[German]I'm posting a topic here in the blog that still has "a few days to go" but could have very unpleasant consequences. In the fall of 2026, a certificate in Windows will expire, which ensures that Secure Boot can be executed in the UEFI. At that time, the certificate was valid for 15 years, but all machines that are not updated will no longer be able to start in Secure Boot mode by the deadline.
[German]I'm posting a topic here in the blog that still has "a few days to go" but could have very unpleasant consequences. In the fall of 2026, a certificate in Windows will expire, which ensures that Secure Boot can be executed in the UEFI. At that time, the certificate was valid for 15 years, but all machines that are not updated will no longer be able to start in Secure Boot mode by the deadline.
Windows and the Secure Boot CA
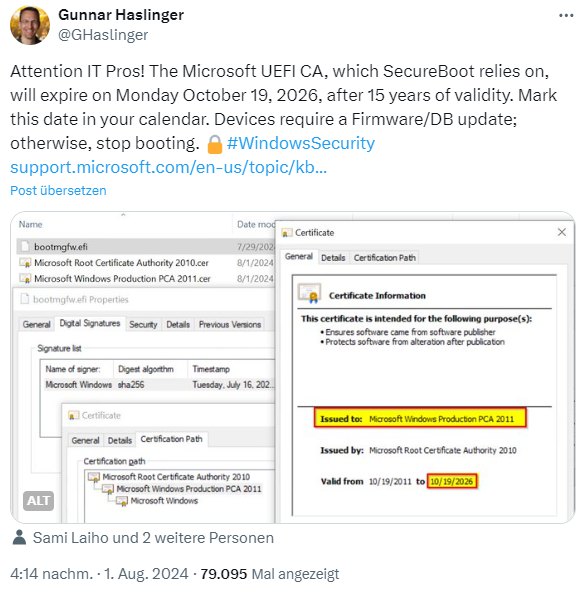
I came across the following tweet by Gunnar Haslinger a few days ago and am posting it here on the blog today for your information.
The issue at hand is described in a few words. Microsoft uses a UEFI certificate that is stored in a database. The Secure Boot propagated by Microsoft in Windows accesses this certificate to check its integrity. Secure Boot therefore depends on the validity of this certificate. If the certificate in the bootmgfw.efi file on the UEFI partition is invalid, the machine can no longer start in Secure Boot.
The Windows Production PCA 2011
However, the certificate used so far was issued a long time ago, specifically in 2011, and will expire on Monday, October 19, 2026, after 15 years of validity. Machines that use Secure Boot and have not been updated by this date will no longer be able to start. This is likely to affect Windows systems in particular, which do not receive updates via the internet.
The Black Lotus problem
With the May 2023 security updates, Microsoft has attempted to close the vulnerability in Secure Boot that is being exploited by the hacker group BlackLotus and its UEFI bootkit. The vulnerability CVE-2023-24932 relates to a vulnerability in the Secure Boot used in Windows operating systems, which allows untrusted software to be executed during the boot process.
I wrote about this topic in the blog post BlackLotus UEFI bootkit bypasses Secure Boot in Windows 11. And in the German article Windows und das (BlackLotus) Secure Boot-Desaster: Wie ist bei euch der Status? I discussed the problem of administrators having to intervene manually to secure the Secure Boot.
New Windows UEFI CA 2023
To solve the problem with the expiring certificate, Microsoft has provided the update KB5025885 for protection (see KB5025885: Secure boot hardening against vulnerability CVE-2023-24932 (Black Lotus) from May 2023). There is also a support article on update KB5025885, which contains the advice to install the Windows security update of July 9, 2024 or a later cumulative security update under Windows in order to provide the required safeguards against Black Lotus.
This blog post also contains a note that a new certificate (Windows UEFI CA 2023) will be provided with the update to replace the old Windows Production PCA 2011. Administrators in enterprise environments will find corresponding instructions in the support article for KB5025885 as to which additional steps need to be carried out. Anyone who provides their Windows systems with protection against Black Lotus and the Secure Boot vulnerability CVE-2023-24932 is also prepared for the scenario of an expiring UEFI certificate outlined above.
In 2024, Microsoft then carry out various hardening measures, which I outlined in the blog post Update on Windows hardening in 2024/2025 – March 2024.
Similar articles:
BlackLotus UEFI bootkit bypasses Secure Boot in Windows 11
KB5025885: Secure boot hardening against vulnerability CVE-2023-24932 (Black Lotus)
Update on Windows hardening in 2024/2025 – March 2024