 [German]The successful cyberattack on the provider of remote maintenance software, AnyDesk GmbH, has caused quite a stir. One problem for users of AnyDesk – at least in my eyes – is that the provider is very tight-lipped about the details. We don't know what happened, we don't know when something happened. However, there are always bits and pieces of information from the readership that fall into place like pieces of a puzzle. Below I try to complete this picture, especially after AnyDesk published an FAQ hours ago.
[German]The successful cyberattack on the provider of remote maintenance software, AnyDesk GmbH, has caused quite a stir. One problem for users of AnyDesk – at least in my eyes – is that the provider is very tight-lipped about the details. We don't know what happened, we don't know when something happened. However, there are always bits and pieces of information from the readership that fall into place like pieces of a puzzle. Below I try to complete this picture, especially after AnyDesk published an FAQ hours ago.
Lack of transparency as a problem
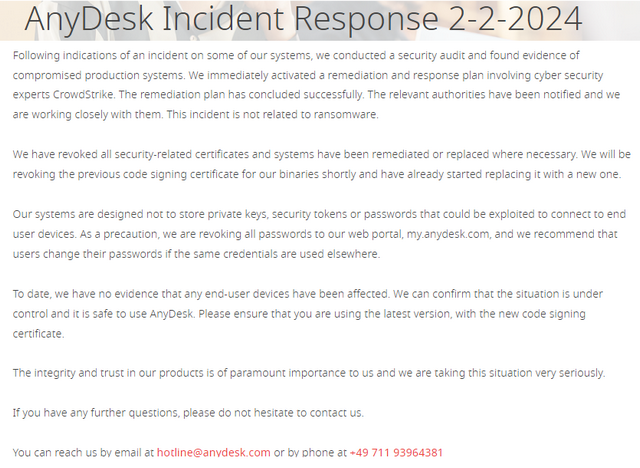
Till now AnyDesk has not released anything in detail to the general public, describing what and when the incident happened. There is no forensics report, just a thin announcement confirming the hack (see image below) from Friday, February 2, 2024.
I have compiled details I know in the article AnyDesk confirmed, they have been hacked in January 2024, Production systems affected – Part 1, as far as the provider has disclosed them, as well as I got some background. AnyDesk then only writes that they have no evidence that end points are affected. They also confirm that the situation is under control and that AnyDesk is safe to use.
A forensics report that could reveal details is not known to the public. The report should exist, as AnyDesk states in the text above that an action plan with countermeasures has been initiated and successfully implemented with the help of CrowdStrike's security experts. The only fact that can be found in the text above: AnyDesk rules out ransomware as the cause. And they write that they have replaced and will replace the necessary certificates.
An FAQ with some new information
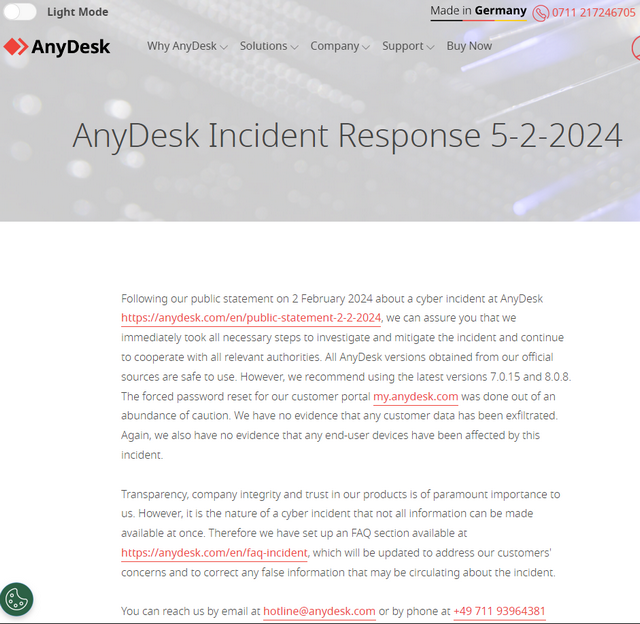
Several blog readers have pointed out to me (thanks for that) that there is an update to the Incident Response Report as of February 5, 2024, which links to an FAQ from AnyDesk that provides some answers to questions.
