 [German]The successful cyberattack on AnyDesk, a provider of remote maintenance software, is making quite a stir. Officially, the incident was confirmed by AnyDesk on February 2, 2024 (specifically Friday evening at 10:44 pm). Almost nothing is known – neither when, nor what exactly was hacked. I've been working on this topic since January 2024 and an overall picture is emerging from many bits and pieces of information. I now have various sources that indicate that the hack was noticed as early as December 20, 2023. Addendum: AnyDesk has confirmed my suspicions, see my text below.
[German]The successful cyberattack on AnyDesk, a provider of remote maintenance software, is making quite a stir. Officially, the incident was confirmed by AnyDesk on February 2, 2024 (specifically Friday evening at 10:44 pm). Almost nothing is known – neither when, nor what exactly was hacked. I've been working on this topic since January 2024 and an overall picture is emerging from many bits and pieces of information. I now have various sources that indicate that the hack was noticed as early as December 20, 2023. Addendum: AnyDesk has confirmed my suspicions, see my text below.
No details from AnyDesk
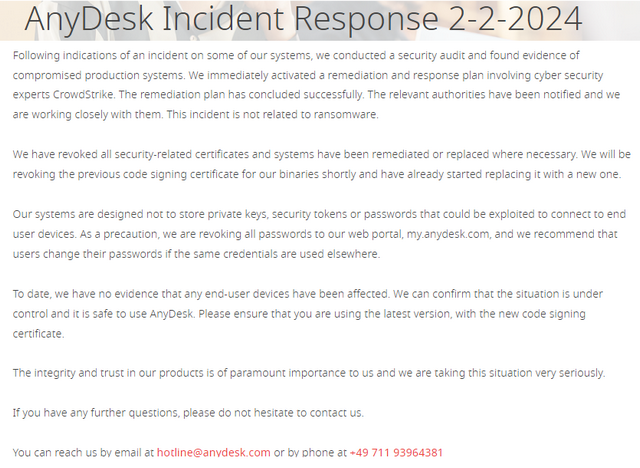
As mentioned above and in my posts at the end of the article, a cyber incident at AnyDesk that affected the production systems has been confirmed since February 2, 2024. I received the press release (Friday night) at 22:44. I have again pulled out the screenshot of the statement:
The announcement says next to nothing. In the article AnyDesk confirmed, they have been hacked in January 2024, Production systems affected – Part 1 I had compiled some more information that I had. But nothing is known for sure, was my conclusion.
On February 5, an update of AnyDesk was published (see AnyDesk hack – more details (FAQ from Feb. 5, 2024) – Part 8), which links to an FAQ from AnyDesk. I had extracted some insights from the FAQ in my linked article.
The company could have com forward and provided more details. Unfortunately, the FAQ again leaves the essential questions (when was what hacked) in connection with the incident unanswered.
When was the compromise noticed?
What is striking about the entire story regarding the official announcements by the provider AnyDesk is that there is only ever a minimal admission of what is absolutely necessary. "Yes, we were hacked" – "we immediately took countermeasures" – "everything is fine again, users can safely use AnyDesk again".
This may all be true – but there is a lack of transparency. To this day, we do not officially know when the attack took place, what exactly was compromised and whether private keys and source code were extracted. There are rumors that keys and source code may have been extracted – but this has not been officially confirmed or denied.
In the post AnyDesk hack – more details (FAQ from Feb. 5, 2024) – Part 8, I tried to derive certain findings from the FAQ and explained what was compromised (probably Proyx servers, which was admitted). And even this announcement is open to interpretation and misunderstanding, as the discussion on the post shows.
In the blog post, I also extracted the information from the AnyDesk FAQ, which states that the attack was noticed in mid-January 2024. But there is a suspicion that says an attack was noticed as early as December 20, 2023. My gut feeling told me, based on a reader observation, that something could have already been going on at the end of 2023 for a week now.
