 [German]I'm revisiting a topic here on the blog that still has a year to go, but could have very unpleasant consequences. UEFI Secure Boot certificates expire in June 2026. In October 2026, the next expiring UEFI certificate for Secure Boot will be affected. Microsoft pointed this out last week and asked administrators to react.
[German]I'm revisiting a topic here on the blog that still has a year to go, but could have very unpleasant consequences. UEFI Secure Boot certificates expire in June 2026. In October 2026, the next expiring UEFI certificate for Secure Boot will be affected. Microsoft pointed this out last week and asked administrators to react.
I have published several articles on the subject of expiring UEFI certificates, which are required for Windows Secure Boot, here on the blog (see end of article). However, it was about a certificate expiry in October 2026. But the topic will become explosive as early as June 2026. Last week, Microsoft published the tech community article Act now: Secure Boot certificates expire in June 2026, which refers to another certificate expiration problem. Various readers had emailed me about this topic (thank you).
UEFI Secure Boot certificate expires in June 2026
In the article, Microsoft points out that the Microsoft certificates used in Secure Boot will all expire in June 2026. The background to this is that these UEFI certificates were first issued 15 years ago (for Windows 8 machines).
Understanding the structure of the Secure Boot certificate chain
The Secure Boot introduced in Windows 8 uses a trust hierarchy based on certificates in the UEFI to ensure that only authorized software is executed at system startup. The platform key (PK), which is usually managed by the OEM or an authorized representative and serves as a basis of trust, is at the top of this chain.
The platform key (PK) authorizes updates to the Key Enrollment Key (KEK) database, which in turn authorizes updates to two critical signature databases: the Allowed Signature Database (DB) and the Forbidden Signature Database (DBX).
This multi-layered structure ensures that only validated updates can change the system's boot policy to ensure a secure boot environment (see Updating Microsoft Secure Boot keys).
Expiring certificates for Windows
Microsoft has published the following table with the list of expiring certificates in the Technet article. This article is about the two certificates Microsoft Corporation KEK CA 2011 and Microsoft Corporation UEFI CA 2011 (or UEFI certificates from third-party providers, e.g. for Linux systems), both of which expire in June 2026.fen.
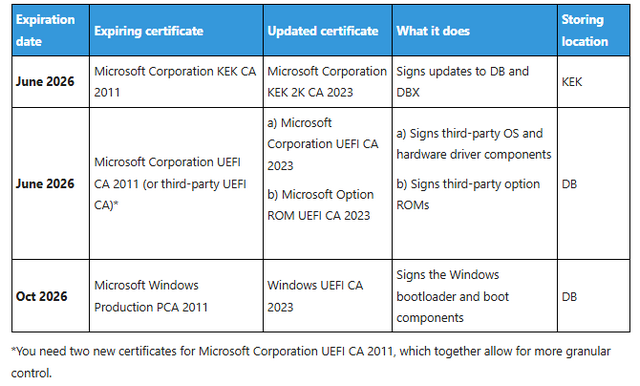
These expiring certificates will be replaced by the new Microsoft Corporation KEK 2K CA 2023 and Microsoft Corporation UEFI CA 2023 or Microsoft Option ROM UEFI CA 2023 certificates.
I referred to the expiring Microsoft Windows Production PCA 2011 certificate in October 2026 in the articles at the end of this article.
Which systems are affected?
Both physical and virtual machines (VMs) running a supported version of Windows 10, Windows 11, Windows Server 2025, Windows Server 2022, Windows Server 2019, Windows Server 2016, Windows Server 2012, Windows Server 2012 R2 are affected by the UEFI certificate expiry. These are all systems that have been released since 2012. This also includes systems from the Long-Term Servicing Channel (LTSC).
Not affected are systems that a) do not use Secure Boot to secure Windows startup and b) new systems with Copilot+PC from 2025 – the latter already have the new UEFI certificate from 2023.
Reminder: Apple Macs may also be affected if Windows is installed on this hardware via Bootcamp or virtualized via Parallels. However, Microsoft does not support updating these certificates. Those who do without Bootcamp and Windows or use one of the Apple Macs with a silicon chip (M1-M3) are also not affected.
What does the certificate expiring mean?
My first thought was that the systems no longer boot Windows when the certificate expires (see also my German blog post Frage: BlackLotus-Schwachstelle und ablaufendes UEFI-Zertifikat – was droht uns?). However, this scenario does not occur; the systems continue to boot Windows if Secure Boot is activated. If Secure Boot is deactivated and everything is
However, there is a bigger problem: Once these CAs expire, the systems will no longer receive security updates for the Windows Boot Manager and the Secure Boot components. Systems (whether physical devices or virtual machines) that rely on Secure Boot:
- Lose the ability to install Secure Boot security updates after June 2026 (relevant if root kits exploiting new vulnerabilities become known).
- Can no longer trust third-party software signed with new certificates after June 2026.
- Will no longer receive security updates for the Windows Boot Manager until October 2026 (and beyond).
The only remedy is to update the affected systems with the above-mentioned 2023 Secure Boot certificates.
In this context, Microsoft then brings out the cudgel "Compromised boot security threatens the overall security of affected Windows devices, particularly due to bootkit malware." out. It is mentioned that such an "unsecured" boot process can still be used today by the BlackLotus UEFI bootkit (CVE-2023-24932) as a cyberattack vector.
What do I have to do?
Anyone who wants or needs to ensure that the UEFI Secure Boot certificate chain is aligned with the 2023 certificates must ensure that the certificates are updated on the systems. Microsoft will (probably) roll out the updated Secure Boot certificates in the coming months as part of the monthly patchdays via Windows Update.
In this context, Microsoft advises administrators to check with the OEM providers whether new BIOS/UEFI firmware updates are available and to install them before updating the certificates via Windows Update. May be due to the latest "update problems", see the blog posts Windows 10: June 2025 update KB5060533 causes Surface Hub v1 boot error and Caution: Windows June 2025 updates bricks Fujitsu computers.
However, Microsoft's attempt to update the certificate that expires in October 2026 via Windows Update also went badly wrong (see my German blog post Frage: BlackLotus-Schwachstelle und ablaufendes UEFI-Zertifikat – was droht uns?). From this perspective, the coming months should "be exciting" in terms of the respective patch days.
As a precautionary measure, Redmond points out that Microsoft support is only available for supported client versions of Windows 11 and Windows 10. Once Windows 10 reaches the end of support in October 2025, administrators should consider obtaining Extended Security Updates (ESU) for Windows 10, version 22H2, to obtain further UEFI certificate updates if necessary.
Similar articles:
BlackLotus UEFI bootkit bypasses Secure Boot in Windows 11
KB5025885: Secure boot hardening against vulnerability CVE-2023-24932 (Black Lotus)
Update on Windows hardening in 2024/2025 – March 2024
Attention: Microsoft's UEFI certificate expires on Oct. 19, 2026 – Secure Boot affected
Windows 10: June 2025 update KB5060533 causes Surface Hub v1 boot error
Caution: Windows June 2025 updates bricks Fujitsu computers
FAQ and script for secure boot protection against CVE-2023-24932 (Black Lotus)




How does this work if it's Windows 10 on Boot Camp. We have iMacs and AFIK UEFI updates happen on the MacOS side. And also UEFI updates to Macs have broken Boot Camp once before – making the partition inaccessible, in fact invisible.