 [German]A bug in Windows SMB (Server Message Block) protocol sets network systems at risk. A proof of concept code is publically available, but no patch is in sight. US-CERT warns.
[German]A bug in Windows SMB (Server Message Block) protocol sets network systems at risk. A proof of concept code is publically available, but no patch is in sight. US-CERT warns.
The SMB issue
The United States Computer Emergency Readiness Team (US-CERT) has releases an official Advisory yesterday.
Microsoft Windows contains a memory corruption bug in the handling of SMB traffic, which may allow a remote, unauthenticated attacker to cause a denial of service or potentially execute arbitrary code on a vulnerable system.
Microsoft Windows fails to properly handle traffic from a malicious server. In particular, Windows fails to properly handle a server response that contains too many bytes following the structure defined in the SMB2 TREE_CONNECT Response structure. By connecting to a malicious SMB server, a vulnerable Windows client system may crash (BSOD) in mrxsmb20.sys.
In short – some Windows versions (clients an servers) contains a memory corruption bug in the code to handle SMB data traffic. The bug is contained within the kernel file mrxsmb20.sys.
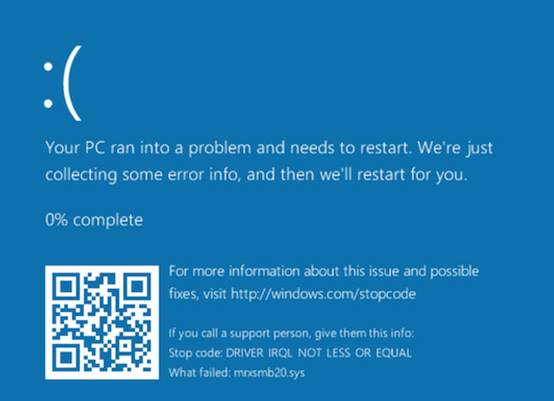
US-CERT writes, that the bug may be used by unauthenticated attacker to cause a denial of service (aka Blue Screen) – currently it isn't clear, whether this can be used to inject and execute malicious code (probably not). Exploit code to use this vulnerability has been released to the public (see this tweet and here).
SMBv3 0day, Windows 2012, 2016 affected, have fun :) Oh&if you understand this poc, bitching SDLC is appropriate :)https://t.co/xAsDOY54yl
— Responder (@PythonResponder) February 1, 2017
Which Windows systems are affected?
US-CERT writes, the bug has been found on fully patched systems with Windows 8.1 and Windows 10, but also affects Windows server versions. Bleeping Computer names Windows 10, Windows 8.1, Windows Server 2012 and Windows Server 2016 as affected.
The ancient SMB protocol is available as SMBv1, SMBv2 and SMBv3. Microsoft recommends, to deactivate SMBv1 due to security reasons. But the bug addresses SMBv3.
US-CERT qualifies this vulnerability as 10 of a scale of 10 (most critical). Till now, no patch from Microsoft is available. US-CERT proposes the following workaround:
Consider blocking outbound SMB connections (TCP ports 139 and 445 along with UDP ports 137 and 138) from the local network to the WAN.
For me, it seems that this is for companies with WANs. For small LANs I would classify the risk as low, because an attacker needs access to the network shares. Also in networks with WLAN access is WPA2 protected, so I can't see, how the exploit can bee uses (but maybe I overlooked something).




"or in worst case inject and execute malicious code" – advisory does not say that. BSOD by its nature will prevent that.