 [German]A short addendum from the December 2024 patchday. On December 10, 2024, Microsoft published a critical vulnerability (CVE-2024-49112) in the Lightweight Directory Access Protocol (LDAP). This enables remote attacks on Windows clients and servers, but has been patched. However, there are a number of systems accessible on the Internet via LDAP, which should be avoided or the systems should be specially secured. Here is a brief overview.
[German]A short addendum from the December 2024 patchday. On December 10, 2024, Microsoft published a critical vulnerability (CVE-2024-49112) in the Lightweight Directory Access Protocol (LDAP). This enables remote attacks on Windows clients and servers, but has been patched. However, there are a number of systems accessible on the Internet via LDAP, which should be avoided or the systems should be specially secured. Here is a brief overview.
Windows LDAP vulnerability (CVE-2024-49112)
I have added it to the blog post Microsoft Security Update Summary (December 10, 2024). Microsoft disclosed the vulnerability CVE-2024-49112 in the Windows Lightweight Directory Access Protocol (LDAP) on December 10, 2024. This is a remote code execution vulnerability caused by an integer overflow that has been rated as critical with a CVEv3 score of 9.8.
An unauthenticated attacker can successfully exploit this vulnerability remotely. He then has the possibility to execute arbitrary code in the context of the LDAP service. However, successful exploitation depends on which component is attacked.
- In the context of exploiting a domain controller for an LDAP server, an attacker must send specially crafted RPC calls to the target to trigger a query of the attacker's domain in order to be successful.
- In the context of exploiting an LDAP client application, an attacker must convince or trick the victim into performing a domain controller query for the attacker's domain or connecting to a malicious LDAP server. However, unauthenticated RPC calls would not be successful.
The vulnerability was closed as part of the security updates for Windows rolled out on December 10, 2024 (see links at the end of the article). Microsoft states that this vulnerability is not being exploited so far and exploitability is considered less likely.
Customers should also ensure that domain controllers are either configured not to access the Internet or not to allow incoming RPCs from untrusted networks. Both measures will protect a system from this vulnerability.
The background is that RPC and LDAP are published externally via SSL. Applying the above mitigations reduces the risk that an attacker can successfully convince or trick a victim into connecting to a malicious server. If a connection is established, the attacker could send malicious requests to the target over SSL.
Numerous systems reachable on the Internet
The topic came to my attention recently via security service provider Hunter. In the following tweet, they point out the facts.
Hunter writes that Microsoft has disclosed details of the critical vulnerability CVE-2024-49112, which allows remote code execution (RCE) in Windows Lightweight Directory Access Protocol (LDAP).
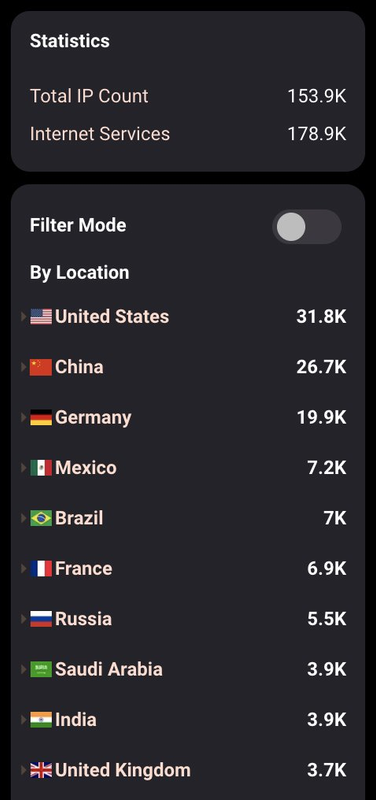
According to Hunter 178,900 LDAP and LDAPS services are found annually during scans via hunter.how. The image above shows the hits for different countries.
Similar articles:
Microsoft Security Update Summary (December 10, 2024)
Patchday: Windows 10/Server Updates (December 10, 2024)
Patchday: Windows 11/Server 2022/2025-Updates (December 10, 2024)
Patchday: Windows Server 2012 / R2 (December 10, 2024)
Patchday: Microsoft Office Updates (December 10, 2024)




Hello Günter Born, I hope you are doing well. I am a regular reader of your blog. I even sometimes use your blog to write articles and fix Windows issues. But for some days, I have noticed that some links in the post content don't open the pages correctly. For example, the following links on this post don't open the pages correctly:
Similar articles:
Microsoft Security Update Summary (December 10, 2024)
Patchday: Windows 10/Server Updates (December 10, 2024)
Patchday: Windows 11/Server 2022/2025-Updates (December 10, 2024)
Patchday: Windows Server 2012 / R2 (December 10, 2024)
Patchday: Microsoft Office Updates (December 10, 2024)
The pages opened by these links are empty and have no content. There are several other instances too. I am trying to provide a screenshot of your page (which are not opening correctly) – https://imgur.com/TvSMwQB
Hope this will help you to correct the issue. Thanks and happy new year.
If you mean the "yellow area" in the header, which is "empty" in your screenshot, this can be explained. The yellow box is for ads, and if Google don't server ads, it stay empty with a yellow background. I won't fix that and hide the empty ad box due to unwelcome page shift.
Content is missing. I know the yellow area is a sandbox that appears because of missing AdSense ads. Please watch this: https://imgur.com/DbTSseU
Firefox is serving the pages properly. But Google Chrome and Microsoft Edge are creating the glitch.