 [German]A frustrated buyer of a used VW vehicle was unable to register for Connected Car because the data was sent to the previous owner. So he took a closer look and was able to determine the server access data through OTP bypassing. He then used the chassis number to obtain the vehicle history and the previous owner's personal data. The incident took place in India – but I'm not sure whether the VW app "My Volkswagen" doesn't handle the whole thing in exactly the same way.
[German]A frustrated buyer of a used VW vehicle was unable to register for Connected Car because the data was sent to the previous owner. So he took a closer look and was able to determine the server access data through OTP bypassing. He then used the chassis number to obtain the vehicle history and the previous owner's personal data. The incident took place in India – but I'm not sure whether the VW app "My Volkswagen" doesn't handle the whole thing in exactly the same way.
I came across the following tweet about the facts that white-hat hacker LoopSec documented on Medium in the article Hacking My Car, and probably yours— Security Flaws in Volkswagen's App.
The curse of modern used cars
Buying a modern used car in the age of connected cars is turning into a hurdle race for new owners and a data risk for previous owners. A technology fan bought a used car from VW in 2024. As a technology fan, he wanted to explore the connectivity functions. As soon as he parked his newly purchased car, he installed the My Volkswagen (ŠKODA Auto Volkswagen India Pvt Ltd) app on his smartphone.
How to register in the app as buyer of a used vehicle?
During setup, he was asked for the vehicle identification number (VIN) of the car – this can be found directly on the dashboard and can be read through the windshield. In the next step, a four-digit OTP (One-Time Password) was requested. Obtaining this code should be child's play.
The OTP was sent to the previous owner's phone. The buyer called the dealership to get the previous owner's contact information. Although he was given this phone number, the previous owner could not be reached by phone. A text message had gone unanswered after an hour.
This encourages experimentation. The buyer impatiently tried to enter some random codes to see if they worked. They didn't, of course, but even after about 10-15 failed attempts, the app didn't block the buyer from trying again.
Brute force OTP attack
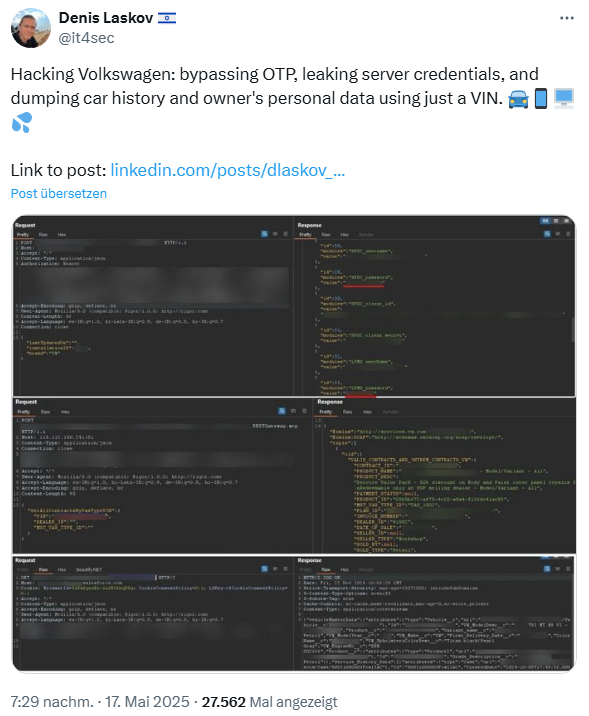
The buyer wondered what would happen if he tried all 10,000 combinations? Would he be locked out? He configured his iPhone so that he could use his Burp Suite to analyze the OTP requests. In doing so, he came across various API calls, one of which could send new OTPs to the server. Since the Burp community version of the suite was quite slow to send the OTPs via API, he developed a Python script documented in the Medium article.

This encourages experimentation. The buyer impatiently tried to enter some random codes to see if they worked. They didn't, of course, but even after about 10-15 failed attempts, the app didn't block the buyer from trying again.
Vulnerability analysis
At this point, the buyer's curiosity was piqued and he analyzed which vulnerabilities the app communication with the VW server would still reveal.
Vulnerability 1: Internal access data in plain text
An API endpoint revealed passwords, tokens and user names for various internal services in plain text. These included internal VW applications, payment processing details and even CRM tools such as Salesforce.
Vulnerability 2: Personal data of the vehicle owner
Access to vehicle data in the app is controlled via the chassis number.
According to the white-hat hacker, another API endpoint contained all service and maintenance packages ever purchased for the car for the specified chassis number.
Each service package entry contained extensive customer information, including names, phone numbers, mailing addresses, email addresses, vehicle details (model, color, registration number, VIN, engine number), active service contracts, purchase dates and payment amounts, etc.
Vulnerability 3: Vehicle service history
Another endpoint, retrievable via the VIN, contained the service history and details of the work carried out on all visits to the service center for any given vehicle.
For each workshop visit, there was an entry with details of the work carried out, the customer's personal details and even the results of the customer survey for each of these visits.
Full disclosure of all information via API
Other API endpoints provided the individual with vehicle telematics data and in some cases even "educationQualification" and "drivingLicense" numbers. The person in question has documented the details in the Medium article linked above.
The case shows the extent of the disclosure of customer data in this case. Anyone could add a vehicle to the app and then gain access to all available information and controls for the vehicle. This included the vehicle's location, engine condition, fuel statistics, tire pressure and geo-fencing controls.
In addition, all personal data such as address, phone number, email, driver's license and even the vehicle owner's maintenance history, complaints and problems were accessible.
The whole thing reminds me of the situation outlined in the blog post VW data leak: terabytes of location data from electric vehicles on AWS, where personal data (who was where in the brothel and when) of vehicles was accessible. Here, too, the VW app played an inglorious role.
The case shows once again that the always connect and app craze is causing people to lose control of their data. Ok, the "hacker" contacted VW in 2024 and pointed out the problems. It took some time, but the problems were supposedly fixed on May 6, 2025.
Similar articles:
Tesla vehicle data collection
Bluetooth Low Energy vulnerability and the Tesla car theft
Server error: Tesla vehicles could not be opened remotely
Car safety: Kia Challenge and Hyundai Key found on the web
Honda and Acura also had a Year 2K22 bug
Software: Our grave as future car owners?
Security incident: Source Code for Mercedes OLU leaked
Vulnerabilities in connected cars allow remote access at Honda, Nissan, Infiniti, Acura, etc.
Car safety: Kia Challenge and Hyundai Key found on the web
New cars as a privacy night mare; Mozilla investigates situation in the U.S.
Keyless systems in cars in 2024 still easy to hack
VW data leak: terabytes of location data from electric vehicles on AWS



