 [German]Following confirmation that the provider of remote maintenance software, AnyDesk, was the victim of a hack that also affected production systems, I have prepared some information in Part 1 and Part 2 of my series of articles (AnyDesk confirmed, they have been hacked in January 2024, Production systems affected – Part 1). In Part 3, I address topics that were brought to my attention by readers. It deals with unauthorized access attempts and sudden communication of the client with foreign URLs. Although I now classify these as "false alarms", the discussion may help some readers with their interpretation. And there is probably a first malware find. Below is a summary of these points.
[German]Following confirmation that the provider of remote maintenance software, AnyDesk, was the victim of a hack that also affected production systems, I have prepared some information in Part 1 and Part 2 of my series of articles (AnyDesk confirmed, they have been hacked in January 2024, Production systems affected – Part 1). In Part 3, I address topics that were brought to my attention by readers. It deals with unauthorized access attempts and sudden communication of the client with foreign URLs. Although I now classify these as "false alarms", the discussion may help some readers with their interpretation. And there is probably a first malware find. Below is a summary of these points.
Advertising
Suspicious cases reported from readers
My German blog post Störung bei AnyDesk, jemand betroffen? from January 2024 acted as a honeypot, providing me with the first indications of an incident as well as feedback from the reader affected at the time. Following the disclosure of the incident, I have received a number of information from readers in the past few days – and I have been in contact with two readers since this week (and before AnyDesk's disclosure) to discuss "unusual observations".
Case 1: Unauthorized access attempt
When I received the first vague indications of a cyber incident at AnyDesk this week, I asked my communities (X, BlueSky, Mastodon, Facebook groups) whether anyone knew more. In this context, a reader, I will call him John, contacted me in a private message because he had noticed an attempted unauthorized access in the run-up to the incident. I spoke to John on the phone last Friday, before AnyDesk made the disclosure, and I know some of the background. John observed an unauthorized access attempt (on a private laptop).
According to him, the system in question was running with permanent access by AnyDesk, although this was protected by a more complex password. John then received a request to authenticate this access on a second computer. If he had confirmed this, the unknown third party would have been in the system. Since, according to John, he had already experienced a ransomware case, he shut down his NAS and cut the internet connections. He then started checking for an attack.
The check was unsuccessful, but John told me: "I had configured unattended access with a password an this private notebook, and it looked like someone had brute-force cracked it – and it was a really complex password." The reader told me that he had sent the logs to AnyDesk support. But he never got a feedback.
I have the log file and John has also given me the ID of the third-party user. This user first requested access on December 29, 2023 via anynet.any_socket (via relay). However, this session was quickly terminated by this third-party user. The remote AnyDesk client version was 8.0.6, if I am interpreting the log correctly. The log then contains a second attempt from January 4, 2024 with the same ID, where someone tried to establish a background connection with access to the screen, keyboard, microphone, etc. (if I am interpreting it correctly). But was not allowed by John.
Advertising
The whole thing must remain as an unsolved suspicious case. I don't have the expertise to completely analyze the entries in the log file – there is no feedback from AnyDesk. In the run-up to this article, I asked John (who is a developer) whether the request could be the result of a typo by a third-party user. This cannot be ruled out. At the moment, I would vaguely classify this incident as a "false alarm".
Case 2: AnyDesk client with connect to playanext.com
Due to the reports here in the blog, administrators are now probably taking a closer look at what AnyDesk is up to in terms of connections. Georg got in touch yesterday and wrote that anydesk.exe had been blocked for execution by the endpoint solution and that an external security service provider had been activated. Checking the log files of the last 10 days led to a discovery.
The background, which is quite interesting and may concern some readers: The company itself does not use AnyDesk and is therefore not a customer of this provider. However, a foreign ERP software is used in the company, where AnyDesk is also rolled out for remote maintenance.
In this context, the contacted security service provider then found connections with the URL playanext.com (specifically api.playanext.com) in the log files and reported them to the customer. This probably rang all the alarm bells, as a command & control server was suspected. All connections were blocked and AnyDesk was prevented from running.
