 [German]Security researchers from the Trend Micro Zero Day Initiative (ZDI) point to a 0-day vulnerability ( ZDI-CAN-25373) in Windows, which has probably been exploited by 11 state-supported hacker groups from North Korea, Iran, Russia and China since 2017. Microsoft rated the vulnerability in shortcut files as "not sufficiently" critical in September 2024 and rejected a patch.
[German]Security researchers from the Trend Micro Zero Day Initiative (ZDI) point to a 0-day vulnerability ( ZDI-CAN-25373) in Windows, which has probably been exploited by 11 state-supported hacker groups from North Korea, Iran, Russia and China since 2017. Microsoft rated the vulnerability in shortcut files as "not sufficiently" critical in September 2024 and rejected a patch.
Peter Girnus and Aliakbar Zahravi from the Trend Micro Zero Day Initiative (ZDI) point out the issue in the blog post ZDI-CAN-25373: Windows Shortcut Exploit Abused as Zero-Day in Widespread APT Campaigns. They write that both state-sponsored and cybercriminal groups are extensively exploiting a Windows .lnk file vulnerability (ZDI-CAN-25373) that allows the execution of hidden commands.
According to the article, the Trend Zero Day Initiative™ (ZDI) has now identified almost 1,000 malicious .lnk files that exploit the ZDI-CAN-25373 vulnerability. The vulnerability allows attackers to use manipulated shortcut files to execute hidden malicious commands on a victim's computer.
Attacks using the shortcut vulnerability, source Trend Micro
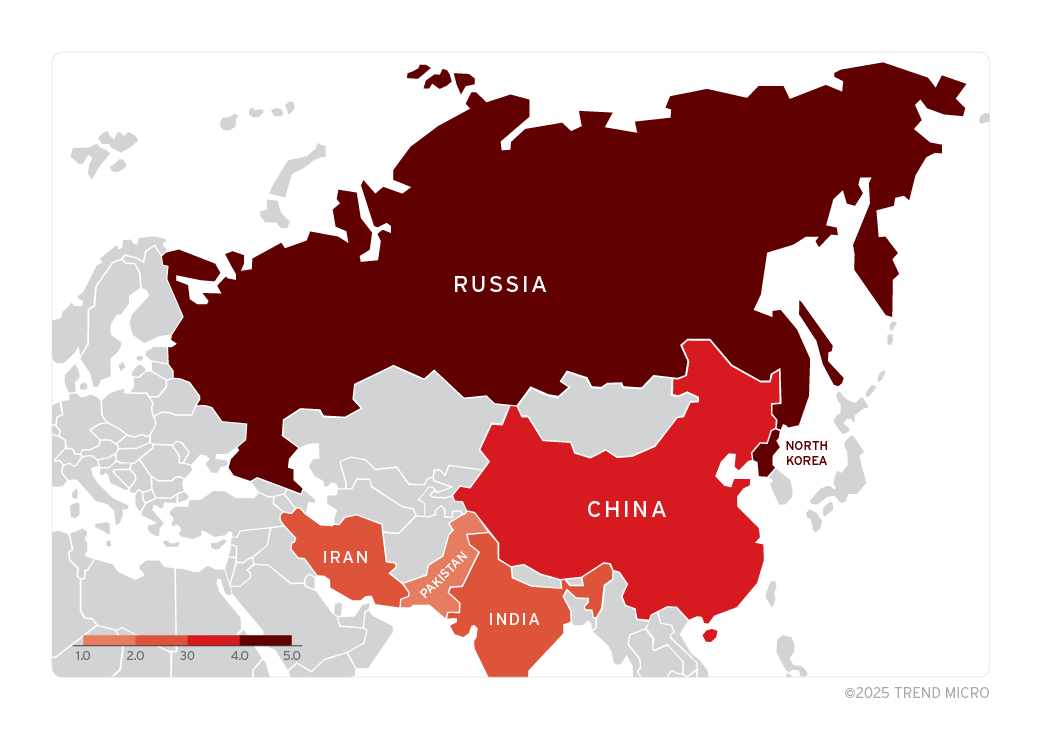
The map above shows countries from which 11 state-sponsored hacker groups from North Korea, Iran, Russia and China have exploited the vulnerability in campaigns, probably since 2017, for attacks. The organizations affected are from the government, finance, telecommunications, military and energy sectors in North America, Europe, Asia, South America and Australia.
Attackers use hidden command line arguments in .lnk files to execute malicious payloads. This makes it more difficult to detect attacks. By exploiting ZDI-CAN-25373, companies are exposed to a significant risk of data theft and cyber espionage, the security researchers write.
Trend Micro's recommendation is that companies should immediately scan their networks for the ZDI-CAN-25373 vulnerability and take security precautions. They should look out for suspicious .lnk files and ensure that comprehensive endpoint and network protection measures are in place to detect and combat this threat.
On March 18, 2025, the Zero Day Initiative published the security alert ZDI-25-148: (0Day) Microsoft Windows LNK File UI Misrepresentation Remote Code Execution Vulnerability vand assigned the vulnerability a CVSS score of 7.0. So far, this vulnerability in Windows has not been patched by Microsoft – and there are no known plans for a patch.
Technical details on the vulnerability in shortcut files can be found in the ZDI article. Given the current situation, a sensible mitigation strategy to mitigate the vulnerability is to restrict the interaction of .lnk files with applications on Windows. Trend Micro also writes that customers are protected against possible attempts to exploit the vulnerability by rules and filters published in October 2024 and January 2025.
Bleeping Computer has published a Microsoft statement on the subject here. They point out that Microsoft Defender also has detection capabilities to detect and block this threat activity. And Smart App Control offers an additional layer of protection by blocking malicious files from the Internet.
Microsoft also recommends its customers to be careful when downloading files from unknown sources. In principle, a warning should also appear if a potentially harmful file is detected. It is also said that Microsoft is considering fixing this problem in a future feature release.



