[German]There is a vulnerability in Windows that allows attackers to infect a system and search a network. Security researchers from Elastic uncovered this new infection technique in mid-June 2024 and dubbed it GrimResource. I was aware of this at the time, but have only just got around to writing about it here in the blog (due to my vacation).
[German]There is a vulnerability in Windows that allows attackers to infect a system and search a network. Security researchers from Elastic uncovered this new infection technique in mid-June 2024 and dubbed it GrimResource. I was aware of this at the time, but have only just got around to writing about it here in the blog (due to my vacation).
Office macros & co. mitigated as an attack vector
Microsoft is making some efforts to plug vulnerabilities that can be used for attacks. Historically, there have been many gateways for attackers. For security reasons, Microsoft Office macros are deactivated by default for documents originating from the Internet. This renders an attack vector ineffective.
Cyber attackers now rely on other infection vectors such as JavaScript, MSI files, LNK objects and ISOs, so these have become much more popular. However, the situation here is that administrators have already put up barriers or these attack techniques are closely scrutinized by security solutions and have a high probability of detection. A previously largely unknown attack technique would therefore have a "high potential".
GrimResource and the Windows .msc XSS vulnerability
North Korean attackers appear to be using just such an attack technique. Security researchers from Elastic Security Labs have discovered this new infection technique, which they call GrimResource. The attack exploits .msc files and allows attackers to execute full code in the context of mmc.exe. It is enough to trick a user into opening a specially crafted .msc file by double-clicking on it. An example exploited by the Actor GrimResource thread was first uploaded to VirusTotal on June 6, 2024.
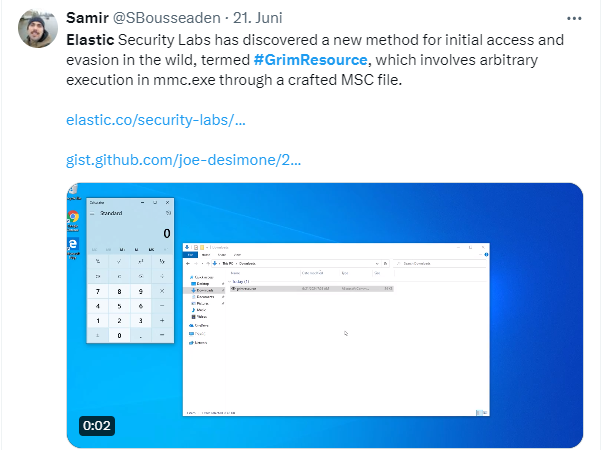
I had seen the following tweet about this issue (and there was this comment), but had no way to respond here on the blog. The details were published by Elastic Security Labs in the blog post GrimResource – Microsoft Management Console for initial access and evasion.
XML file abused
Elastis has published a file on Github with a proof of concept of this attack vector. The file already shows where the problem could lie, because .msc files are XML documents. Here is an excerpt from the PoC file:
<?xml version="1.0"?><MMC_ConsoleFile ConsoleVersion="3.0" ProgramMode="UserSDI"> <ConsoleFileID>a7bf8102-12e1-4226-aa6a-2ba71f6249d0</ConsoleFileID> <FrameState ShowStatusBar="false"> <WindowPlacement ShowCommand="SW_HIDE"> <Point Name="MinPosition" X="-1" Y="-1"/> <Point Name="MaxPosition" X="-1" Y="-1"/> <Rectangle Name="NormalPosition" Top="0" Bottom="0" Left="0" Right="0"/> </WindowPlacement> </FrameState> <Views>
If you save the source code from the above GitHub page in a text file and rename it to .msc, you have a file that can be loaded into mmc.exe. And mmc.exe then implements all instructions from the .msc file. If you click on the screenshot above, you can watch a video on X that shows that opening the .msc file by double-clicking opens a dialog box and the Windows computer. A look at the .XML structure reveals that it also has a BinaryStorage with binary data that can be used by the .msc file.
Details of the attack vector
The Elastic arcticle describes the attack vector in more detail. The GrimResource attack vector exploits an old XSS vulnerability in the apds.dll library. By adding a reference to the vulnerable Authentication Protocol Domain Support (APDS) resource in the corresponding StringTable section of a crafted MSC file, attackers can execute arbitrary Javascript in the context of mmc.exe. Attackers can combine this technique with DotNetToJScript to achieve arbitrary code execution.
For interested readers, the Elastic article describes the GrimResource exploit in detail. The colleagues from Bleeping Computer, who dealt with the topic promptly, quote in this article that the vulnerability in Windows has not yet been patched.
MMC and UAC bypassing
What struck me when reading the above sources is that the particular risk of .msc files is not addressed. Such .msc files and mmc.exe can be misused for UAC bypassing attacks so that user account control can be bypassed and administrative rights to standard accounts can be obtained. I pointed this out in 2017, for example, in my German blog post Erebus Ransomware und die ausgetrickste UAC.
How can you protect yourself?
Administrators can protect themselves for GrimResource by checking whether the execution of .msc files from Internet sources (Mark of the Web flag, MotW) is set, can be prevented. The Elastic Labs have compiled some information (Indicator of Compromise, IoCs) on this GitHub page (here is the Elastic Protection Rules collection, see also this tweet) and the colleagues from Bleeping Computer provide further information here.