The reader later added that the systems on which this was noticed were running Anydesk version 8.0.7 and 8.0.6. Regarding an anydesk.exe, he writes that it has the SHA-1 hash: 0B82B980EEA1E8D2BE9E70E01FE1421AA38ABC7D and was compiled on 16.01.24 14:10:29.
This client was first detected by the endpoint solution of the corporate environment on 17.1.2024. The reader wrote that version 8.0.7 was probably already removed on the evening of 17.01.24 (it probably went back to 8.0.6). This can be seen from the AnyDesk log files, and the affected server is located in Turkey, the reader said. And he added: "The 8.0.7. was either not made available to the AutoUpdater at all or was immediately withdrawn."
Sysmon logged that the anydesk.exe directly called this URL. In the follow-up email, the reader said that playanext.com gave the impression of a software distribution. However, a Google search for "playanext.com reputation" left the reader with a mixed feeling.
I briefly touched on this in Part 2 of my German article and wrote that Fortigate definitely lists the URL or product as riskware. Something to do with tracking. But the swarm intelligence of the readership works, because reader THunter got in touch with this comment (thanks for that) and wrote:
Hello Günther,
the URL api.playanext.com was addressed by earlier Anydesk versions < 7.x. This was a residual API for license query, telemetry data and download control, which was still from philandro Software GmbH at that time.
In various SandboxReports from Joes, HybridAnalyse or AlienVault you will find Anydesk.exe samples from the years 2019-2021, which already called api.playanext.com at that time.
The URL api.playanext.com is often associated with malware because it is also misused for telemetry. However, there is no binary download from this URL.
The reader posted a link to the urlscan.io reports, where this URL is listed several times and the all-clear is given. I have also informed the reader of this and have now classified the whole thing as a "false alarm". However, the comments of the reader mentioned above suggest that the URL playanext.com is also used in the clients of the 8 version of AnyDesk.
Change of infrastructure in January
Blog reader Daniel, who is entrusted with AnyDesk in an IT company, had pointed out the disruptions in January 2024 to me and I then published the articleStörung bei AnyDesk, jemand betroffen? Daniel naturally reads the blog and wrote in an email to me.
I have been closely monitoring the network connections to and from AD since the fault occurred and have noticed multiple changes in the infrastructure.
As soon as the problem occurred, I thought of "bad guys" and I think something like that will come out soon. In any case, I am continuing to observe and am preparing appropriate measures. AD is no longer trustworthy for me.
The email reached me before AnyDesk disclosed the hack. Regarding "change in infrastructure", this means that network requests go to different network addresses than the day before. This was an indication to him that something was going on in the background and that the provider was restructuring and rebuilding the infrastructure.
Password change at AnyDesk
AnyDesk's announcement states that the passwords for customer access to the portals have been reset as a precautionary measure. There appear to be two portals, My Anydesk I and My Anydesk II. Accounts managed under My Anydesk I do not require a password change, whereas My Anydesk II does. However, I cannot judge which clients are managed where and why a password change is only required for one portal.
Problems with client download
Mark contacted me by e-mail this morning and wrote that AnyDesk is used across the board and that clients usually use their own client, which the company can generate via my.anydesk.com. He wanted to update all client versions on Sunday morning (including setting a new fixed password) so that the company can replace the client everywhere as a precautionary measure.
After logging in at my.anydesk.com, he was asked to set a password (see above). However, after he had adjusted the client version and wanted to save the whole thing, this did not work. The save button turns gray and rotates, but the changes are not saved.