The French ANSSI report
Yesterday I came across a warning from the French security authority ANSSI (they are the equivalent of the German BSI or US CISA) as part of the preparation of the article AnyDesk hack – more details (FAQ from Feb. 5, 2024) – Part 8. In a message dated February 5, 2024, the French CERT refers to information from German BSI dated January 29, 2024. The publicly accessible message states that the BSI had been notified of a cyber incident at AnyDesk. The following statements in the ANSSI warning are noteworthy:
- The source code of the applications developed by the publisher as well as certificates and private keys may have been stolen.
- The ANSSI recommends that French users check their systems for the presence of AnyDesk and, if present, look for anomalies dating back to at least December 20, 2023.
I have described the details in the linked blog post. It was at this point that I first shuddered when reading the ANSSI report. The authority refers to BSI communications that the German public never got to see (but only a small circle of addressees knows about).
A second source
In the meantime, a second source (outside the BSI), who wishes to remain unnamed, has contacted me and confirmed my suspicions. According to the source, there is a non-public document from the BSI (which I do not know, however), which states that AnyDesk probably informed the authority that "data may have already flowed out" on December 20, 2023. This information or accusation is now in the air, and only AnyDesk could confirm or deny it and disclose details.
There are questions upon questions
I cannot say whether this is true and whether December 20, 2023 was also the day of the compromise, as I do not know the classified BSI documents. For me, this context now explains the BSI's reaction of issuing a warning dated January 29, 2023 to operators of critical infrastructure with the classification TLP AMBER:STRICT, and then on February 5, 2024 (one weekend after the vague confirmation of the hack by AnyDesk) to issue a less meaningful notification to the public.
I had also a statement from the press speaker of German BSI, who told me "The BSI cannot confirm that it has been aware of the hack since the end of December." Might be translated to: The BSI was not informed about the incident by December 20, 2023. It remains unclear when the information about the AnyDesk hack reached the BSI. These "assumptions" and the concrete information from the public French ANSSI document give rise to burning questions for me, which I will put into plain language:
- When did the attack take place and how long had the attackers been in the system?
- How were the attackers able to penetrate the production system and how far did they penetrate, or what was compromised/extracted?
- Have the attackers already been able to access customer systems and gain permanent access?
AnyDesk denies the latter in the FAQ, but you can only believe the "nothing has happened for customers" statement from AnyDesk GmbH – or not. But let me put it cautiously: How can a customer decide on the basis of this information whether he can still (safely) use the remote maintenance software? The French ANSS document provides clear instructions for action, which I outlined in the article AnyDesk hack – more details (FAQ from Feb. 5, 2024) – Part 8.
The question also arises: What happened from December 20, 2023, when my suspicion of a compromise was confirmed, until the BSI was notified? AnyDesk claims to have investigated and concluded the incident together with CrowdStrike. Then there should be answers to the above questions, which AnyDesk customers should be very interested in.
Addendum: As of February 7, 2024, AnyDesk has updated the FAQ on the incident (I haven't noticed it during translating my German post into English) and added the following note:
"Diligent forensic investigation revealed that the incident had started in late December 2023."
So what I have outlined above (since Feb. 6, 2024 in my German editions) from various sources is now confirmed (thanks to the reader for pointing this out). What remains is the answer to the question raised below as to how the attackers gained access to the system and whether Atlassian was a gateway.
As AnyDesk advertises in its first announcement: "The integrity and trust in our products is of paramount importance to us and we are taking this situation very seriously. The integrity and trust in the products has definitely been "cracked" by the incident, and in my view the disclosure to date is definitely not suitable for restoring "trust in the provider".
More pieces?
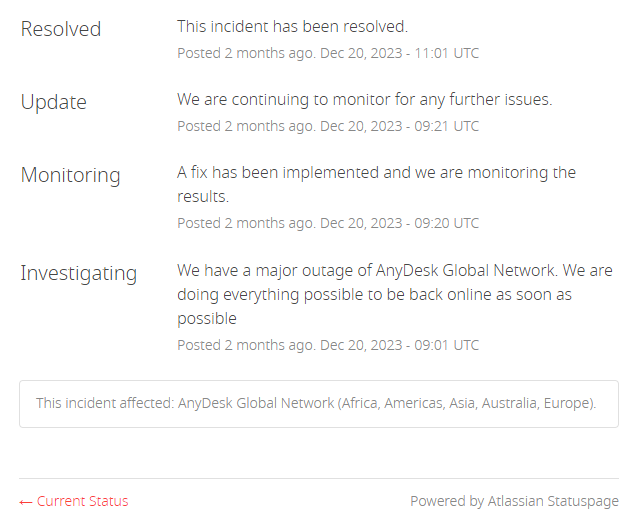
Addendum: There is now further feedback from readers with observations on each article on AnyDesk. In the following comment, Henry refers to an incident entry from December 20, 2023 at AnyDesk (see screenshot below).
