 [German]The security updates for Windows released on October 14, 2025 cause the preview of files (e.g., PDF documents or Office documents) in Explorer to be blocked in some cases. I described the problem in Part 1. On October 22, 2025, Microsoft published an FAQ on this topic—this is by design and for security reasons.
[German]The security updates for Windows released on October 14, 2025 cause the preview of files (e.g., PDF documents or Office documents) in Explorer to be blocked in some cases. I described the problem in Part 1. On October 22, 2025, Microsoft published an FAQ on this topic—this is by design and for security reasons.
What is the preview problem?
The security updates for Windows, which were released on October 14, 2025, tweak the security settings. Once the MotW flag has been set for a file, document previews can no longer be displayed.
A warning appears, stating that the preview may damage your computer. I covered the details in the article Windows: File preview in Explorer broken after October 2025 update – Part 1. This affects various versions of Windows that have installed the October 2025 updates.
The issue was documented in the changelogs for the updates—e.g., KB5066791 —on October 22, 2025. Here is the text: "File Explorer] After installing this update, File Explorer automatically disables the preview feature for files downloaded from the internet. This change is designed to enhance security by preventing a vulnerability when users preview potentially unsafe files. For details, including steps to unblock files, see File Explorer automatically disables the preview feature for files downloaded from the internet."
Microsoft explains the whole thing in an FAQ
On October 22, 2025, Microsoft published a support article entitled File Explorer automatically disables the preview feature for files downloaded from the internet on the above issue, which explains a lot (I missed this when I created the German edition of part 1 for the blog).
Behavior is by design
First of all, it should be noted that this behavior of refusing file previews was deliberately caused by Microsoft. Redmond writes:
- Starting with Windows security updates released on or after October 14, 2025, File Explorer will automatically disable the preview feature for files downloaded from the Internet.
- This change is intended to improve security by preventing a vulnerability that could expose NTLM hashes when previewing potentially unsafe files.
In other words, uninstalling the October 2025 update to fix the problem is not a solution. The feature will return with the preview updates and all subsequent cumulative security updates.
The background and implications
The reason for this change is that Microsoft wants to close a security gap that could lead to the disclosure of NTLM hashes. This is the case, for example, when users preview files that contain HTML tags (such as <link>, <src>, etc.) that refer to external paths. Attackers could exploit this preview function to capture sensitive login data.
Therefore, the preview function has been disabled by default for all files marked with "Mark of the Web" (MotW), which indicates that they originate from the 'Internet' security zone. The same applies to files with this flag that are located on network shares assigned to the "Internet" security zone.
At this point, a note to administrators: If possible, NTLM could be disabled in the environment and Kerberos could be used instead. This should mitigate the above attack vector.
Workarounds and solutions
In Part 1, I outlined the general context and also described some workarounds (apart from uninstalling the updates).
Resetting the MotW flag
If a user is certain that a download from the Internet poses no threat, they can reset the MotW (Mark-of-the-Web) attribute.
- To do this, right-click on the document file whose preview is being denied and select Properties from the context menu.
- In the Properties window, select the Allow check box in the Security group on the General tab.
If you close the Properties window by clicking the OK button, the MoW attribute should be deleted and previewing should be possible again.
Add network shares to the intranet or trusted zone
For document files located on network shares, you can select the Internet Options command in the Windows Control Panel to open the Internet Properties window.
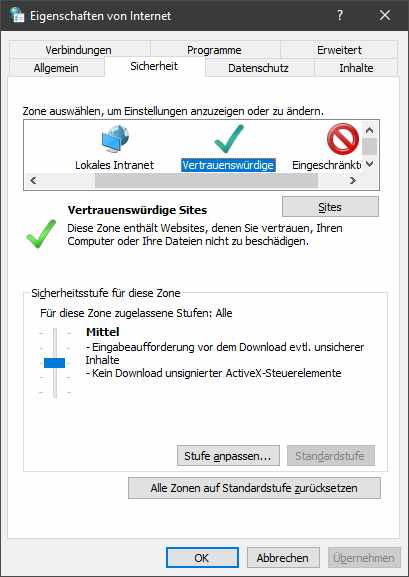
The security zones can be found in the Properties window on the Security tab. In most cases, it should be sufficient to add the network shares to the Local Intranet or to the Trusted Sites zone. The Sites button allows you to enter the path names for sharing. German blog reader Werner has confirmed that this works.
