[German]Blog reader Fabian D. accidentally discovered a Privilege Escalation vulnerability in the G Data Security Client at the beginning of April 2024 and was then able to prove a Privilege Escalation vulnerability in the G Data Management Server during targeted research. Both vulnerabilities were reported to G DATA and have been fixed with version 15.8.333 in December 2024.
[German]Blog reader Fabian D. accidentally discovered a Privilege Escalation vulnerability in the G Data Security Client at the beginning of April 2024 and was then able to prove a Privilege Escalation vulnerability in the G Data Management Server during targeted research. Both vulnerabilities were reported to G DATA and have been fixed with version 15.8.333 in December 2024.
Fabian has just contacted me by email and informed me about recently fixed vulnerabilities in G DATA business software. I assume that other blog readers are affected and may not have noticed that there is a security update to fix the vulnerabilities.
Discovery of vulnerabilities by chance
Blog reader Fabian wrote to me that in April 2024 he accidentally discovered a trivial Privilege Escalation Vulnerability (EoP) in the endpoint solution "G Data Security Client". The security solution is used on the servers of a service provider that provides parts of the data center where the reader works.
The discovery of the vulnerability aroused the reader's curiosity, and he then also took a look at the associated management software "G Data Management Server". There, too, the reader found a Privilege Escalation Vulnerability (EoP), which allows an ordinary user to (over)write arbitrary files as NT-Authority\SYSTEM via archives with relative path specifications (Zip Slip).
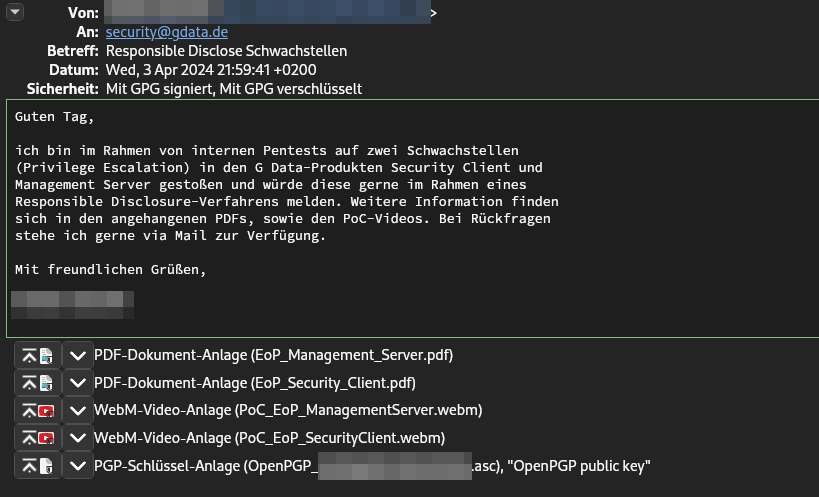
The blog reader then documented both vulnerabilities and reported them to G DATA (see screenshot of the report above). It is positively mentioned that G DATA provides a dedicated contact address with a public key for this purpose.
G DATA closes the vulnerabilities
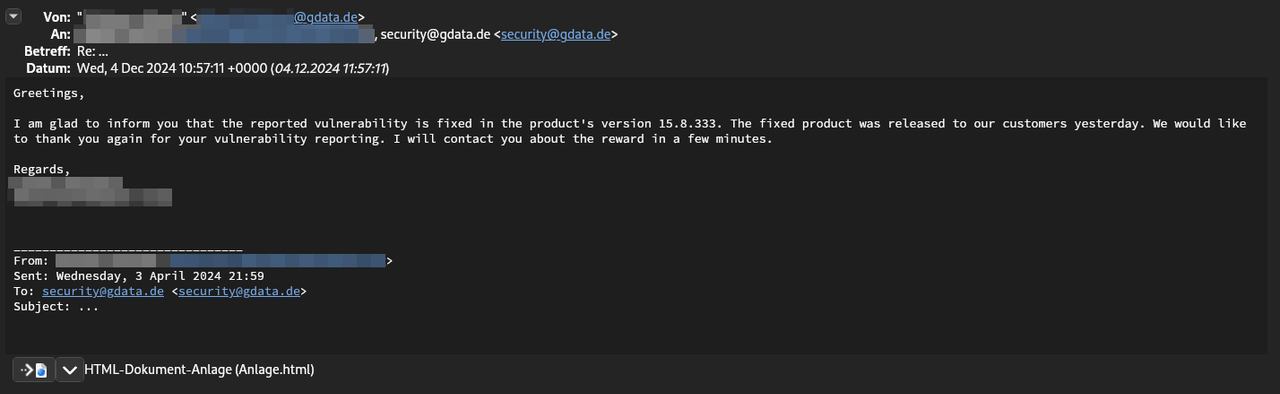
The reader wrote to me that after a long wait and several queries, both vulnerabilities were fixed by G DATA in early December 2024 with version 15.8.333. The provider has made a corresponding update available (see following image).
At a first glance everything actually went well. The problem, however, is that G DATA does not provide a change log for version 15.8.333 and therefore the fixes are not mentioned.
Fabian notes that unfortunately G DATA does not mention the fixes in the change logs or otherwise provide public information (blog post or similar) for customers. Unfortunately, this is currently of little help to customers and they have to trust that all those affected will release patches promptly via the management server, even if these do not appear to involve any security-relevant changes.
Perhaps one or two blog readers are affected by this issue and have not yet heard about this security update. Fabian asked G DATA about it. All he was told was that they were planning their own security bulletins and registration as a CVE Numbering Authority in the future. He himself has submitted a report on the vulnerabilities to MITRE, but has been waiting two months for a reply regarding the requested CVEs. I would like to take this opportunity to thank the reader for pointing this out.