There was a global outage of the AnyDesk network for two hours. Of course, there could be many reasons for this, but the coincidence with the above date is striking.
Then there's a comment from a reader who wonders whether there was an intrusion on or before November 9, 2023. I think the reader is alluding to my post AnyDesk hack undercover – Suspicious cases and more – Part 3, where I mentioned a malware sample uploaded to VirusTotal. In the VirusTotal listing, November 9, 2023 is listed as the signature date, for which a certificate from philandro Software GmbH was used. A certificate from this company was also used by AnyDesk and will be recalled soon. But they are probably different certificates.
At this point, however, I noticed that AnyDesk has based its status page on Altassian. At this point, all alarm bells rang for me, because there were several warnings about security vulnerabilities in Altlassian Confluence in October and November 2023. I had reported on this at the end of October 2023 in the German article Kritische Schwachstelle (CVE-2023-22518) in Atlassian Confluence-Servern. These are not hard facts, but speculations. But it could be a hint that there is more in the dark. For customers it means that they should check their logs for "anomalies" back to mid October 2023. I'm curious to see if a forensics report will ever be made public.
Articles:
AnyDesk confirmed, they have been hacked in January 2024, Production systems affected – Part 1
AnyDesk hack undercover – more information and thoughts – Part 2
AnyDesk hack undercover – Suspicious cases and more – Part 3
AnyDesk hack undercover – Access data offered for sale – Part 4
AnyDesk hack – A review – Part 5
AnyDesk hack – Review of the German CERT BSI report – Part 6
AnyDesk hack – Notes on exchanging certificates for Customs clients 7.x – Part 7
AnyDesk hack – more details (FAQ from Feb. 5, 2024) – Part 8
AnyDesk hack already noticed on December 20, 2023? – Part 9
AnyDesk hack confirmed as of December 2023; old certificate recalled – Part 10
AnyDesk hack: Revoke chaos with old certificates? – Part 11
AnyDesk hack: Newly signed clients available; what are your experiences? – Part 12
Similar article:
Störung bei AnyDesk, jemand betroffen?
AnyDesk: Be careful in using that remote support software
Kritische Schwachstelle (CVE-2023-22518) in Atlassian Confluence-Servern
Atlassian verstärkt Warnung vor Ausnutzung der Confluence-Schwachstelle CVE-2023-22518




What a mess!!!!
So now they have acknowledged the date of Dec 20 2023, but still it could have been earlier. All of this secrecy is really hurting their reputation. But still, only to the few of us who actually know about this accident. The vast majority of their users know nothing about it because they have never published anything on their home page or twitter account. Also, the Italian CERT has not published anything about it. This whole mess is unnoticed by the majority of Anydesk users.
I'll have to pay for one more year because their TOS states that I cannot withdraw from my contract when there are less than 30 days left before the next payment (I had 15 days left when the accident was discovered in the first days of February) and I don't really want to make a fuss about it, but this is the last time I pay for their service.
I have currently installed Rustdesk (open source version) on my own server and I plan on using it even if it's not exactly as good as Anydesk. I'm quite afraid of it too, actually, because it seems no one cares about security anymore.
I have also made a list of every password I have typed into anydesk sessions since Nov 1 2023 (by reading my work logs) and I am now in the hard process of changing all of these passwords while NOT typing them again into an Anydesk session, which is quite hard when I have to reconfigure remote computers for people who cannot change the password themselves because they are not proficient enough.
What a mess, indeed.
In part 10 I mentioned, that a 3rd party has asked DigiCert to revoke the certificate – so some AnyDesk users will be awakening soon.