[German]Microsoft has disabled the MSXI ms-appinstaller protocol because it was being abused by malware groups. I remembered, that the vulnerability CVE-2021-43890 has been patched in Dec. 2021 and the protocol has been disabled long ago. Here is an overview of hat story.
[German]Microsoft has disabled the MSXI ms-appinstaller protocol because it was being abused by malware groups. I remembered, that the vulnerability CVE-2021-43890 has been patched in Dec. 2021 and the protocol has been disabled long ago. Here is an overview of hat story.
Advertising
App installer protocol deactivated
The ms-appinstaller URI (Uniform Resource Identifier) scheme (protocol) developed by Microsoft enables apps to be downloaded and installed directly from a web server from Windows 10 (v1607) onwards. This Microsoft page now states that this URI scheme is now disabled by default. However, the URI scheme can be activated by an administrator via group policy.
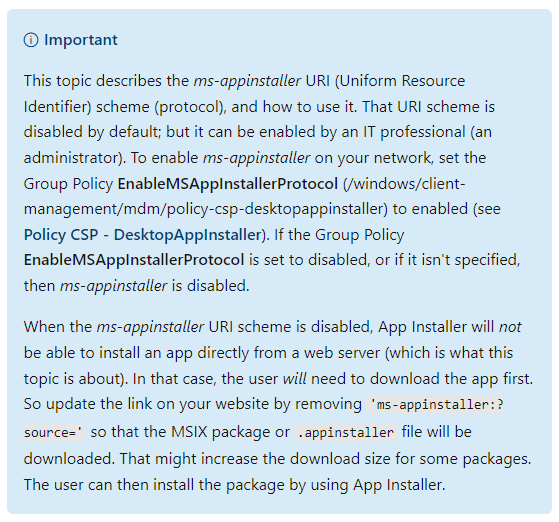
The explanation for this step can be found in the blog post Financially motivated threat actors misusing App Installer from December 28, 2023.
Since mid-November 2023, Microsoft Threat Intelligence has observed threat actors (some with financial addresses), such as Storm-0569, Storm-1113, Sangria Tempest and Storm-1674, using the ms-appinstaller URI (App Installer) scheme to distribute malware. The attackers are abusing the current implementation of the ms-appinstaller protocol handler as an access vector for malware, which can lead to the spread of ransomware.
Advertising
According to Microsoft, several cybercriminals are also selling a malware kit as a service that abuses the MSIX file format and the ms-appinstaller protocol handler. These threat actors distribute signed malicious MSIX application packages via websites accessed through malicious advertisements for legitimate popular software. A second phishing vector via Microsoft Teams is also used by Storm-1674.
According to Microsoft, the attackers probably opted for the ms-appinstaller protocol handler vector because it can be used to bypass mechanisms designed to protect users from malware. These include, for example, the Microsoft Defender SmartScreen and the integrated browser warnings for downloads of executable file formats.
In response to these findings, the ms-appinstaller protcol handler has been disabled by default. The Microsoft article her contains a detailed description of the issue and recommendations for administrators on the topic.
Hasn't CVE-2021-43890 been closed?
When I read the topic ms-appinstaller protocol is disabled, something rang in the back of my head "wasn't there an update for the vulnerability CVE-2021-43890"? And indeed, I found the blog post Microsoft disables MSIX ms-appinstaller protocol handler in Windows (Feb. 2022). After ransomware such as Emotet or BazarLoader abused the MSIX ms-appinstaller protocol handler, Microsoft deactivated it as protection in Windows "for the time being". This was the second action after CVE-2021-43890 was patched at this point in December 2021.
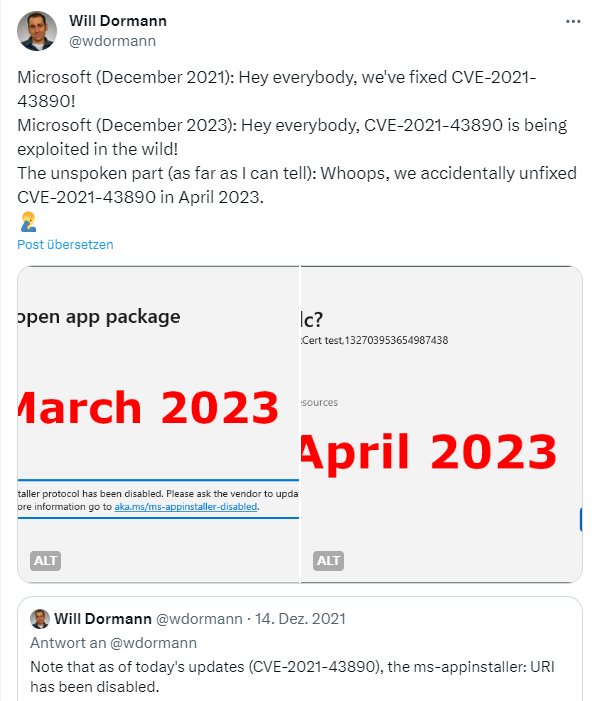
I came across the above tweet from Will Dormann. Dormann points out that the vulnerability CVE-2021-43890 was patched by Microsoft in December 2021. Now it says in December 2023 that the ms-appinstaller protocol was abused. According to Dormann, the patch for the CVE-2021-43890 vulnerability was accidentally removed again in April 2023, so the whole thing was vulnerable again. And now the ms-appinstaller protocol has been deactivated again.
When and how did Microsoft do this?
Addendum: At this point, it was unclear to me when and how the ms-appinstaller protocol was finally deactivated. There were no updates during the days – I guessed that the deactivation took place with the security updates of December 12, 2023. At least the post Why has the ms-appinstaller protocol been disabled? from December 15, 2023 can be found on MS Answers, which would fit.
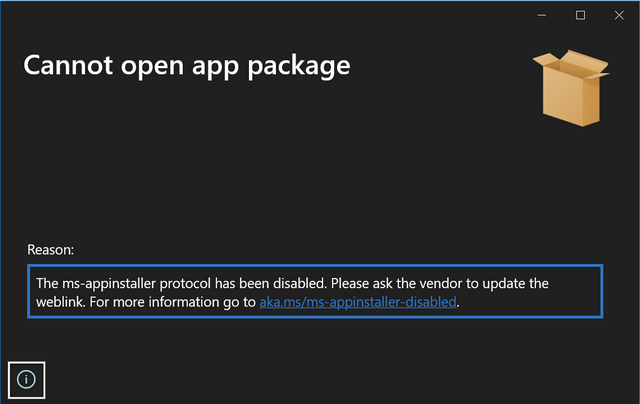
The person concerned posted the above image and writes that he started seeing this on December 13, 2023. There is also this summary on GitHub. At least it now explains why the log handler was deactivated. There is also an addendum dated December 4, 2023 on the MicrosoftDosc GitHub page for MSIX, where the deactivation is mentioned.
In the GitHub post referenced above, Giovanni Bozzano mentions that the protocol was deactivated again with the release of the MSXI app installer version 1.21.3421.0 on December 12, 2023. And there is the article Microsoft addresses App Installer abuse from MSRC, dated December 28, 2023, recommending administrators to install App Installer version 1.21.3421.0, to fix CVE-2021-43890.
The Techcommunity article here has an addendum, dated August 5, 2022, which states that the fix for activating the ms-appinstaller protocol handler in Windows 11 Insider Preview Build 25147 was rolled out for the Dev Channel. After this date, the re-activation was probably rolled out to the Windows 10/11 production versions. The tech community article also contains information on how to enable and disable the log handler via group policies. This clarifies when the deactivation happened.
Advertising