[German]Since February 13, 2024, a vulnerability CVE-2024-21410 has been known, through which attackers can access NTLM hashes via Microsoft Exchange Server and then misuse them for NTLM relay or pass-the-hash attacks. I have now read that more than 28,500 Exchange servers are vulnerable via CVE-2024-21410. Administrators must therefore take action and secure their IT infrastructure. In this context, I also came across an analysis by Frank Carius, who sees the vulnerability not in the Exchange Server but in the IIS. So there is potentially much more affected.
[German]Since February 13, 2024, a vulnerability CVE-2024-21410 has been known, through which attackers can access NTLM hashes via Microsoft Exchange Server and then misuse them for NTLM relay or pass-the-hash attacks. I have now read that more than 28,500 Exchange servers are vulnerable via CVE-2024-21410. Administrators must therefore take action and secure their IT infrastructure. In this context, I also came across an analysis by Frank Carius, who sees the vulnerability not in the Exchange Server but in the IIS. So there is potentially much more affected.
Advertising
Vulnerability CVE-2024-21410
I have already covered CVE-2024-21410 here on the blog. In the article Microsoft Security Update Summary (February 13, 2024) I mentioned, that CVE-2024-21410 is a Microsoft Exchange Server Elevation of Privilege vulnerability that is classified as critical; with a CVEv3 score of 9.8. Successful exploitation of this vulnerability would allow an attacker to pass an NTLMv2 hash against a vulnerable server. NTLM2.0 hashes could be abused in NTLM relay or pass-the-hash attacks.
Administrators can activate Extended Protection (EP) in Microsoft Exchange Server to be protected against this type of attack. I wrote about this in the blog post Follow-up on CU 14 for Exchange 2019 and vulnerability CVE-2024-21410 (Feb. 2024). Alternatively, IT administrators can replace NTLM authentication with Kerberos authentication to prevent the risk of NTLM2.0 hashes being tapped in the first place.
German blog reader R.S. had written something about this in this GErman comment and pointed out that the NTLM hashes can only be siphoned from the outside if port 445 (SMB) in the firewall is open to the internet. This should not be the case in a good configuration. Microsoft has published a support article about Kerberos on Exchange 2013 titled Configuring Kerberos authentication for load-balanced Client Access servers. Here are two (German) articles from Frank Zöchling to change Exchange to Kerberos authentication.
Exchange 2013: Authentifizierung auf Kerberos umstellen
Exchange 2019: Kerberos Authentifizierung aktivieren
It's an IIS vulnerability
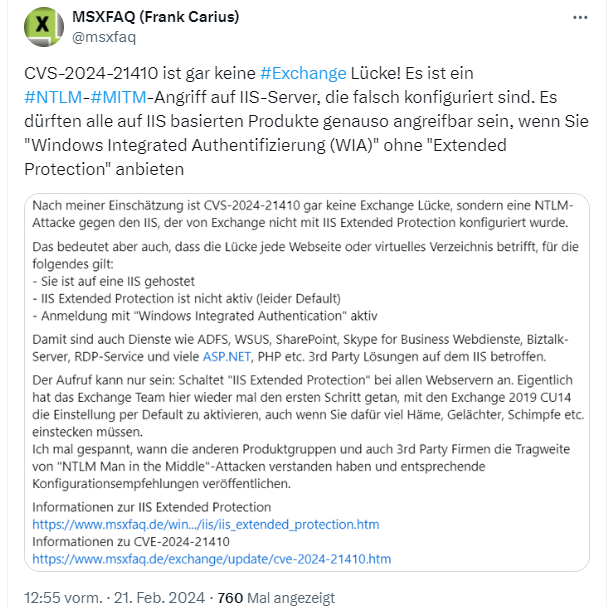
German expert Frank Carius has revisited the topic and also points out that CVE-2024-21410 is not actually an Exchange Server vulnerability. Instead, it is an NTLM attack to access the hashes on the Internet Information Server (IIS) used by Exchange Server.
Advertising
Frank points out his assessments in the above tweet and writes that the vulnerability applies to any website or virtual directory to which the following applies:
- It is hosted on an IIS
- IIS Extended Protection is not active (unfortunately default)
- Login with "Windows Integrated Authentication" active
According to Frank, this also affects services such as WSUS, SharePoint, Skype for Business web services, Biztalk server, RDP service and many ASP.NET applications, PHP etc. as well as 3rd party solutions on the IIS.
ADFS mentioned in the tweet should not be affected, as it uses HTTP.sys and does not require IIS. No EP can be activated there – this is mentioned in a comment within my German blog and also in a comment in a private German Facebook group.
He calls for "IIS Extended Protection" to be switched on for all web servers. Here are links to the two articles (in German) written by Frank Carius on the subject:
Informationen zur IIS Extended Protection
Informationen zu CVE-2024-21410
And here are two links to Microsoft support articles:
Description of the update that implements Extended Protection for Authentication in Internet Information Services (IIS)
Windows Extended Protection <extendedProtection>
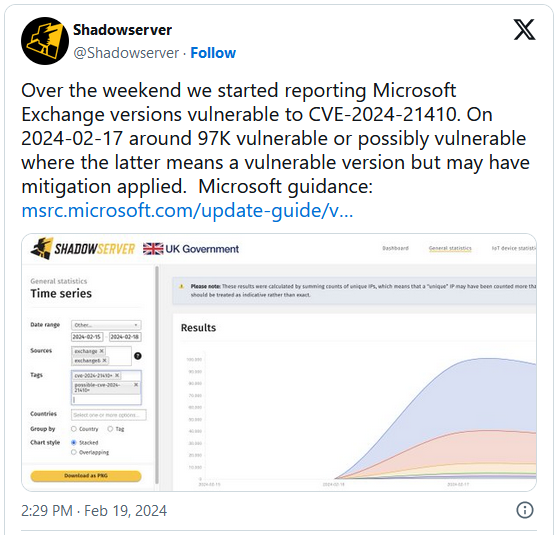
More than 28,500 Exchange servers vulnerable
With the above information, I would have said: The risk is limited, but I did the math without the administrators. The colleagues at Bleeping Computer report in this article that up to 97,000 Microsoft Exchange servers may be vulnerable to attacks via the CVE-2024-21410 vulnerability. At present, 28,500 servers have already been identified as vulnerable to the vulnerability, which is already being actively exploited by hackers to access hashes and evaluate permissions.
The above tweet from Shadowserver, lists the corresponding Exchange instances on this page. With almost 25,000 instances, Germany is well ahead of the USA.
Similar articles:
Microsoft Security Update Summary (February 13, 2024)
Exchange Server Cumulative Update CU 14 (February 13, 2024)
Follow-up on CU 14 for Exchange 2019 and vulnerability CVE-2024-21410 (Feb. 2024)
Advertising