 [German]The 0Patch team has developed a micropatch to close a 0-Day Information Disclosure vulnerability in Internet Explorer 11 on Windows 10. This vulnerability allows Windows attackers to access files and upload them from the user's system to their own servers. It is caused by an undocumented Edge feature that breaks IE 11's security under Windows 10.
[German]The 0Patch team has developed a micropatch to close a 0-Day Information Disclosure vulnerability in Internet Explorer 11 on Windows 10. This vulnerability allows Windows attackers to access files and upload them from the user's system to their own servers. It is caused by an undocumented Edge feature that breaks IE 11's security under Windows 10.
Advertising
0-day vulnerability in Internet Explorer
There is a vulnerability in Microsoft Internet Explorer that allows attackers in all versions of Windows to access and steal files. However, Microsoft has no ambitions to patch the vulnerability. I had reported a few days ago about the problem discovered by security researcher John Page in the blog post 0-day vulnerability in IE 11 allows to steal files.
0Patch finds an undocumented Edge trick
When security researcher John Page reported the problem to Microsoft, Microsoft returned the answer that they would eventually fix it – was not considered important. The 0Patch team then tried to track this attack using .HMT files on Windows 7. The security researchers found interesting details and informed me by e-mail.
For files downloades from the Internet, the proof of concept code did not work for the 0patch team under Windows 7, while for locally created .HMT files, it was uploaded to a server. This is because the browser marks downloads from the Internet with an Internet zone bit (Zone.Identifier, referred by 0patch as mark-of-the-web) in the alternate data stream. Then strict security rules apply to the browser to prevent such attacks. The whole thing is described in this blog post.
Then the 0Patch team switched from Windows 7 to Windows 10 and suddenly MHT files downloaded from the Internet in the Edge browser could read local files and transfer them to a server (i.e. steal them) when they were opened via Internet Explorer. But why? Doesn't Edge set the Zone.Identifier on downloaded files, or does it do it differently and confuse Internet Explorer somehow? That would be a serious mistake.
Time for a differential analysis comparing two MHT files downloaded from the same location. One was downloaded from the Internet using Internet Explorer (msie-xss-0day-1.mht) and the other using Edge (msie-xss-0day-2.mht). The data from the Alternat Data Stream was opened with an editor. This showed that the files have slightly different Zone.Identifier data streams.
Advertising
msie-xss-0day-1.mht
[ZoneTransfer]
ZoneId=3
msie-xss-0day-2.mht
[ZoneTransfer]
ZoneId=3
ReferrerUrl=http://www.acrossecurity.com/test/
HostUrl=http://www.acrossecurity.com/test/msie-xxe-0day-2.mht
The Edge Browser inserts two URLs into the file. But when the team transferred the Zone.Identifier information from file 1 to file 2, nothing changed in the existing vulnerability. There were two identical files with identical data streams, and one of them executed the exploit while the other did not.
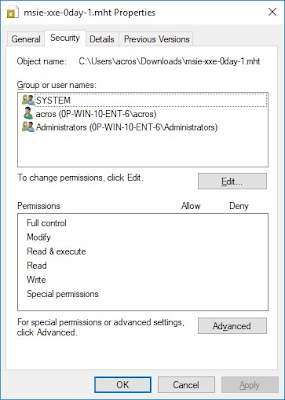
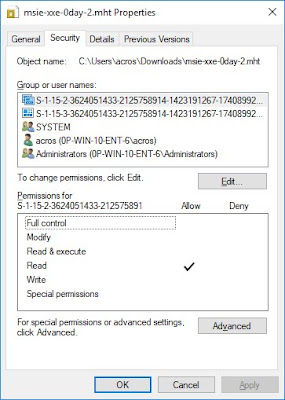
(Permissions: left with Internet Explorer, right with Edge downloaded)
After a little frustration, Twitter user Eric Lawrence suggested to check the permissions for these files. The picture above shows the permissions when downloading via IE and Edge. Edge seemed to have added two entries to the AC of the downloaded file, both for some SIDs that Windows cannot translate into a name.
After a lengthy analysis described in the blog post, it was clear that an undocumented security feature used by Edge neutralized an existing, undoubtedly much more important feature (mark-of-the-web) in Internet Explorer. It is clearly a significant security issue, especially as the attack can be further improved over the originally proven Proof of Concept (PoC). Because:
- The malicious MHT file does not need to be downloaded and manually opened by the user – opening it directly from Edge can also be successful;
- The exploit can be improved to work quieter and extract many local files with a single MHT file.
On the other hand, only Edge users are at risk. No other popular web browsers and email clients tested by 0patch people use the undocumented security flag in downloaded files, effectively blocking the abuse.
Micropatch available
Although the people of 0patch believe that Microsoft will update its original severity rating of this problem and provide a solution to it, action has been taken. People have developed a micropatch that they make available to 0patch users so that they can protect themselves. Details on this topic can be found in this blog post. Thanks also to the blog readers who pointed this out to me in parallel to the 0patch people's mail to me.







