![]() [German]Microsoft has released a new Security Advisory on November 6, 2018 with hints for hardware and software encryption on Bitlocker SSD drives. Fits to a topic that I mentioned a few hours ago in a separate blog post.
[German]Microsoft has released a new Security Advisory on November 6, 2018 with hints for hardware and software encryption on Bitlocker SSD drives. Fits to a topic that I mentioned a few hours ago in a separate blog post.
Advertising
Background information
Microsoft Security Advisory Notification is about Bitlocker and software-based encryption on SSDs. A few hours ago I published the blog post SSD vulnerability breaks (Bitlocker) encryption on this topic. Here is the text of the Security Advisory:
* Microsoft Security Advisory ADV180028
– Title: Guidance for configuring BitLocker to enforce software
encryption
– https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/ADV180028
– Reason for Revision: Information published.
– Originally posted: November 6, 2018
– Updated: November 6, 2018
– Version: 1.0
Within the Security Advisory Microsoft reacts to exactly the fact that I mentioned within the above article that Bitlocker encryption of SSD drives is vulnerable if the hardware-supported variant is used.
What says Security Advisory ADV180028?
In the ADV180028 Microsoft confirms that there have been reports of a vulnerability in the bitlocker encryption of SSD drives and provides specific advices.
Advertising
Microsoft is aware of reports of vulnerabilities in the hardware encryption of certain self-encrypting drives (SEDs). Customers concerned about this issue should consider using the software only encryption provided by BitLocker Drive Encryption™. On Windows computers with self-encrypting drives, BitLocker Drive Encryption™ manages encryption and will use hardware encryption by default. Administrators who want to force software encryption on computers with self-encrypting drives can accomplish this by deploying a Group Policy to override the default behavior. Windows will consult Group Policy to enforce software encryption only at the time of enabling BitLocker.
How to check the used Bitlocker encryption method?
If an SSD is built into the system, Microsoft suggests using the command manage-bde.exe -status in an administrative command prompt (The abbreviation bde presumably stands for Bitlocker Device Encryption).
1. Open an administrative command prompt (e.g. enter cmd in the search box and use the context menu command Run as administrator).
2. Execute the command manage-bde.exe -status within the command prompt window and inspect the status messages.
I tried that command under Windows 7 SP1 and Windows 10 V1809, knowing that there is no Bitlocker encryption in use. Here is the status output of the command:

If none of the listed drives reports "Hardware Encryption" in the Encryption Method field, then this device uses software encryption or there is no Bitlocker encryption. Then the machine with its drives is not affected by (newly disclosed) vulnerabilities .
I am affected, what should I do?
If drives encrypted with Bitlocker using hardware encryption, administrators can fix the vulnerability by switching in Bitlocker to software encryption using Group Policy (GPO). Microsoft writes:
After a drive has been encrypted using hardware encryption, switching to software encryption on that drive will require that the drive be unencrypted first and then re-encrypted using software encryption.
If you are using BitLocker Drive Encryption, changing the Group Policy value to enforce software encryption alone is not sufficient to re-encrypt existing data.
To resolve the vulnerability caused by hardware-based encryption, follow these steps:
- Configure a Group Policy to enable forced software encryption and deploy it to the affected drives.
- Turn off Bitlocker completely to force decryption of the drive.
- After decryption, re-encrypt the drive by enabling Bitlocker.
At this point, Microsoft also clears up a misunderstanding, which I have torn out in the blog post SSD vulnerability breaks (Bitlocker) encryption. Microsoft writes:
IMPORTANT: You do NOT need to reformat the drive or reinstall any applications after changing BitLocker settings.
The Group Policy settings for Bitlockers can be found in this Microsoft document. For additional questions or ambiguities, Microsoft ADV180028 should be consulted. All in all, it must be said that Microsoft has reacted.
Addendum: Some more thoughts
It might be the GPO described here, that changes the encryption method. Martin Brinkmann has a more detailled description about that GPO at ghacks. But that thing is getting even stranger. Microsoft writes, that hardware based encryption support is beeing used by default, if supported (the settings within the GPO properties are indicating the same).
