[German]I do not know if it's widely known, but the legitimate Windows application WorkFolders.exe can be used to launch other .exe programs in the Windows System32 folder or the current folder. This allows malware to launch so-called LOLBin attacks, where legitimate operating system files are misused to execute malicious programs. WorkFolders.exe can be abused as a RunDLL substitute.
[German]I do not know if it's widely known, but the legitimate Windows application WorkFolders.exe can be used to launch other .exe programs in the Windows System32 folder or the current folder. This allows malware to launch so-called LOLBin attacks, where legitimate operating system files are misused to execute malicious programs. WorkFolders.exe can be abused as a RunDLL substitute.
LOLBin, a brief insight
The acronym LOL stands for "living off the land," a term coined by malware researchers Christopher Campbell and Matt Greaber to explain the use of trusted, pre-installed system tools to spread malware. This Cynet page explains that there are different types of LOL techniques. Among them are so-called LOLBins, which use Windows binaries to hide malicious activities. LOLLibs use libraries, and LOLScripts use scripts to execute malware. Kaspersky has listed the most popular LOLBins in this article. And there is a GitHub project that aims to document every binary, library and script that can be abused for LOL techniques.
What does WorkFolders.exe do?
There is a executable file called WorkFolders.exe included in the System32 subfolder of Windows. It is a legitimate Windows application and the .exe file can be seen in the screenshot below in the Windows folder in question.
If you call this program file, the Working Folders window appears to manage these working folders in Windows (see the following screenshot of a German Windows 10). The text indicates that in the dialog you can manage the working folders to make "online" working files available on all devices used, even if you are offline.
Microsoft explains here, that Work Folders is a Windows Server role service for file servers, and provides users with a consistent way to access work files from PCs and devices. With Work Folders, users are supposed to be able to store and access their work files not only on company PCs, but also on personal computers and devices, often referred to as bring-your-own-device (BYOD).
Users should have a convenient place to store work files and can access them from anywhere. Organizations use Work Folders to maintain control over corporate data. They can store files on centrally managed file servers and set policies for user devices such as encryption and screen lock passwords. The service is available on Windows 11, Windows 10, Windows Server 2022, Windows Server 2019 and Windows Server 2016.
LOLBin with WorkFolders.exe
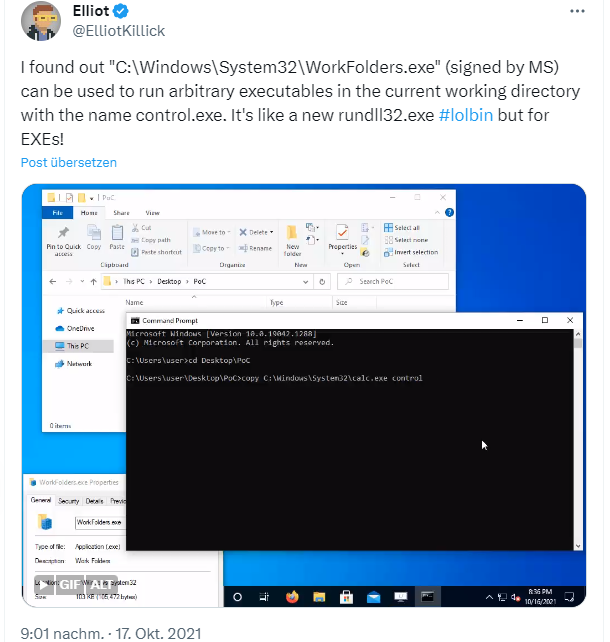
A few dasy ago I came across the following tweet, which left me quite pensive. Elliot shows how the WorkFolders.exe program file can be misused to call other program files.
In his test scenario, he copies calc.exe as control.exe from the Windows System32 folder to a local folder and then calls WorkFolders.exe. The animation then shows that instead of the Manage Working Folders dialog box, Windows calc opens. The trick is to simply rename the "target data" in question to control.exe.
I then ran a test of my own and instead of using the Windows folder Shell32 as the target, I saved a copy of the file calc.exe as control.exe under my user account in the profile folder Downloads/Test.
Then I entered the workfolders.exe command in a PowerShell console. Windows calc was also called (because the search for the .exe is done via the preset path from the above profile folder to the Windows folders) – with the program notepad.exe my short test did not work.
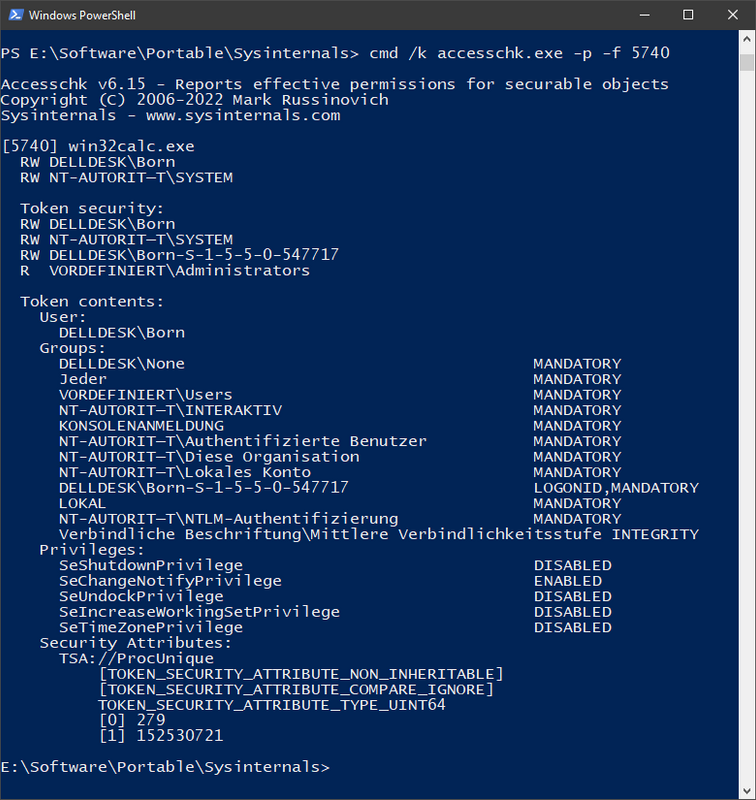
Subsequently, I used accessschk.exe from the Sysinternals tools to view the permissions of the calc.exe process in question. If I am not completely misinterpreting, an increase in permissions still requires approval via User Account Control. But the situation may allow the launch of malware by chaining other applications, without security software possibly not noticing – because they trust workfolders.exe.