[German]December 2023 patch day from Microsoft has revealed problems on Windows Server systems where ESET File Security v9.0.12013.0 (now called "ESET Server Security") is used. Due to the restart required after the update installation, the ESET antivirus solution may then fail to work. A message then appears stating that various protection protection functions are deactivated. The cause is an expired certificate. A blog reader informed me about the problem and provided a workaround. I'll post the facts here in the blog – perhaps it will help those affected.
[German]December 2023 patch day from Microsoft has revealed problems on Windows Server systems where ESET File Security v9.0.12013.0 (now called "ESET Server Security") is used. Due to the restart required after the update installation, the ESET antivirus solution may then fail to work. A message then appears stating that various protection protection functions are deactivated. The cause is an expired certificate. A blog reader informed me about the problem and provided a workaround. I'll post the facts here in the blog – perhaps it will help those affected.
ESET File Security
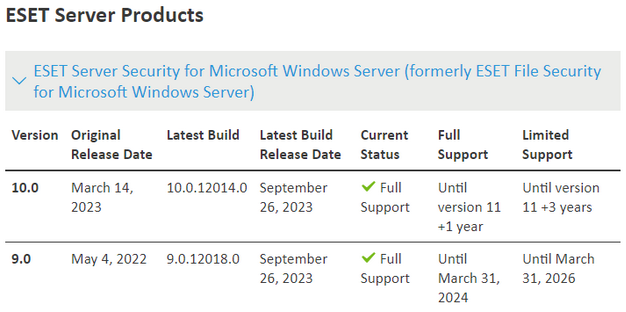
If I have seen it correctly, "ESET File Security" is the old name for a product that is now distributed as "ESET Server Security for Microsoft Windows Server" in version 10.x (see table below). However, the download file names still contain the term efsw.
ESET Server Security is an integrated solution that, according to the manufacturer, was developed specifically for Microsoft Windows Server environments. ESET Server Security offers effective and secure protection against various types of malware with two types of protection: malware protection and spyware protection. The product is available for Windows Server 2012 / R2 and Windows Server 2016 – 2022. According to the table above, the version is still in support until March 31, 2026 and was last updated on September 26, 2023 – version v9.0.12013.0 is dated July 7, 2022 according to this page.
Issues with ESET File Security v9.0.12013.0
German blog reader Sebastian contacted me today by e-mail because he encountered a problem in connection with ESET File Security v9.0.12013.0 in connection with the December 2023 patch day for Windows. He wrote to me that he manages a large number of customer systems that frequently use ESET as an antivirus solution, including ESET File Security version 9.0.12013.0.
December 12, 2023 was Microsoft's monthly Windows patch day, and according to Sebastian, a large number of systems therefore rebooted "tonight" (i.e. from December 12 to 13, 2023).
On the morning of December 13, 2023, Sebastian's customers experienced a very specific error pattern on the servers on which ESET File Security was installed. The Windows servers restarted due to the update installation and were still working. On all Windows Server systems from 2016 onwards, on which ESET File Security version v9.0.12013.0 is installed, ESET goes on strike after the restart. The security solution reports that various protection functions are deactivated:
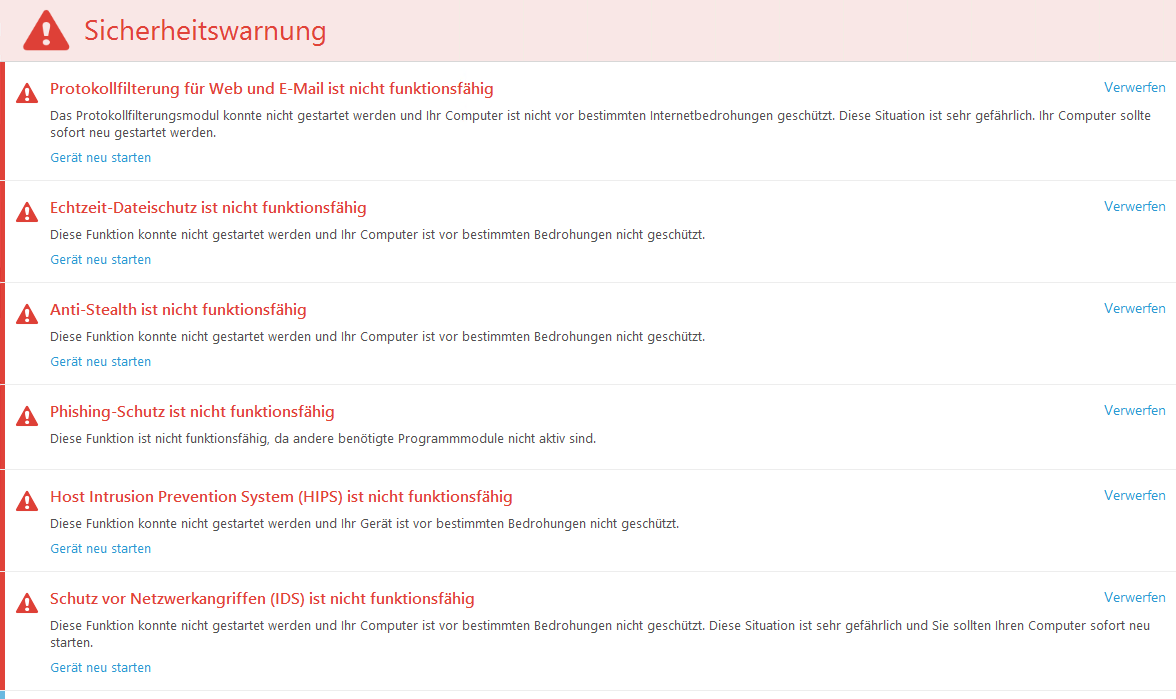
ESET File Security v9.0.12013.0 warning; click to zoom
According to the reader, a restart does nothing. And the built-in update function to update ESET to a new version via central management (ESET PROTECT) does not work either.
The reader initially thought that the cause was due to the latest Windows updates. However, someone had already reported the problem in the ESET forum this Monday (December 11, 2023), i.e. before the patch day. There the upgrade to ESET Server Security 10 failed and after the restart the security solution was broken. Ergo, the effect described above that the security solution generates a security warning is not related to the Windows update, but only to the required system restart.
Certificate expired – a fix
In the forum thread, the ESET employee and moderator describes that the cause is that the SHA256 Entrust certificate has expired and the ESET version in question cannot verify the new certificate.
The Entrust certificate expired on December 7. Only ESET File Security for Windows v9.0.12018 and newer have drivers that can verify the new certificate.
Since an ESET installation in this state does not allow a remote update, according to the blog reader, all affected ESET systems must be touched manually. A technical support employee suggested the following procedure to the reader:
- Deactivate the Host-based Intrusion Prevention System (HIPS) in the ESET installation
- Restart the server
- The ESET version can now be updated and the ESET update shall install
- Restart the system again
- Then reactivate HIPS – another restart is required for this to be active
- Restart the server again
This approach seems to work, writes the reader, who has just successfully tested it with a system. According to the blog reader, he has learned from ESET that the company is currently receiving a lot of feedback/enquiries about this behavior.