[German]US vendor Cisco has publicly disclosed another 0-day vulnerability (CVE-2023-20273) in IOS XE as of October 20, 2023. This vulnerability is already being exploited in the wild to compromise systems. The vendor plans to provide fixes for the CVE-2023-20198 and CVE-2023-20273 vulnerabilities probably on October 22, 2023 (US time). A vulnerability made public on Oct. 16, 2023, led to tens of thousands of infections. Now the number of "discoverable, infected" systems suddenly dropping to a few hundred.
[German]US vendor Cisco has publicly disclosed another 0-day vulnerability (CVE-2023-20273) in IOS XE as of October 20, 2023. This vulnerability is already being exploited in the wild to compromise systems. The vendor plans to provide fixes for the CVE-2023-20198 and CVE-2023-20273 vulnerabilities probably on October 22, 2023 (US time). A vulnerability made public on Oct. 16, 2023, led to tens of thousands of infections. Now the number of "discoverable, infected" systems suddenly dropping to a few hundred.
Advertising
Currently, Cisco administrators are unlikely to have a quiet time. In early October, the critical vulnerability CVE-2023-20101 was closed via emergency update. Then, as of Oct. 16, 2023, there was a security warning about a 0-day vulnerability (CVE-2023-20198) in IOS XE that allows privilege escalation via the Web UI (Over 32,000 Cisco components compromised via CVE-2023-20198 vulnerability).
Network devices running Cisco IOS XE include enterprise switches, access points, wireless controllers, and industrial, aggregation, and branch routers.
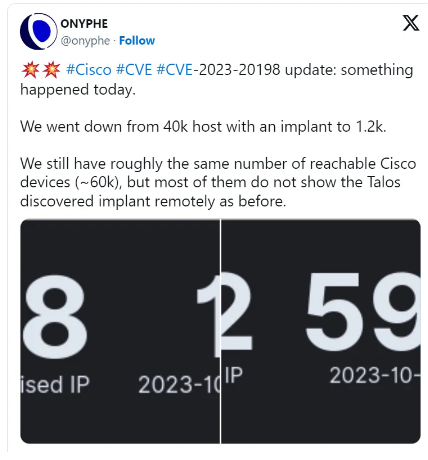
In the post linked above, I pointed out that tens of thousands of Cisco systems worldwide that are accessible via the Internet have now been compromised with an "implantant." The colleagues at Bleeping Computer report here that the number of compromised systems has even exceeded 50,000. However, a few hours ago, the number of compromised systems dropped to a few hundred.
Security researchers are now puzzling over what could be the cause of this steep drop in infection numbers. Because there are still about the same number of Cisco devices accessible via the Internet (~60k). But most of those instances no longer remotely display the implant Talos discovered. The security researchers' best explanation is that the devices previously identified as compromised are still compromised. But the attackers have probably adapted the implant and covered the tracks in such a way that the infection can no longer be detected (using the previous methods).
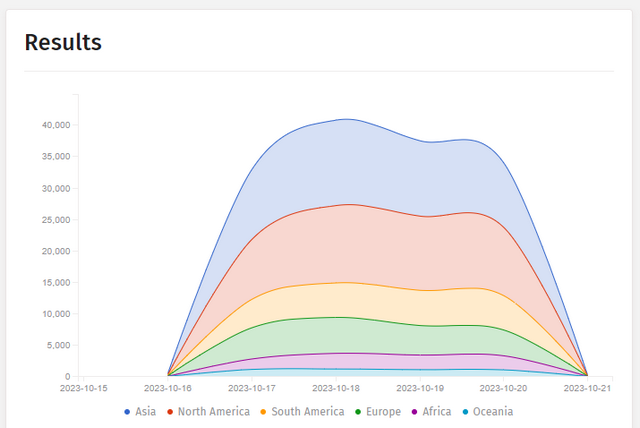
Infection of Cisco instances; source Shadow Server.
Advertising
Shadow Server has published the above graph showing the progression of infections of Cisco systems over time, reflecting the steep drop in infections. And now comes the next vulnerability (CVE-2023-20273), which is also being actively exploited to roll out an implant to systems. Cisco added the following text to its blog post:
Identified an additional vulnerability (CVE-2023-20273) that is exploited to deploy the implant. Fixes for both CVE-2023-20198 and CVE-2023-20273 are estimated to be available on October 22. The CVE-2021-1435 that had previously been mentioned is no longer assessed to be associated with this activity.
An additional vulnerability (CVE-2023-20273) has been identified that is exploited to deploy the implant. Fixes for CVE-2023-20198 and CVE-2023-20273 have been advised for October 22, 2023 (US time zone). The previously mentioned vulnerability CVE-2021-1435 would no longer be associated with this activity.
Explanation for decreased detections
Addendum: In the meantime, security researchers from Fox-IT have provided an explanation on Twitter for the sudden drop in the detection of compromised systems:
IMPORTANT We have observed that the implant placed on tens of thousands of Cisco devices has been altered to check for an Authorization HTTP header value before responding [1/3]
This explains the much discussed plummet of identified compromised systems in recent days. Using a different fingerprinting method, Fox-IT identifies 37890 Cisco devices that remain compromised. [2/3]
We strongly advise everyone that has (had) a Cisco IOS XE WebUI exposed to the internet to perform a forensic triage. We published steps on identifying compromised systems on our GitHub here: github.com/fox-it/cisco-i [3/3]
Patches available
The security advisory Multiple Vulnerabilities in Cisco IOS XE Software Web UI Feature states now that the first fixed software releases have been published in the Cisco Software Download Center.
Similar articles:
Over 32,000 Cisco components compromised via CVE-2023-20198 vulnerability