, 2023. There they confirm that Cisco has detected active exploitation of a previously unknown vulnerability in the Web User Interface (Web UI) feature of Cisco IOS XE software (CVE-2023-20198) when exposed to the Internet or untrusted networks.
Both physical and virtual devices running Cisco IOS XE software that also have the HTTP or HTTPS server feature enabled are affected. The first indication of potentially malicious activity emerged on September 28, 2023, when a case was opened at Cisco's Technical Assistance Center (TAC) because unusual behavior was detected on a customer device. Upon further investigation, security researchers observed activity as early as September 18 that was determined to be related.
This activity included an authorized user creating a local user account under the username "cisco_tac_admin" from a suspicious IP address (5.149.249[.]74). This activity ended on October 1, and security researchers did not observe any other related behavior at that time other than the suspicious account creation.
On October 12, Cisco Talos Incident Response (Talos IR) and TAC discovered another cluster of related activity that began on the same day, as later determined. In this cluster, an unauthorized user was observed creating a local user account under the name "cisco_support" from a second suspicious IP address (154.53.56[.]231).
Unlike the September case, this October 2023 activity included several subsequent actions. This included the deployment of an implant consisting of a configuration file ("cisco_service.conf"). The configuration file defines the new web server endpoint (URI path) used to interact with the implant.
This endpoint is given certain parameters, described in more detail in the Talos contribution, which allow the actor to execute arbitrary commands at the system or IOS level. For the implant to become active, the web server must be restarted; in at least one observed case, the server was not restarted, so the implant never became active despite being installed.
The implant is stored in the file path "/usr/binos/conf/nginx-conf/cisco_service.conf", and contains two variable strings consisting of hexadecimal characters. The implant is removed when the device is rebooted, but the newly created local user accounts remain active even after the system is rebooted. The new user accounts have privilege level 15, which means they have full administrator access to the device. For more details, see the linked Cisco and Cisco Talos articles.
Thousands of systems compromised
It seems that thousands of IOS XE instances have been compromised in a wave of attacks. Colleagues at Bleeping Computer have published this information in their postOver 10,000 Cisco devices hacked in IOS XE zero-day attacks. According to the post, attackers have exploited the critical zero-day bug outlined above to infect more than 10,000 Cisco IOS XE devices with malicious implants. Jacob Baines, CTO of VulnCheck, revealed this in his blog post.
Jacob Baines accuses Cisco of failing to mention that thousands of IOS XE systems that were accessible via the Internet had implants. That's a bad situation because privileged access to IOS XE likely allows attackers to monitor network traffic, penetrate protected networks and conduct any number of man-in-the-middle attacks, Jacob Baines said.
"If your organization is using an IOS XE system, it is imperative that you determine if your systems have been compromised and take appropriate action once the implants are discovered," Bleeping Computer's Jacob Baines is quoted as saying.
Meanwhile, I came across the above post on BlueSky with an overview of compromised systems (source is Shadow server). Rapid 7 has published a blog post with more findings, mitigation hints and detection of a compromise. There is a script on Github that can be used to detect a compromise if necessary.
Advertising