 [German]Problem for users of an AVM FRITZ!Box family broadband routers who try to access the router's administration interface from the home network. However, when entering the URL fritz.box, users do not end up on the routers firmware FRITZ!Box login page, but are redirected to an external website. Two users have pointed out the problem to me, with one user suspecting a hack. The cause is a combination of two circumstances that provoke this behavior. Someone has registered a domain fritz.box and DNS servers from Google then resolve to this page. The remedy is to enter the IP address of the FRITZ!Box or to use a different DNS server.
[German]Problem for users of an AVM FRITZ!Box family broadband routers who try to access the router's administration interface from the home network. However, when entering the URL fritz.box, users do not end up on the routers firmware FRITZ!Box login page, but are redirected to an external website. Two users have pointed out the problem to me, with one user suspecting a hack. The cause is a combination of two circumstances that provoke this behavior. Someone has registered a domain fritz.box and DNS servers from Google then resolve to this page. The remedy is to enter the IP address of the FRITZ!Box or to use a different DNS server.
Advertising
An e-mail from a blog reader
Blog reader Bernd D. contacted me by e-mail this afternoon. The subject of the e-mail was "Fritz.box hijacked?". I immediately thought of the German blog post Neues zur Authentication Bypass-Schwachstelle in FRITZ!OS (Sept. 2023) about a bypass vulnerability. Bernd wrote in his email:
Hello Günter,
as a regular and convinced reader of your feed from the Borncity blog, I wanted to tell you about a current phenomenon with fritz.box.
Basically, it was foreseeable that this would happen.
Anyone who currently wants to look at their local fritz!box and enters fritz.box in Firefox ends up on a dubious page, see 2 screenshots.
I'm sure it's not just me, is it?
192.168.178.1 works of course
Bernd then sent me a screenshot of the landing page, which I have included below.
Quick cross-check: Don't work for me
At this point, of course, I immediately did a cross-check and typed the URL fritz.box into Ungoogled browser. As expected, I ended up on my login page for the FRITZ!box broadband router. In the next step, I tested the Firefox browser with this URL. First a warning appears that the URL fritz.box is insecure and can only be accessed via http. However, this is known and you can display this "insecure" page (in a local network this isn't a security problem). However, the expected FRITZ!Box login page appeared there.
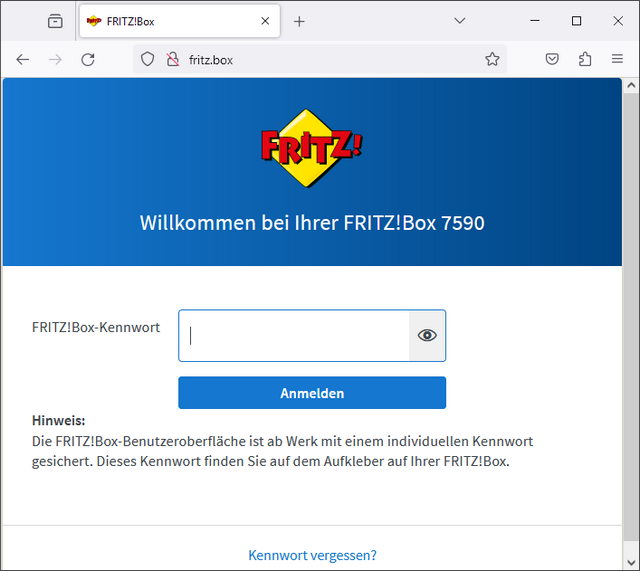
So I put the issue aside for the time being and informed the user by email that there was no redirection for me. I then phoned AVM briefly, but received confirmation that nothing was known about an attack – but they were looking into it.
Advertising
A second reader report
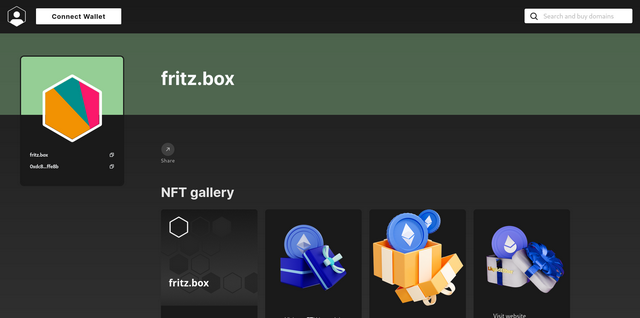
A short time later, Ralf M. contacted me with an e-mail "fritz.box registered, chaos at the end customer" and also wrote to me that the URL fritz.box would not take him to the login page, but would redirect him to the above external page. Ralf also posted the above screenshot and wrote "Fortunately only an NFT page and not a replicated login mask.". That was the point where I called AVM (see comment above), but got no immediate answer.
Bernd got in touch with me a couple of minutes later and wrote that the Chrome browser was suddenly redirecting him to the local router (as was with the mullvad browser). He use Deutsche Telekom, he wrote, adding "Oh, my Firefox is now back to normal, that's strange. The last screenshots are from 13:42, when the redirection was still active."
The explanation
When I replied to Ralf that he was the second one, he took care of the issue. In the first email he had already sent me a link to Whois for fritz.box. There you can see that four days ago someone registered a fritz.box domain in the USA, which is held by namesilo.