With knowledge of the overall complex, the FAQ makes it possible to confirm some assumptions. I would like to summarize a few points for the readership that I now understand.
What does an attack on the production environment mean?
AnyDesk's first report states that there were "indications of an incident in some of its own systems". An immediate security audit then provided "evidence of compromised production systems".
- In the FAQ dated February 5, 2024, there is a reference for the first time that the "incident" took place in mid-January 2024. A security audit found evidence of compromised production systems.
- This FAQ states that two AnyDesk relay servers from Europe (specifically Spain and Portugal) were affected by the incident.
- AnyDesk writes that customers who were connected via relay servers outside Europe (e.g. USA, Asia, Africa, Australia, South America) and outside the affected location zone (Spain and Portugal) are not affected by the incident.
AnyDesk writes that connections to the customer portal "my.anydesk.com I" are explicitly not affected. If login data was already stored in the client, i.e. it was not entered manually by the user, these systems are also not affected by the incident.
Why the password reset for the customer portal?
AnyDesk does not store any private keys, security tokens or customer passwords on its systems. Only when a password is entered to log in is this login data transmitted to the AnyDesk server via TLS/SSL encryption via relay servers. For remote access between AnyDesk clients, they only connect to the server of the customer portal "my.anydesk.com II".
The evaluation of the cyber incident revealed that there was a theoretical risk that the access data could have been compromised. The boundary conditions are described in the FAQ. As a precautionary measure, it was then decided to reset the customer passwords for the customer portal.
The above explanations also clarify why only customers who logged on to the "my.anydesk.com II" customer portal at the weekend were asked to change their password, while this was not the case for the "my.anydesk.com I" customer portal. In the meantime, however, it seems that passwords are also being changed on the "my.anydesk.com I" customer portal, as various readers have reported.
What certificates have been changed?
There have been heated discussions in the German blog about the statement "We have revoked all security-related certificates and systems have been remediated or replaced where necessary." and the question, what that means.
- The security-relevant certificates on the AnyDesk relay servers and servers were replaced immediately in order to secure this infrastructure.
- However, there are still the certificates with which the AnyDesk clients are digitally signed. The certificate for client version 8.0.8 and client version 7.0.15 has been replaced.
This means that all AnyDesk versions obtained from the manufacturer's official sources are safe to use. The use of the latest client versions mentioned above is recommended. AnyDesk has revoked all security-relevant certificates (of the servers). The code signing certificate for the binaries will only be revoked in the future – once it has been ensured that all clients have been updated.
No malware, no abuse
What also emerges from the FAQ is the clear statement from AnyDesk that no malware was distributed with the client versions from the AnyDesk servers and that there was no abuse. This dispels the theory that client version 8.0.7, which was only available for a few hours, could have been infected. And AnyDesk also states that session hijacking is extremely unlikely. This answers many open questions.
I got a reader report, saying that that "anomalies" had been detected with one customer. The reader writes that the customer's email address stored at Hetzner has been changed. And a customer's AnyDesk computer had accessed links that were blocked by Bitdefender – and it was not the customer. As AnyDesk is also hosted by Hetzner, the reader suspects that there may be more going on. But that case is too weak, no smoking gun. The reader told me, that he checked the customer's system, it was malware free.
Addendum: AnyDesk has updated the FAQ on Feb. 7, 2024, and confirmed, that investigation has shown, dass the incident took place "late in December 2023".
Detailed recommendations from CERT-FR
In this comment, a German blog reader referred to the French CERT notification dated February 5, 2024. It states that the French ANSSI (CERT FR) was notified by the BSI on January 29, 2024 that the software manufacturer AnyDesk Software GmbH had been the victim of a data leak. The source code of the applications developed by the publisher as well as certificates and private keys may have been stolen.
