 [German]Security provider Bitdefender has informed me that security researchers in its labs have found vulnerabilities in Bosch BCC100 thermostats. Hackers can use these vulnerabilities to take control of such smart thermostats and gain access to smart home networks. The experts at Bitdefender Labs have described a specific possible attack on smart thermostats from the manufacturer Bosch in a study.
[German]Security provider Bitdefender has informed me that security researchers in its labs have found vulnerabilities in Bosch BCC100 thermostats. Hackers can use these vulnerabilities to take control of such smart thermostats and gain access to smart home networks. The experts at Bitdefender Labs have described a specific possible attack on smart thermostats from the manufacturer Bosch in a study.
Bosch BCC100 thermostats
Smart thermostats play an important role in realizing energy efficiency and sustainability, saving electricity costs and increasing living comfort in the smart home. The demand for Internet of Things solutions has therefore given rise to a broad market with various manufacturers and a large ecosystem of hardware and technologies. This also results in new security gaps.
The Bosch BCC100 (stands for Bosch Connected Control 100) is an intelligent room thermostat that can be accessed via Wi-Fi. With the Bosch Connected Control 100 Wi-Fi thermostats, heating and air conditioning in the home can be controlled on demand and from anywhere, as the manufacturer writes here. I have seen the thermostats for 150 US dollars on Amazon – and there is an app to control the settings.
Vulnerabilities in the BCC100
As part of an ongoing program, Bitdefender checks widely used IoT hardware for vulnerabilities and security risks. This also included samples of the Bosch BCC 100 thermostat. Bitdefender Labs discovered vulnerabilities (vulnerability CVE-2023-4972) in this widely used Bosch BCC100 thermostat.
Hackers can send commands to the thermostat via the Wi-Fi microcontroller, which acts as a network for the logical microcontroller, and also install malicious firmware updates. Attackers are also able to intercept data traffic, jump to other devices or carry out other actions.
The identified attack possibilities affect SW version 1.7.0 – HD version 4.13.22. Bitdefender informed Bosch about the issue on August 29, 2023. The manufacturer closed the vulnerability in production on November 11, 2023. Users should urgently check whether the updated firmware is installed on their thermostats.
Weak points in the thermostat network
The thermostat has two microcontrollers that work together (see illustration). The controller outlined in yellow is a Hi-Flying Chip HF-LPT230 microcontroller with implemented Wi-Fi functionality. This chip acts as a network gateway and proxy for the logical microcontroller, the STMicroelectronics STM32F103 chip marked in red in the illustration.
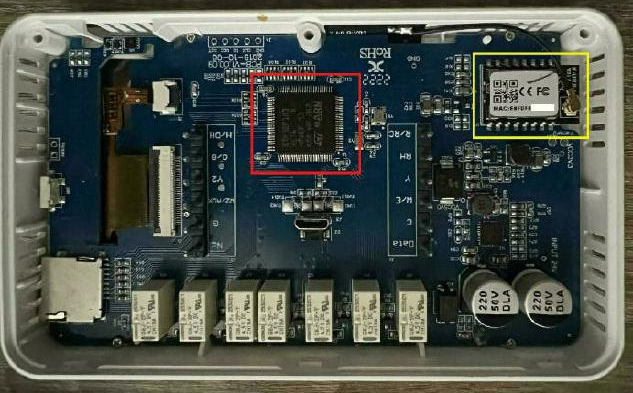
Interior view of the Bosch BCC 100 thermostat, photo: Bitdefender
Using the UART protocol, the STM chip transmits data to the Wi-Fi chip, which establishes the actual connection to the servers. The STM chip itself cannot communicate with the network and leaves communication with the Internet to the Hi-Flying Wi-Fi chip.
The Wi-Fi chip also communicates via TCP port 8899 in the Local Area Network (LAN) and mirrors each message via this port directly to the logical STM microcontroller via UART Data Bus. If the message format is correct, the WiFi microcontroller cannot distinguish malicious messages from legitimate data packets from the cloud server. This also allows attackers to send commands to the thermostat – up to and including malware-infected updates of the device.
Updating with third-party firmware
The thermostat communicates with the connect.boschconnectedcontrol.com server with JSON-encoded payloads via a web socket. The server sends the packets unmasked so that hackers can easily imitate them. Via the command "device/update" to port 8999, the device learns about a new update and initiates the supposedly legitimate firmware update.
The thermostat asks the cloud server for the update. Despite an error code response from the server, if there is no legitimate update, devices with an unclosed vulnerability will accept a fake response with the details of the malicious new firmware:
\x81\x7e\x01\x33{"error_code":"0","cmd":"server/fireware",
"device_id":"<device mac>","timestamp":"<unix timestamp>",
"model":"BCC101","version":"<fw version>","url":"<firmware URL>",
"size":"<firmware size>","isize":"0","pic_pos":"2930",
"md5":"<firmware md5>","type":0,"release_date":"1111-11-11"}
The transmitted packet provides the source for the firmware download, its size and an MD5 checksum of the firmware file as well as the new version. The authenticity of a firmware update is not validated. If all conditions are met, the thermostat requests the cloud server to download the firmware and send it via a web socket:
{"cmd":"server/deviceUpdate","device_id":"<device mac>",
"timestamp":"<unix timestamp>","url":"<firmware URL>","pindex":"0"}
The URL must be accessible via the Internet, as the cloud server performs the download. Once the file has been received by the hardware, the thermostat updates itself. In the event of a malicious attack, the device would now be completely compromised.
Protection of IoT hardware
IoT in the smart home network increases the attack surface for hackers and is therefore just as much an IT security risk as PC systems, smartphones, routers or smart TVs. Users should therefore monitor their IoT hardware carefully and isolate it from the local network as much as possible. This enables a dedicated network for IoT devices alone.
Smart Home Scanner can scan and identify hardware with connectivity and report devices with vulnerabilities. Users of IoT hardware should always check for the latest firmware and publish upgrade versions supplied by the manufacturer as soon as they are released.
A good option for smart home security is also a network solution for cybersecurity that is integrated into routers. The full report is available for download. Users should check that their thermostats are using the latest Bosch firmware.



