![]() [German]Kraus-Maffei, a chinese owned German manufacturer, fell victim to the blackmail Trojan Emotet, which paralyzed numerous computers in the company. After the district hospital Fürstenfeldbruck this is another victim, whose case became publicly known.
[German]Kraus-Maffei, a chinese owned German manufacturer, fell victim to the blackmail Trojan Emotet, which paralyzed numerous computers in the company. After the district hospital Fürstenfeldbruck this is another victim, whose case became publicly known.
Advertising
Emotet malware – an overview
Two days ago I warned German companies against a Emotet malware campaign within my German article Achtung: Emotet-Malware-Welle gefährdet deutsche Firmen. This was, because the Lower Saxony State Criminal Police Office (LKA-Niedersachsen, Germany), has issues a warning, that a malware campaign targeting German companies and spying on or damaging them via variants of the Emotet-Trojan.
The Emotet-Trojan is nothing new, Symantec published this article about this malware in summer 2018. The group behind the Trojan has been active since at least 2014 and had focused on bank customers so far. But now there seems to have been a strategy change by attacking infrastructure and companies in Europe.
The most critical component is the Emotet worm component, which makes it possible to expand into company networks. This poses a particular challenge for companies. In general, there has recently been a renaissance of malware with worm components to spread. Ransomware such as WannaCry (Ransom.Wannacry) and Petya/NotPetya (Ransom.Petya) are well-known examples.
Network propagation also means that victims can be infected without ever clicking on a malicious link or downloading a malicious attachment. Once on a computer, Emotet downloads and executes a spreader module. The module contains a password list that it uses to attempt to gain access to other computers on the same network, writes Symantec. Microsoft has published an article about this malware (deleted), with Windows Defender detecting some variants.
German District Hospital has been infected
German District Hospital Fürstenfeldbruck (in Bavaria) has been infected with ransomware mid of November 2018. The clinic has been offline for more than a week with it's computer systems, due to a with Emotet virus infection. I've covered this within my blog post German District Hospital: IT systems grounded by a virus.
Advertising
Current Emotet infection scheme
Emotet is currently distributed through infected Word documents with macros that are sent as invoices attachment or similar. The texts of the mail vary, some are written in German and are intended to prompt the recipient to open the attachment. The Trojan part of the malware evaluates a victim's address books and e-mails and forwards this data to the attacker. Then the Trojan is sent by mail (partly with correct address) to further targets. The following screenshot shows a more recent version of the mail published by the Lower Saxony State Criminal Police Office (LKA-Niedersachsen, Germany), as an example.
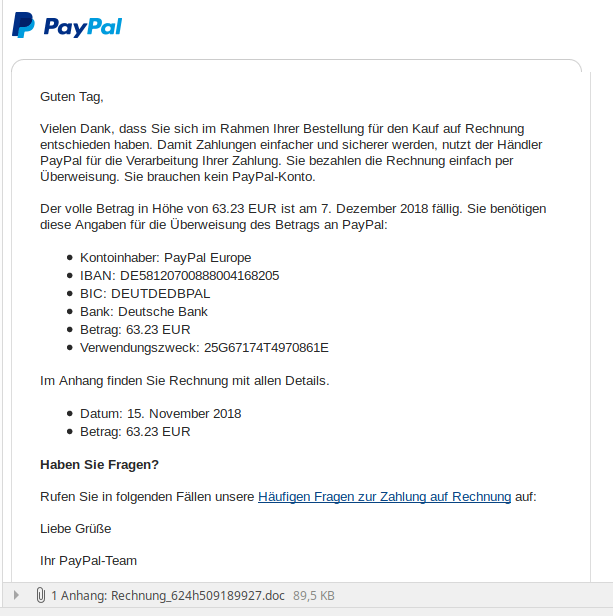
If macros are blocked, the malware tries to move the victim to open the attachment. If the malware succeeds in persuading the victim to disable Office macro protection, the malware reloads a spreader component. This component is able to spread over the network to other computer systems via the EternalBlue vulnerability that exists in Windows (and has long since been patched). I had some details within my German article Achtung: Emotet-Malware-Welle gefährdet deutsche Firmen.
Kraus-Maffei affected for '2 weeks' already
I became aware of the case through this comment within my German blog. Some German news sites reported (based on a short DPA broadcast) that the mechanical engineering company Krauss Maffei (according to its own statements) was the victim of a cyber attack. The infection took place 'two weeks ago' – the Trojan seems to have encrypted data disks and the company (according to its own statements) was faced with a ransom demand.
A company spokesman confirmed to DPA that following this attack, production at individual sites had to be significantly reduced due to computer failure. Meanwhile, the company sees itself 'on the way to normal' status. The reference to the Emotet-Trojan can be found in German news magazine FAZ, which published an article here.
German business magazine Das Handelsblatt has published this article, writing that the main location Munich with its 1,800 employees had been particularly affected. The company became aware of the attack on November 21, 2018. According to the report, the company then immediately interrupted its connections to its customers. It is not yet known that customers or suppliers were also affected by the Tojan.
Who's Kraus-Maffei?
I had mainly associated Kraus-Maffei with tanks and military vehicles – but this line of business probably belongs to Kraus-Maffei Wegmann GmbH. So it's a completely different company. Victim is Kraus Maffei Group, a company with 5,000 employees that offers complete solutions from injection moulding machines to trimming machines for plastics and rubber products as well as automation. The Krauss-Maffei Group was acquired in 2016 by the Chinese chemical group China National Chemical Corporation (ChemChina).
How can you protect yourself?
Finally, a few lines about what administrators in companies can do to raise the ramparts. Here are some general hints:
- The management should immediately issue a binding instruction that no attachments with .doc files or the like may be opened unless it is explicitly clear that this document really comes from the supposed sender and is not infected.
- Administrators should generally block macro execution in Office. If Office macros are required, signatures can be used to allow these documents.
- Windows systems should be up to date with the latest security software patches. That may be a problem in production environments, where million dollar drilling and welding machines are populated with Windows XP or Windows 7 SP1 as controller OS.
- In the network area, an appropriate protection should exist so that a compromised AD account cannot be used for lateral propagation (see my blog post Harden Windows networks with AD option against NotPetya).
Further hints to protect against ransomware may be found within the following articles:
Links:
7 tips to prevent ransomware (Symantec)
11 things you can do to protect against ransomware, including Cryptolocker (ESET)
Ransomware (Microsoft)
Similar articles:
German District Hospital: IT systems grounded by a virus
Bristol Airport affected by ransomware
#BadRabbit #Ransomware outbreak in Eastern Europe
News about (Not)Petya ransomware – Killswitch/vaccine found?
Petya ransomware is back – using WannaCry vulnerabilties
Ransomware WannaCry infected worldwide thousands of Windows systems
WannaCry & Co.: EternalBlue Vulnerability Checker and Crysis Ransomware Decryptor
No end for Cerber Ransomware in 2017
Petya-Mischa Ransomware variant GoldenEye
Advertising