According to the French company AnyDesk, the exfiltrated data could potentially be reused for further attacks on users of AnyDesk solutions.
- The French recommend identifying all systems that contain AnyDesk clients (mobile devices are explicitly mentioned).
- After this inventory, the results should be saved to facilitate possible future investigations.
- Managers should verify that AnyDesk clients have been installed as part of a legitimate, known and internally confirmed activity of the organization.
- Identifying the sensitivity of the machines, workstations and servers using these tools and the business constraints associated with their use is encouraged.
- Responsible parties should conduct a risk assessment to identify the impact that an incident scenario involving the potential compromise of one or more of these devices could have.
Based on your risk assessment and to anticipate potential future suspicions, conduct a digital investigation of all affected machines and seize them, it says. If this cannot be done globally, ANSSI recommends starting with the most critical machines. Then, depending on the risk assessment and business constraints, there are further recommendations.
- Consider uninstalling the AnyDesk solution and using an alternative solution.
- For Windows environments: Update the AnyDesk solution to version 8.0.8 (it is essential to download the update from the publisher's official website).
- Once the inventory is migrated to this new version, measures should be taken, as far as possible, to detect/block all applications signed with the listed philandro Software GmbH certificate.
These are much more far-reaching instructions than the BSI presents in its "warnings". The French CERT gives further instructions, including looking for connections to *.net.anydesk.com at network level. This indicates the presence of AnyDesk. And then there is the specific instruction to look for suspicious activity on the machines from 20.12.2023.
Uncertainty about the date of the attack
This brings us to the last point that is currently on my mind. An anonymous source mentioned to me a German CERT (BSI) notification that is not yet public and addresses the AnyDesk cyber incident that went public on February 2, 2024. The source told me, that the BSI document has a "mention" of December 20, 2023.
German site heise picked up that rumor on this article and quotes a BSI spokesperson as saying "The BSI cannot confirm any knowledge of the BSI since the end of December". I would have ticked this off now if I hadn't received the CERT FR document quoted above shortly afterwards, where exactly this December 20, 2023 is mentioned. This matches the rumors I've head from my sources.
Articles:
AnyDesk confirmed, they have been hacked in January 2024, Production systems affected – Part 1
AnyDesk hack undercover – more information and thoughts – Part 2
AnyDesk hack undercover – Suspicious cases and more – Part 3
AnyDesk hack undercover – Access data offered for sale – Part 4
AnyDesk hack – A review – Part 5
AnyDesk hack – Review of the German CERT BSI report – Part 6
AnyDesk hack – Notes on exchanging certificates for Customs clients 7.x – Part 7
AnyDesk hack – more details (FAQ from Feb. 5, 2024) – Part 8
AnyDesk hack already noticed on December 20, 2023? – Part 9
AnyDesk hack confirmed as of December 2023; old certificate recalled – Part 10
AnyDesk hack: Revoke chaos with old certificates? – Part 11
AnyDesk hack: Newly signed clients available; what are your experiences? – Part 12
Similar article:
Störung bei AnyDesk, jemand betroffen?
AnyDesk: Be careful in using that remote support software




So "mid january" has actually become AT LEAST december 20, 2023, it seems. And I suspect it's about november 9 or even earlier, based on the fact that the Philandro cert has been used to sign a malware that's found on virustotal, and that the sign date (that can be wrong, of course) is november 9 2023. Are they (Anydesk and the German CERT BSI) lying? Well, I'd that that maybe they are. Or at least they are not saying everything they know.
So are we safe to assume that no MITM has been performed, and no user data from Anydesk session has been exposed, and there is (or there has not been) no way for the threat actors to actually access customers system by means of Anydesk, if it was running unattended on customers computers?
NO, we can't be sure, if we have reasons not to completely trust Anydesk or the German BSI.