 [German]Security researcher has found a new security issue in Windows 10 that allows malware to bypass most common security solutions using Subsystem for Linux (WSL).
[German]Security researcher has found a new security issue in Windows 10 that allows malware to bypass most common security solutions using Subsystem for Linux (WSL).
Advertising
This vulnerability was recently discovered by the security company Check Point and documented in this blog post. Check Point wrote, that it's a new and alarming method that allows any known malware to bypass even the most common security solutions, such as next generation anti-viruses, inspection tools, and anti-ransomware.
The method to bypass security solutions was dubbed Bashware, because it uses the Bash shell in Subsystem for Linux (WSL). WSL is a now a full supported feature in Windows 10, that which recently exited Beta. It makes the popular bash terminal available for Windows OS users, and in so doing, enables users to natively run Linux operating system executables on the Windows operating system.
Existing security solutions fails to detect malware
Bashware is so alarming because it shows how easy it is to take advantage of the WSL mechanism to allow any malware to bypass security products. Check Point tested the Bashware technique on most of the leading anti-virus and security products on the market, successfully bypassing them all.
Their findings: Existing security solutions are still not adapted to monitor processes of Linux executables running on Windows OS, a hybrid concept which allows a combination of Linux and Windows systems to run at the same time. This may open a door for cyber criminals wishing to run their malicious code undetected, and allow them to use the features provided by WSL to hide from security products that have not yet integrated the proper detection mechanisms.
This means that Bashware may potentially affect any of the 400 million computers currently running Windows 10 PC globally, if Subsystem for Linux is activated as an additional feature.
Advertising
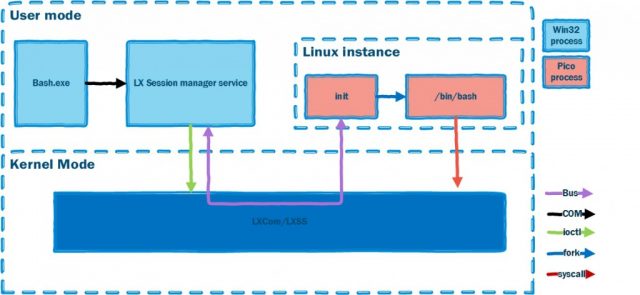
The Bashware technique leverages the underlying mechanism of the Windows Subsystem for Linux (WSL). This feature, introduced as part of Windows 10, allows native Linux ELF binaries to run on Windows.
The WSL feature goes far beyond having the familiar Linux "Bash" shell on Windows OS. It contains both user mode and kernel mode components, which together create a complete compatibility layer for running an environment that looks and behaves just like Linux, without having to fire up any virtual machine.
(Source: Check Point)
Microsoft aimed to run the target application and OS entirely within the user-mode address space of a single process, by implementing a way to run an application in an isolated environment, with reduced overhead. In order to allow this new concept, Pico processes were introduced. Pico processes are the containers that allow running ELF binaries on the Windows OS. These new types of processes are minimal and lack the structural blocks that are commonplace in regular Windows NT processes (PEB, TEB, NTDLL, etc.).
By placing unmodified Linux binaries in Pico processes, WSL enables Linux system calls to be directed into the Windows kernel. The lxss.sys and lxcore.sys drivers translate the Linux system calls into NT APIs and emulate the Linux kernel.
The key to the technique lies within the design of the Pico process structure. The Pico process has none of the common windows process characteristics, and in fact – nothing that would identify it as a regular NT process at all. Nevertheless, Pico processes have the same capabilities as normal NT process and do not pose any less threat.
This may open a door for cyber criminals wishing to run their malicious code undetected, and allow them to use the features provided by WSL to hide from security products that have not yet integrated the proper detection mechanisms.
(Source: YouTube
The above video demonstrates the attack. Check Point has updated their SandBlast Threat Prevention solutions, to protect customers from Bashware. Check Point call the security industry to take immediate action and to modify their security solutions to protect against this new method. The only fix today is to remove WSL from Windows, until the access vector has been closed and the used security solution is capable to detect such an attack. Further details may be found within Check Points blog post Beware of the Bashware: A New Method for Any Malware to Bypass Security Solutions
Advertising





