[German]A quick note for administrators in corporate environments. Microsoft carries out so-called hardening measures for Windows (clients and servers) over longer periods of time. This involves hardening (securing) functions via Windows Update on certain key dates. Some of these hardening measures are also scheduled for 2024 and 2025. Microsoft has recently updated its corresponding schedule.
[German]A quick note for administrators in corporate environments. Microsoft carries out so-called hardening measures for Windows (clients and servers) over longer periods of time. This involves hardening (securing) functions via Windows Update on certain key dates. Some of these hardening measures are also scheduled for 2024 and 2025. Microsoft has recently updated its corresponding schedule.
Hardening Windows against security threats is a key element of Microsoft's ongoing security strategy to protect installations. Microsoft has published a support article KB5036534: Latest Windows hardening guidance and key dates which was updated on March 10, 2024 (our colleagues noticed it).
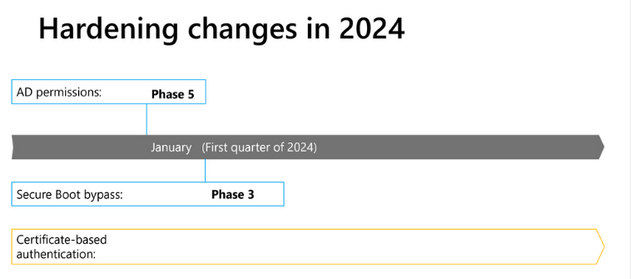
I'll skip the hardening measures that have already been implemented (you can read about them in the article above or in the blog post Important dates for Windows hardening in 2024 from January 2024). However, Microsoft is planning the following dates for the coming months
- April 2024: Secure Boot bypass protections KB5025885 (Phase 3). This is about managing Windows Start Manager lockouts for Secure Boot changes related to CVE-2023-24932. This phase will add additional protections for the Boot Manager. This phase will begin on April 9, 2024 at the earliest.
- Oktober 2024 (or later): Secure Boot bypass protections KB5025885 (Phase 3). Mandatory Enforcement-Mode. The overrides (Code Integrity Boot policy and Secure Boot disallow list) are enforced programmatically after the installation of Windows updates on all affected systems without being able to be deactivated.
- February 2025 (or later): Certificate-based authentication KB5014754 (Phase 3). Full Enforcement-Mode. This involves changes to certificate-based authentication on Windows domain controllers. The vulnerabilities CVE-2022-34691, CVE-2022-26931 and CVE-2022-26923, allow privilege escalation. This can occur when the Kerberos Key Distribution Center (KDC) processes a certificate-based authentication request. If a certificate cannot be uniquely assigned, authentication is denied.
This means that administrators may have some work to do on the next patchday.