![]() In March 2017 a new attack, named DoubleAgent, has been published. Attackers can use Microsoft Application Verifier shipped in Windows to bypass antivirus software.
In March 2017 a new attack, named DoubleAgent, has been published. Attackers can use Microsoft Application Verifier shipped in Windows to bypass antivirus software.
Advertising
The details has been published a few days ago. Security researchers at Cybellum discovered a new way to bypass antivirus software. Microsoft ships the tool Microsoft Application Verifier within all Windows version. Application developers may use this tool to test code for runtime errors. This requires to load a DLL within the app to be tested. Researchers at Cybellum has discovered, that it's possible, to load an own 'verifier DLL' instead of the DLL provided from Microsoft Application Verifier.
It requires just a new Windows registry key to set the name of the application to be hijacked and set the name of the DLL. This can be used, to obtain control of an application – and it also works, if vendors protects their antivirus product registry entries against this szenario.
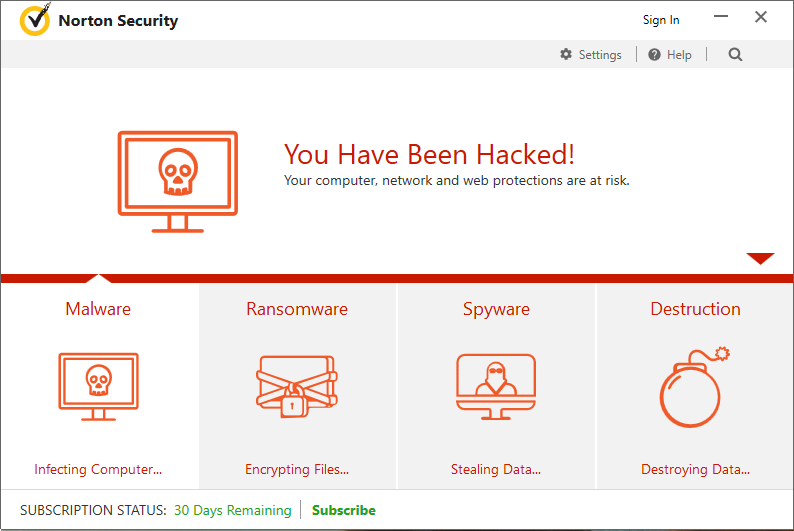
(Source: Cybellum/Bleeping Computer)
The researchers at Cybellum created a proof-of-concept attack, to bypass antivirus software. The above screenshot shows a modified Norton Security dialog after an attack. Currently many antivirus vendors are affected:
Avast (CVE-2017-5567)
AVG (CVE-2017-5566)
Avira (CVE-2017-6417)
Bitdefender (CVE-2017-6186)
Trend Micro (CVE-2017-5565)
Comodo
ESET
F-Secure
Kaspersky
Malwarebytes
McAfee
Panda
Quick Heal
Norton
Advertising
Some vendors like Malwarebytes version 3.0.6 Component Update 3, AVG version 16.151.8007 and Trend-Micro has delivered patches. Other vendors will surely follow. A DoubleAgent attack may be used for:
- deactivate security solutions and make them blind for malware attacks
- misuse security software as a proxy to attack local computer networks
- grant the highest system privileges to malware programs
- misuse security software to hide and filter data transfer made by malware
The proof of concept may be used to damage systems and misuse the infected systems for DDoS attacks. Further details may be found at Bleeping Computer.
Advertising