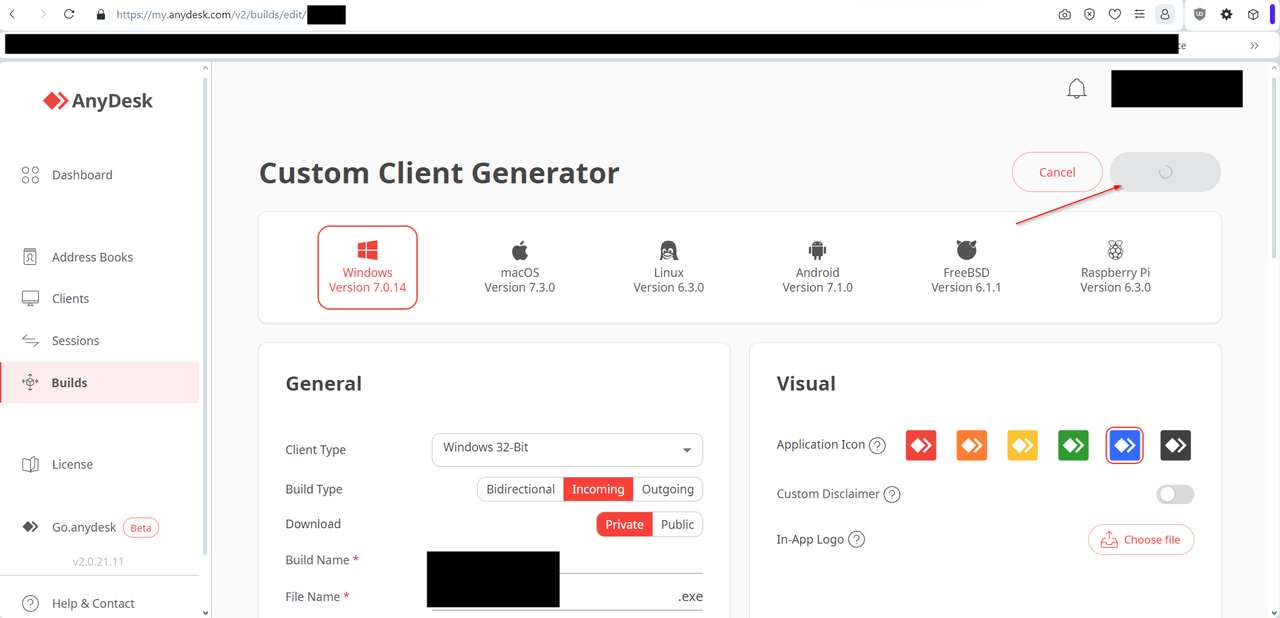
AnyDesk Custom Client Generator, click to zoom
The reader then added in a second email: Saving your own client versions works if you don't enter a password for full access. But that's exactly what we use for servers, so that nobody has to press "Accept" and as soon as I enter a password (either one generated from KeePass or one I made up myself) the save button turns and nothing happens. Perhaps it will help readers who also generate clients.
False alarm when downloading AnyDesk 8.0.8?
One user posted on Facebook that the latest update was immediately blocked from his system "yesterday" (Friday, 2.2.2024) because it was compromised according to the AV software.
-> performed mit winget upgrade –all
< 8.0.6 auf Version 8.0.8
AnyDesk [AnyDeskSoftwareGmbH.AnyDesk] Version 8.0.8
The download was from download.anydesk.com/AnyDesk.exe. Probably a false alarm, I guess – but nobody needs it.
Suspicious activity on Virustotal
A blog reader sent me this link to Virustotal yesterday. Someone uploaded a file OKJhBah6[dot]exe created with .NET to Virustotal for "testing" at the end of October 2023. This is recognized as malware by 48 scanners, which is good.
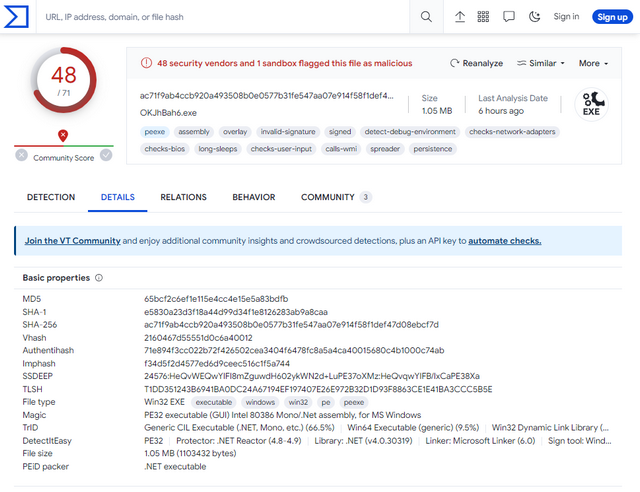
Less good is the realization that this file was signed with a certificate from "philandro Software GmbH". I could not compare the details (serial number of the certificate) (Bleeping Computer has the information here). But the old AnyDesk clients were signed with a certificate from "philandro Software GmbH". I naively assume that someone is developing malware and testing whether the result is recognized by virus scanners. It's not a "smoking gun" either – but it's strange that malware was signed with a certificate from "philandro Software GmbH".
