 [German]It seems that products, that using OpenVPN servers, are now under (Brute Force) attacks. A blog reader contacted me by email the other day because he had observed strange behavior. His logs showed access attempts from the same IP addresses to the Synology OpenVPN server on his systems. It seems to him that the DDNS domains registered with Synology are being attacked. But I got now reports, that a other products with OpenVPN servers also see this access attempts from South Africa.
[German]It seems that products, that using OpenVPN servers, are now under (Brute Force) attacks. A blog reader contacted me by email the other day because he had observed strange behavior. His logs showed access attempts from the same IP addresses to the Synology OpenVPN server on his systems. It seems to him that the DDNS domains registered with Synology are being attacked. But I got now reports, that a other products with OpenVPN servers also see this access attempts from South Africa.
Synology NAS server and OpenVPN
Synology Inc. is a manufacturer of NAS servers with a wide range of products from small servers for private use to high-performance computers. All devices are supplied with their own Linux-based operating systems and are comparatively easy to configure. Synology now offers other products, which are described on the manufacturer's website.
Synology offers a VPN Server package that can be used to turn a Synology NAS into a VPN server. The user can then securely access shared resources on the local network of the Synology NAS remotely. By integrating common VPN protocols – PPTP, OpenVPN and L2TP/IPSec – VPN Server provides options for setting up and managing VPN services tailored to your individual needs.
The VPN server is based on OpenVPN, an open source solution for implementing the VPN service. The configuration of the package is described on this Synology page.
A reader observed access attempts
German blog reader Mario Cortes runs an IT service and uses in this context also Synology NAS servers in conjunction with the OpenVPN package. In his email, he wrote that he had noticed a strange behavior of the OpenVPN Server package on various Synology systems on 22, February 2024.
- He writes that it looks to him as if these OpenVPN packages are being attacked via the standard UDP port 1194.
- According to his observations, these are always the same IP addresses: 197.148.68.41 and 197.148.64.126.
Mario has sent me the following screenshot with the extract of the log that recorded these access attempts during the night. They take place at intervals of minutes, meaning two access attempts with a pause.
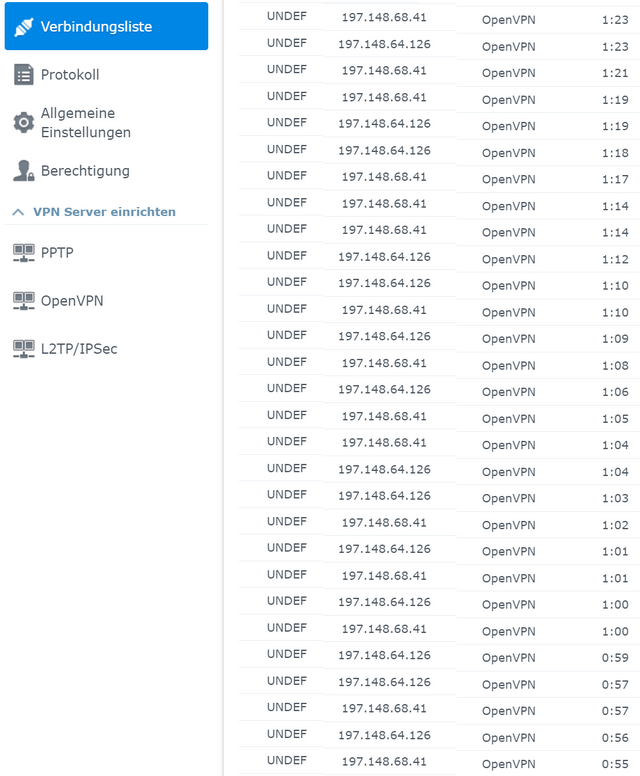
The IP address 197.148.68.41 is given as "Cape Town, Western Cape, South Africa" on this website. The second IP address 197.148.64.126 is located in Johannesburg, South Africa. Mario wrote to me that it seems that the DDNS domains registered with synology.me are under attack.
I did a quick search – someone in the Synology community described such accesses in 2018. Question to the Synology users who use the OpenVPN package: Can you confirm this observation that Mario made on various systems.
Mario writes: "Maybe this is worth a blog post", which has been done (thanks for the hint). By the way, he found a simple workaround and wrote: You can remedy this by changing the default port 1194 to 1196, for example.
More reports – OpenVPN is the target
Later, a 2nd German blog reader, Maximilian, notified me on Facebook in a private message that a customer of his was also affected. Wednesday afternoon (21 Feb. 2024) this system started with access attempts. However, two other IPs 164.160.91.55/56 are listed there. He has already changed the default port since the beginning – but according to him, it doesn't seem to help.
Other readers reported also such access attempts from South Africa. Sascha reported that he also experiencing these attacks on port 1194 on the SecurePoint routers and on the OPNSense.
Mario found later the reddit post Possible DDoS / brute force attack on *.synology.me OpenVPN, where a user also reported this. There is also a WatchGuard KB article
Unknown authentication attempts against Mobile VPN with SSL from a user named "test" or other random users dealing with this topic.
Try to use geo blocking
Sascha and others have now activated GeoBlocking (geo fencing) everywhere, to stop these access attempts. Search for GeoIP, there are articles for ONPsense, and other products. Or block the attempts within your enterprise firewall.