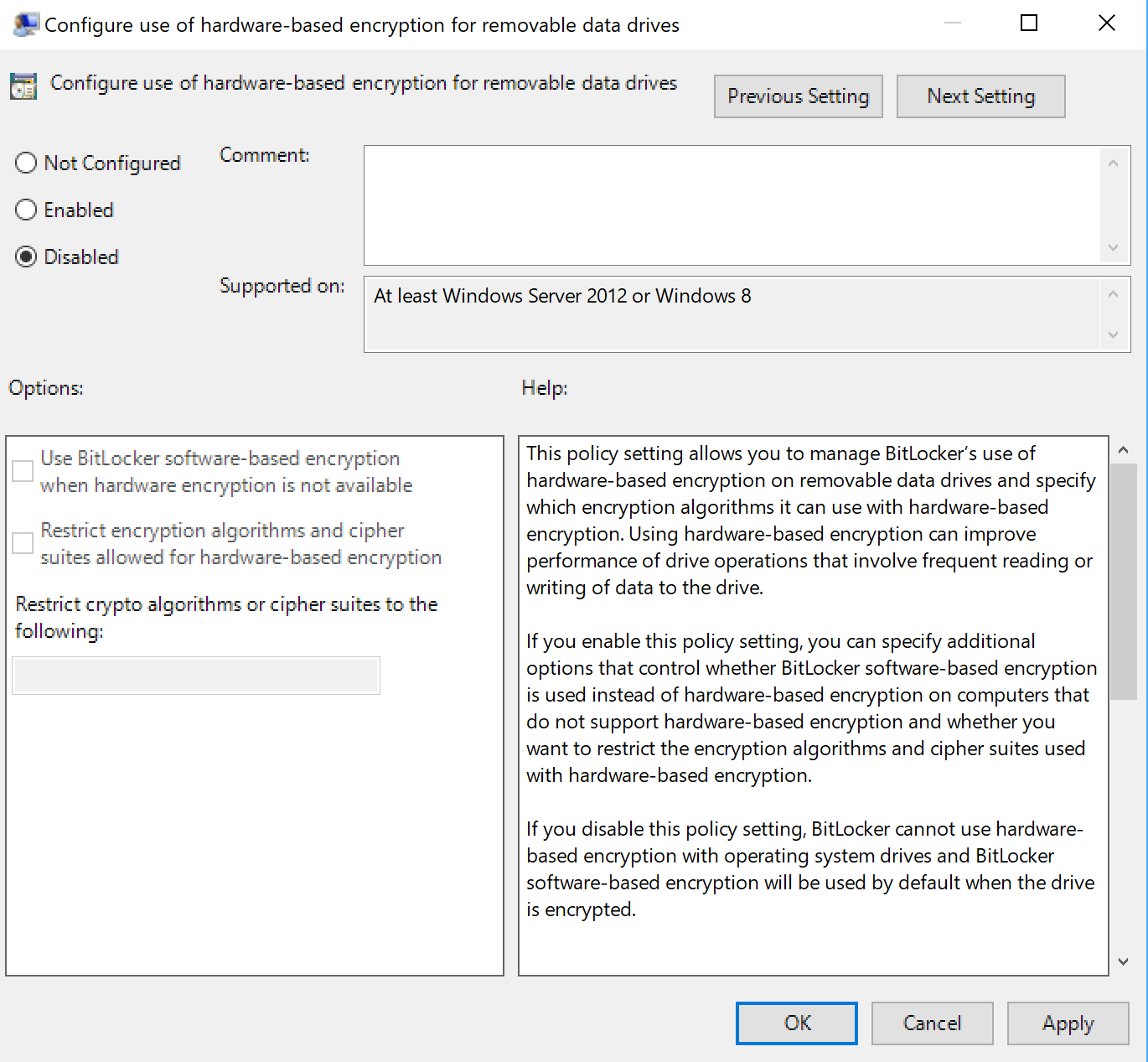 (Source: ghacks.net)
(Source: ghacks.net)
I received feedback from 2 German admins/consultants, administering large Windows install bases. They tolde me, the didn't found a machines using hardware based encryption. Maybe something is still missing, so no Windows machine is able to use haredware based encryption?
Similar articles:
SSD vulnerability breaks (Bitlocker) encryption
Windows 10 V1803: Fix for Bitlocker bug in Nov. 2018?
New Surface Book 2 Firmware Update with Bitlocker issue
Windows 10 V1803: No BitLocker recovery backup in AD
Windows 10 V1607: Hyper-V/Bitlocker/DeviceGuard as upgrade stopper
Security: TPM vulnerable; and dump mode for Intel ME








Pingback: Microsoft Security Advisory for self-encrypting drives - gHacks Tech News