[German]Windows offers the possibility to change the window title of windows of a terminal emulator via control characters (ANSI Escape Characters). Some blog readers still know this, was used to adjust colors of a DOS window for example. A security researcher has shown that something like DoS attacks are also possible with it, which allow a white window ("White Screen of Death") or even a crash of the system via vulnerabilities in the applications. This is especially a problem in environments (Kubernetes) where terminal emulators are used and the window or the whole Windows machine can be crashed.
[German]Windows offers the possibility to change the window title of windows of a terminal emulator via control characters (ANSI Escape Characters). Some blog readers still know this, was used to adjust colors of a DOS window for example. A security researcher has shown that something like DoS attacks are also possible with it, which allow a white window ("White Screen of Death") or even a crash of the system via vulnerabilities in the applications. This is especially a problem in environments (Kubernetes) where terminal emulators are used and the window or the whole Windows machine can be crashed.
I came across the issue via the following tweet from colleagues at Bleeping Computer, which is described by Eviatar Gerz (CyberArk) in the article Don't Trust This Title: Abusing Terminal Emulators with ANSI Escape Characters.
Working with OpenShift (RedHat's Kubernetes distribution), Eviatar Gerz found that he could inject ANSI escape characters (see the following image) into web application components.

ANSI Escape Characters, Source: CyberArc
The ANSI escape characters are then executed by the components – in the current case, the security researcher used this to change the color of the terminal window used. The question arose as to whether this could be abused for security purposes. Because there is an interesting Advisory von Digital Defense Incorporated from 2003 about security issues with terminal emulators.
Terminal emulators vulnerable
After investigating the issue, Eviatar Gerz found that many terminal emulators under Windows could be attacked and crashed via ANSI escape characters. At the end of the day, the following findings were available:
- Five serious vulnerabilities: CVE-2021-28847, CVE-2021-28848, CVE-2021-32198, CVE-2021-33500 and CVE-2021-42095 were discovered. Security researchers have found a way to remotely cause a DoS (Denial of Service) on the terminal client host.
- An ANSI escape character injection vulnerability in OpenShift and Kubernetes (CVE-2021-25743).
- Three additional vulnerabilities: CVE-2021-31701, CVE-2021-37326 And CVE-2021-40147. A way to bypass the bracket insertion mode mechanism within Terminals was found.
The details of the investigation into customizing the title of Teminal emulator windows via ANSI escape control characters were downright shocking. With minor modifications, the remote DoS attacks could be driven. Here is the list of CVEs of the discovered vulnerabilities
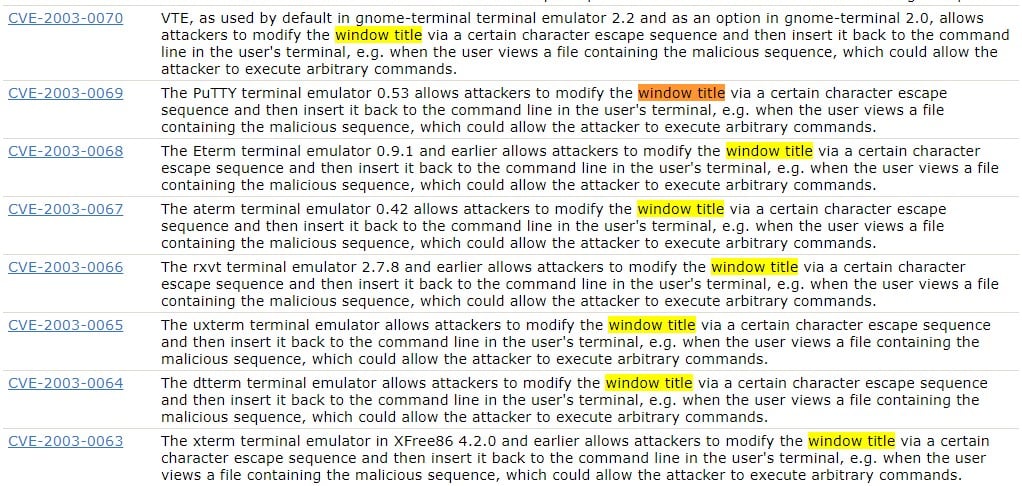
Vulnerabilities in terminal emulators, source: CyberArc
At the end of the day, the following terminal emulators (and some browsers) could be attacked:
- PuTTY: Vulnerability CVE-2021-33500 can cause the entire machine to freeze, fixed in version 0.75
- MobaXterm: Vulnerability CVE-2021-28847 lässt sich die App einfrieren, korrigiert in Version 21.0 Preview 3
- MinTTY (and Cygwin): Vulnerability CVE-2021-28848 can cause the entire machine to freeze, fixed in version 3.4.6
- Git: Uses MinTTY, fixed in version 2.30.1
- ZOC: Vulnerability CVE-2021-32198 the app can be frozen, no fix
- XSHELL: Vulnerability CVE-2021-42095 can freeze the entire machine, fixed in version 7.0.0.76
The extensive details of the exploitation of these attack paths can be read in the article Don't Trust This Title: Abusing Terminal Emulators with ANSI Escape Characters.