Workaround via GPO
In Part 1, two blog readers outlined how administrators can mitigate the problem with network shares for their users. German blog reader Werner provided the appropriate group policy here. Open the Group Policy Editor gpedit.msc and navigate to the following branch.
Computer Configuration\Policies\Administrative Templates\Windows Components\Internet Explorer\Internet Control Panel\Security Page\
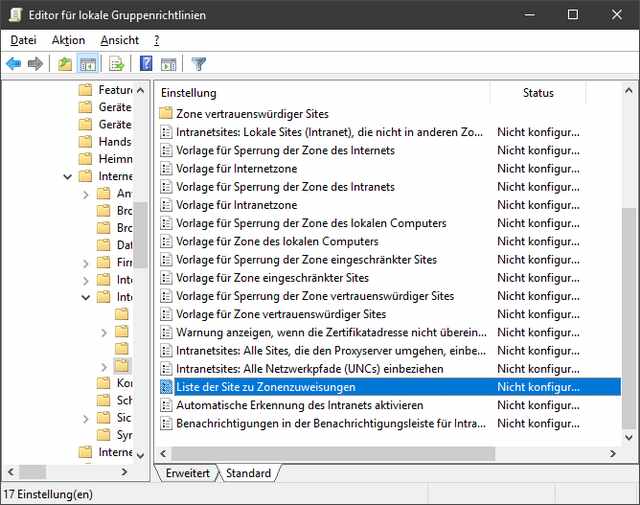
Open the "List of sites for zone assignments" policy there, and then enter the file servers to be released. Don't forget the DFS root for DFS, Werner notes. Then update the group policy.
Further comments
In this German comment Jan mentions, that the PDF preview also fails when PDF documents are received by email. The MotW attribute is also set there – which pleases invoice recipients in accounting. There is a crude workaround: The MotW attribute is only supported on NTFS data volumes. So he set up a FAT32 drive (USB stick) where users can move the files. The preview then works there.
Blog reader Michel Py writes in this German comment that the above GPO was unsuccessful. He provided a registry entry that solved the problem of assigning the correct Internet zone to the storage locations. A restart is required after this.
Andreas also mentioned a GPO in this German comment that allowed him to reactivate the preview via the Device Manager. Perhaps the approaches outlined above will help.
Article series:
Windows: File preview in Explorer broken after October 2025 update – Part 1
Windows file preview broken with Oct. 2025 update: Microsoft explains why it's by design – Part 2
Similar articles:
Microsoft Security Update Summary (October 14, 2025)
Patchday: Windows 10/11 Updates (October 14, 2025)
Patchday: Windows Server-Updates (October 14, 2025)
Patchday: Microsoft Office Updates (October 14, 2025)
Exchange Server Security Updates October 2025
Windows 10 22H2/Windows 11 23H2-25H2: Preview Updates (September 23/25/29, 2025)
September 2025 Update KB5065426 causes issues with large AD environments
Windows 11 24H2/25H2: Localhost issues after October 2025 update KB5066835
Windows 11 24H2-25H2/Server 2025: Microsoft confirms issue with IIS/localhost, offers KIR solution
Windows 10/11: USB keyboard/mouse doesn't work properly in WinRE
Windows 11 24H2-25H2: Out-of-band Recovery Update KB5070762
Windows 11 24H2-25H2: Out-of-Band-Update KB5070773 fixes USB keyboard and mouse issues in WinRE
Windows 10 22H2/Windows 11 23H2-25H2: Preview Updates (September 23/25/29, 2025)
Windows 11 24H2-25/H2, Server 2025: SID duplicates cause NTLM/Kerberos authentication errors