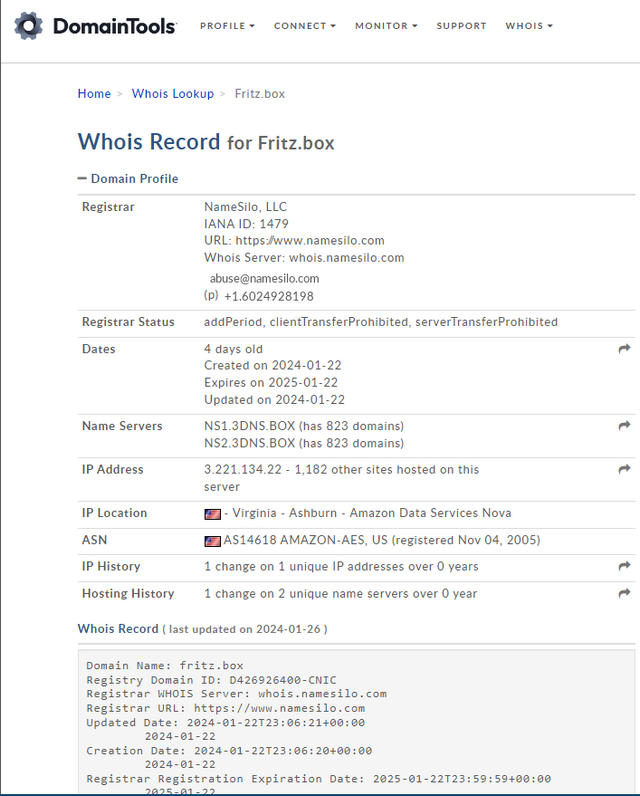
I then did a little Google search, but got nowhere. Then Ralf M. got in touch again and wrote to me: "As soon as a different DNS server is specified in the FRITZ!Box, e.g. 8.8.8.8 or 8.8.4.4 for Google, the Fritz.box goes to the NFT page." This at least explains the problem.
With Google's DNS server, the URL to be resolved internally is resolved externally to the above page and redirected. Shows how shaky this Internet has become – no hijacked FRITZ!Boxes, but a tricky "hijacking" of the Google DNS server. So pay attention to which DNS servers you use and, if necessary, work with the IP of the FRITZ! Thanks in any case to the two blog readers for the tips.
Answer from vendor AVM
AVM's press department contacted me by e-mail with additional information after my first telephone message. Of course, there is this AVM FRITZ!Box support page that addresses the problem of the FRITZ!Box interface not being accessible. But that does not apply here.
In the reply e-mail, the AVM press spokeswoman, Doris Haar, gave me an explanation of what happened. According to this, the fritz.box domain is currently in a sales process in which AVM is also involved. As a result, users may occasionally be taken to another inappropriate, harmless page when the URL fritz.box is entered in the browser.
Calling fritz.box in the home network is possible as usual and is the responsibility of the home FRITZ! box. Until now, users who accidentally entered fritz.box outside their home network received a browser error message or were redirected to a search engine. At the moment, users who accidentally call up fritz.box outside their home network are shown an obviously inappropriate and harmless page.
The spokeswoman told me that AVM is now monitoring all activities relating to the domain allocation and is keeping an eye on security-related requirements.








I've just encountered a problem where trying to connect to another PC or NAS drive by name is resolving externally.
So, for example, \\nas is resolving to nas.fritz.box on IP 45.76.93.104 instead of the internal IP address of the NAS drive.
Make sure your DNS server is set as your routers local IP address. Upstream DNS can still be used for name resolution of external domains but will check local DNS first, where it will find your local DNS entries rather than doing a lookup online.
just add 169.254.1.1 fritz.box to the host file and it is working again
WTH
ping google
PING google.fritz.box (45.76.93.104) 56(84) bytes of data.
64 bytes from 45.76.93.104.vultrusercontent.com (45.76.93.104): icmp_seq=1 ttl=245 time=275 ms
64 bytes from 45.76.93.104.vultrusercontent.com (45.76.93.104): icmp_seq=2 ttl=245 time=295 ms
64 bytes from 45.76.93.104.vultrusercontent.com (45.76.93.104): icmp_seq=3 ttl=245 time=277 ms
64 bytes from 45.76.93.104.vultrusercontent.com (45.76.93.104): icmp_seq=4 ttl=245 time=280 ms
^C
— google.fritz.box ping statistics —
5 packets transmitted, 4 received, 20% packet loss, time 4009ms
rtt min/avg/max/mdev = 274.867/281.489/294.599/7.774 ms
Must be some angry comms going on at the moment with Fritz, ICANN domain reg and vultr. Interestingly going to any of these hijacked sites gets:
"This Site is Suspended
The Domain Name you have entered is not available. It has been taken down as a result of dispute resolution proceedings pursuant to the Uniform Rapid Suspension System (URS). "
Ping to any network name seems to automatically get resolved to this ip above which belongs to the "vultr" group.
These guys "vultr" aren't exactly getting good press at them moment. Some global cloud provider. I wouldn't trust them as far as I can throw them.
https://arstechnica.com/tech-policy/2024/03/after-overreaching-tos-angers-users-cloud-provider-vultr-backs-off/
Blocking off fritz.com domain locally on hosts file in the interrim as recommended above until issue gets resolved.