[German]Since Windows 11 24H2 and Windows Server 2025, there have been problems (Error 500) when testing client certificates with ASP.NET against IIS Express. The reason for this is compatibility issues with TLS 1.3, which only occur with the above-mentioned operating systems. However, Microsoft is not expected to release a fix.
[German]Since Windows 11 24H2 and Windows Server 2025, there have been problems (Error 500) when testing client certificates with ASP.NET against IIS Express. The reason for this is compatibility issues with TLS 1.3, which only occur with the above-mentioned operating systems. However, Microsoft is not expected to release a fix.
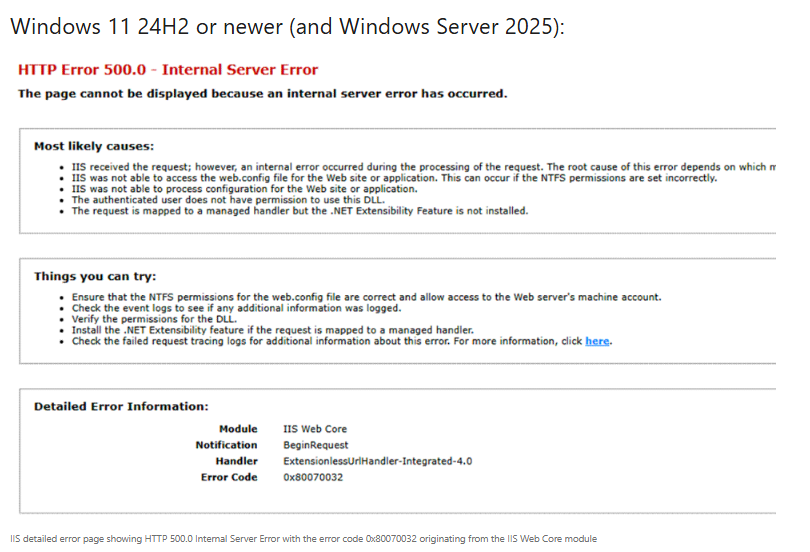
Error 500 in IIS Express
Starting a web app (ASP.NET) in IIS Express may result in an error message. While this is still reasonably meaningful with "can't reach the page …" in Windows 10 or up to Windows Server 2022, Windows 11 24H2 and Windows Server 2025 return an Error 500. Error code 0x80070032 (ERROR_NOT_SUPPORTED) may be reported.
Microsoft addressed this issue in a TechCommunity Addressing TLS 1.3 Compatibility Issues in IIS Express on Windows 11 – I came across it a few days ago in this neowin.net article.
Microsoft points out that the above problems are likely to occur more frequently with the end of Windows 10 support. This is because this problem has always been present in Windows 11 and Windows Server 2025 is also affected.
The cause is most likely that the applicationhost.config file (for IIS Express) was manually modified at some point in the past and contains an XML statement of the following type.
sslFlags="SslNegotiateCert"
The same problem could also occur with SslRequireCert; neither option is set in the file. The options (SslNegotiateCert or SslRequireCert) instruct IIS Express to search for a client certificate at the beginning of request processing.
Unfortunately, this does not currently work on Windows 11 (or Windows Server 2025) without a workaround. The reason for this is the default use of TLS 1.3 for incoming and outgoing traffic on Windows 11. However, TLS 1.3 does not support a TLS concept known as "renegotiation."
Microsoft provides several workarounds to fix the problem in its Techcommunity post. One measure is to disable TLS 1.3 for incoming/server sessions on the workstation. The advantage is that this workaround does not require any code or changes to the app or project and only affects incoming TLS traffic (which is usually minimal on workstations). Outgoing traffic from your browsers or other clients is not affected. The disadvantage is that this applies to the entire computer. According to Microsoft, this should not be a problem either, as nothing on a workstation should be specifically dependent on incoming TLS 1.3. I have no idea how many people are affected by this scenario.