[German]In June 2025, it became known that there are vulnerabilities in the firmware of almost 700 printer models from Brother and other manufacturers. There are now reports that attackers are using these vulnerabilities to attack printers that have not been updated via firmware updates.
[German]In June 2025, it became known that there are vulnerabilities in the firmware of almost 700 printer models from Brother and other manufacturers. There are now reports that attackers are using these vulnerabilities to attack printers that have not been updated via firmware updates.
What are the printer vulnerabilities?
Security researchers from Rapid 7 have taken a closer look at the firmware of various printer models to examine them for vulnerabilities. The 0-Day research project primarily examined multifunction printer (MFP) models from the manufacturer Brother. The comprehensive analysis was later extended to include a number of models from other manufacturers.
At the end of this investigation, eight (8) vulnerabilities in the firmware of various printers were known, of which one vulnerability received a CVSS score of 9.8. The list of vulnerabilities can be found in the blog post Vulnerabilities in 689 Brother and other printer models (June 2025).
- CVE-2024-51978 (CVSS score of 9.8) allows an unauthenticated attacker to generate a default administrator password for the printer.
- CVE-2024-51977 (CVSS score of 5.3) allows an unauthenticated attacker to remotely spy on the serial number of the target device along with several other sensitive pieces of information.
Knowledge of the serial number of a target device (Retrievable via CVE-2024-51977) is required to exploit the authentication bypass vulnerability CVE-2024-51978. If printers listed in the Rapid 7 post Multiple Brother Devices: Multiple Vulnerabilities (FIXED) are accessible to attackers, a firmware update is strongly recommended.
Attacks on printers have become known
CrowdSec, which collects "crowdsourced" data via a tool, reports in a LinkedIn post CVE-2024-51977: The New Vulnerability Turning Printers into Botnets from July 21, 2025 that they have now observed specific attacks via the vulnerabilities CVE-2024-51978 and CVE-2024-51977.
It is said that CrowdSec Network has observed a wave of attack attempts on the CVE-2024-51977 vulnerability (see figure below). The article mentions that Rapid7 has also discovered such attack attempts. The attacks target over 750 different printer models from Brother, FUJIFILM and Toshiba.
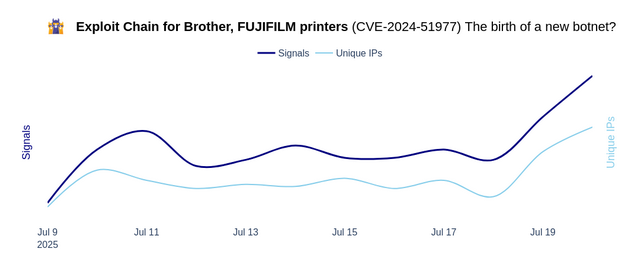
Attacks on printers, Souce: CrowdSec Network
The first attack attempts date back to July 4, 2025 (Independence Day in the USA) and continued in the following weeks. There has been an increase since July 18/19, 2025, although the absolute number of detected attempts is not specified.
However, CrowdSec Network writes that most devices cannot be fully patched. It is therefore assumed that this campaign will continue, as botnets will use the vulnerability for their exploit chains.
The only thing administrators can do here is to isolate the printers concerned in the network as far as possible. Reasons why printers may be accessible from outside would be: Ports opened by the printer software to retrieve printer statuses for subscriptions or to query firmware statuses (etc.). I also suspect that attacks can be carried out from the inside via malware (if necessary even by script).
CrowdSec Network also advertises in its LinkedIn post that people should install their Crowdsec CTI to block the attackers' IPs as well as the Crowdsec Web Application Firewall.