A reader informed me by e-mail that he had downloaded a current file [with the client] from his account at the My Anydesk 1 portal due to the above Virustotal find and looked at the signature. The statement is that the two serial numbers are identical. AnyDesk still has this signature in the 7.0.14 clients, which was downloaded on 4.2.2024 today. What the reader noticed: In contrast to the normal version of the client, the signature with sha1 algorithm is missing in this file. A newly created client file still contains exactly the same signature. That's a bit strange.
My 2 Cents
The confirmation from AnyDesk on Friday night (2.2.2024) states that they have overcome the compromise and that there is no longer any danger of using AnyDesk as a client. The above cases show that there is now a lot of uncertainty among customers and new questions are constantly arising. I think this will really get going on Monday, February 5, 2024, because administrators will have to decide how to proceed.
Two notes at this point: In Part 2, I linked to this GitHub post where someone posted a Yara rule for the compromised AnyDesk certificate. During my research, I now came across the Sentinel One post Customer Guidance on Emerging AnyDesk Cybersecurity Incident, where their specialists give initial indications, but write that the situation is "still unclear". They say that you should go to client v 8.0.8.
Everything that has been communicated by AnyDesk so far remains too vague – we don't even know when the compromise took place. According to the provider, the incident has been investigated with Crowdstrike – so there should be an analysis. If you haven't been following the coverage on IT sites or here on the blog, you haven't noticed the whole thing yet. In my opinion, it is an example of how not necessarily to react to a cyber incident.
And now I'm going to write part 4, because the customer credentials for the AnyDesk customer portal are offered in the internet.
Articles:
AnyDesk confirmed, they have been hacked in January 2024, Production systems affected – Part 1
AnyDesk hack undercover – more information and thoughts – Part 2
AnyDesk hack undercover – Suspicious cases and more – Part 3
AnyDesk hack undercover – Access data offered for sale – Part 4
AnyDesk hack – A review – Part 5
AnyDesk hack – Review of the German CERT BSI report – Part 6
AnyDesk hack – Notes on exchanging certificates for Customs clients 7.x – Part 7
AnyDesk hack – more details (FAQ from Feb. 5, 2024) – Part 8
AnyDesk hack already noticed on December 20, 2023? – Part 9
AnyDesk hack confirmed as of December 2023; old certificate recalled – Part 10
AnyDesk hack: Revoke chaos with old certificates? – Part 11
AnyDesk hack: Newly signed clients available; what are your experiences? – Part 12
Similar article:
Störung bei AnyDesk, jemand betroffen?
AnyDesk: Be careful in using that remote support software








I have thrown out Teamviewer for all customers and introduced AnyDesk. In the last 4 years I had written at least 10 emails to anydesk. Sometimes I didn't receive any answers and sometimes it took several weeks until someone got back to me.
Why I'm writing this: anydesk probably has the best (imho) remote control tool, which requires very smart developers, which anydesk definitely has. What anydesk definitely does not have is customer service, case handling and above all it is extremely worrying that anydesk apparently has zero idea about communication. In an age where 100 breaches happen every week, a made-in-europe software house should know how to communicate. Anydesk has earned #failed as a hashtag. Food for speculation.
Reputation destroyed, great performance, anydesk management, congratulations!
I reported suspicious access requests back in December, based on an attack my former company received the Monday before Thanksgiving.
They had multiple anydesk IDs and passwords while some targets reported mouse movements without the authorization request to the end user.
I sent them the stack of trace files from all the suspect workstations and they've responded with crickets, at least through mid January when I was let go and can't follow up on the support ticket.
Thanks, I got similar reports from readers – but I have no "smoking gun". More has to come in that article series – have to check a few details.