 [English]Interesting story – a security researcher has developed a tool called Raccine as a simple protection against ransomware. This should prevent ransomware or other malware from deleting the volume shadow copies on Windows NTFS drives.
[English]Interesting story – a security researcher has developed a tool called Raccine as a simple protection against ransomware. This should prevent ransomware or other malware from deleting the volume shadow copies on Windows NTFS drives.
Advertising
Ransomware deletes VSS copies
When a Windows system is infected by a successful ransomware attack, the malware not only encrypts all accessible data files. To prevent the user from being able to make copies for recovery, it also scans for backup files. And finally, ransomware typically deletes the volume shadow copies of files stored on NTFS drives. This is because it might be possible to restore a previous copy of the document file from these. The Windows function Previous Version or the Shadow Explorer make this possible. If the volume shadow copies are deleted, nothing can be restored.
Protection for VSS copy deletion
Florian Roth, security researcher, has published the free tool Raccine on Github. His thought was: If ransomware deletes the volume shadow copies, you would need something that prevents exactly this process in case of a ransomware infection. He writes about this:
We [as security researchers] often see ransomware deleting all shadow copies with vssadmin. What if we could simply intercept this request and terminate the calling process?
The following screenshot shows the processes and the call of vssadmin to delete the volume shadow copies. This is exactly where Roth comes in with his ransomware protection.
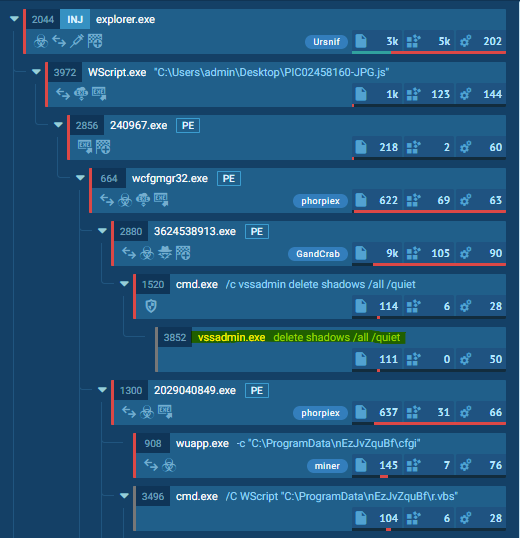
He uses an approach to register a 'debugger' for vssadmin.exe (and wmic.exe), which should monitor all VSS operations. His protection software raccine.exe is registered as debugger. Raccine is a program that first collects all PIDs of the parent processes and then tries to kill all parent processes, as a protection against ransomware and the attempt to delete volume shadow copies. Roth considers his method to be quite general. No system file (vssadmin.exe or wmic.exe) has to be replaced, which avoids integrity problems. In addition, the changes are easy to undo (the debugger only needs to be unregistered to disable monitoring). The protection software raccine.exe should work on all Windows versions from Windows 2000 on. No running executable file or additional service is required (agentless).
Advertising
However, every user must be aware that if the protection software raccine.exe is enabled, the legitimate use of the command:
vssadmin.exe delete shadows
(or any other command combination on the black list) is no longer possible. This becomes a problem when backup functions are started that use the shadow copies to back up the system files. In addition, the method fails if malware processes do not belong directly to the processes in the tree from which vssadmin.exe was called (e.g. called via schtasks).
The author writes that the use of the tool is at your own risk. The complete project is available here on Github. There you can also find more information about the tool, installation and uninstallation, and the download.
Advertising







