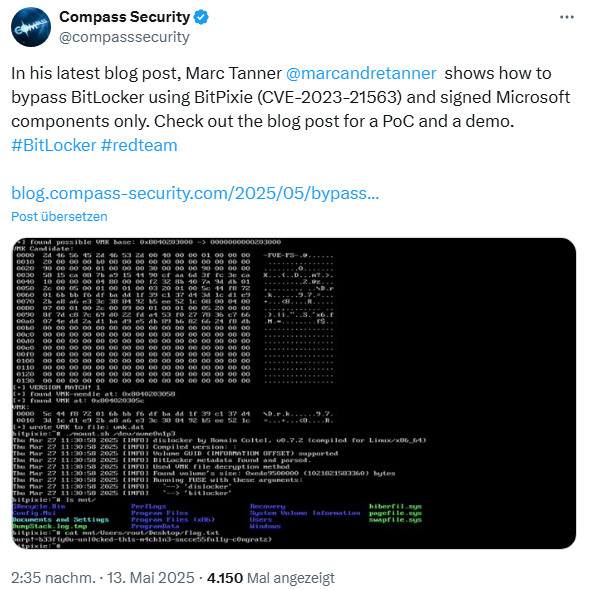
[German]
[German]
The Bitlocker encryption used by Microsoft for Windows for data storage devices can be bypassed by software via the Bitpixie vulnerability (CVE-2023-21563) if certain boundary conditions apply. A security researcher has shown how the master key can be read from the RAM and used for decryption within minutes without a hardware hack if pre-boot authentication is missing under Windows. The Bitpixie attack is not new, but the chosen method is possible with Windows components – and the exploit is public as a PoC. Here is an overview.
Translated with DeepL.com (free version)
On May 13, 2025, Patchday, Windows users once again ran into the Bitlocker recovery key query – I reported this in the blog post Microsoft confirms Bitlocker boot problems after Windows 10/11 May 2025 update. However, none of this is new, as the following explanations and the links to articles at the end of the post show. A German blog reader then commented on the above article that the Bitlocker encryption had been broken. Other comments pointed out that the problem had been known for some time. Here is a brief outline of what it is all about.
38c3: Bitlocker Bitpixie vulnerability (CVE-2023-21563)
Let me jump back a few months, to the year 2024. On December 28, 2024, there was a presentation at the 38C3 congress of the Chaos Computer Club entitled Windows BitLocker: Screwed without a Screwdrive. Security expert Thomas Lambertz showed how Microsoft's Bitlocker encryption can be overridden by "downgrading" a patched vulnerability. This is the way in which secret services or law enforcement agencies can access encrypted data with the help of forensics companies such as Cellebrite.
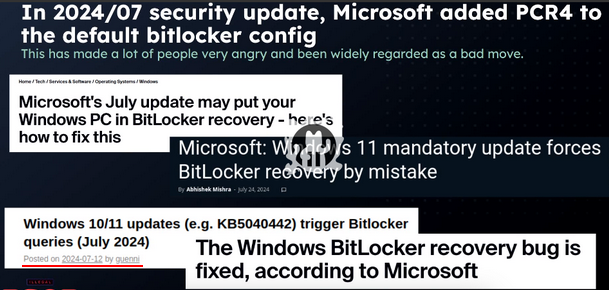
Problems with Bitlocker, screenshot at 45:13 from the presentation at 38C3, including reference to my post Windows 10/11 updates (e.g. KB5040442) trigger Bitlocker queries (July 2024)
I reported on this in the blog post 38C3: Bitlocker bypassed via vulnerabilities (Dec. 2024). While scrolling through the post, I came across the above slide, which includes the English version of one of my blog posts on Bitlocker issues.
Proof of concept for the BitPixie vulnerability CVE-2023-21563
I came across the issue that German users pointed out in the comments here also on X the other day.
Security researcher Marc Tanner has described in the blog post Bypassing BitLocker Encryption: Bitpixie PoC and WinPE Edition how he can bypass Bitlocker using software. Tanner was triggered by the above-mentioned presentation by Thomas Lambertz on the subject.
Although Thomas Lambertz presented the principle of the Bitpixie attack at 38C3 and described it in this blog post in January 2025, he did not publish his exploit. Marc Tanner used the information from Lambertz to develop a Bitpixie Linux Edition exploit with his Red Team. He wrote: "In order to fully understand the attack, reproduce the original research and demonstrate the concrete impact for our customers, I set out to develop a public proof of concept."
Tanner writes that the exploitation of the abused Bitpixie vulnerability is non-invasive and does not require permanent device modifications or a complete hard disk image. This allows for quick (~5 minutes) compromise and more flexible integration into certain social engineering scenarios.
Basically, the machine to be cracked must be booted in WinRE and the boot loader replaced with a vulnerable variant. Thomas Lambertz has then loaded a Linux that scans the memory for Bitlocker master keys.
Marc Tanner has, as far as I understand it, managed the attack under WinPE by using the same mechanisms but using signed Microsoft Windows components. He has published his WinPmem-BitLocker on GitHub with a description.
Theoretically, the exploit from the proof of concept (PoC) should therefore be applicable to all affected devices as long as they trust the Microsoft Windows Production PCA 2011 certificate that is used to sign the vulnerable boot manager. However, this certificate will be replaced by Microsoft as it expires in 2026 (see the German blog post Frage: BlackLotus-Schwachstelle und ablaufendes UEFI-Zertifikat – was droht uns? (Question: BlackLotus vulnerability and expiring UEFI certificate – what is the threat?) and the articles on BlackLotus in the link list below).
In practice, the exploit appears to be somewhat less reliable than its Linux-based counterpart, writes Tanner (Lenovo probably runs its own boot on its systems). Nonetheless, Tanner believes the automation scripts provided are hopefully useful for investigating whether devices are affected.
What helps against the attack?
It was mentioned in my German blog post by Marc Heitbrink, but also by Marc Tanner in his article. The Bitpixie vulnerability – and hardware- and software-based attacks in general – can be mitigated by enforcing pre-boot authentication. This means that an additional PIN and/or key file is requested for authentication at boot time
Conclusion: The attack that has now become known is not new, but a proof of concept that administrators can test in their own systems if necessary. The workaround against these attacks has also been mentioned. Details can be found in the linked articles.
Similar articles:
Windows 10/11 updates (e.g. KB5040442) triggers Bitlocker queries (July 2024)
Windows 10/11: May 2025 updates triggers Bitlocker Recovery and BSODs
Microsoft confirms Bitlocker boot problems after Windows 10/11 May 2025 update
Windows Bitlocker recovery key query bug fixed by August 2024 updates
KB5025885: Secure boot hardening against vulnerability CVE-2023-24932 (Black Lotus)
Frage: BlackLotus-Schwachstelle und ablaufendes UEFI-Zertifikat – was droht uns?
Windows 10/11 KB5053484: Neues PS-Script für Zertifikate in Boot-Medien